Volt Typhoon: International Cybersecurity Authorities Detail Activity Linked to Chinese-State Sponsored Threat Actor

Several international cybersecurity authorities from the United States, United Kingdom, Australia, Canada and New Zealand issue a joint advisory detailing tactics, techniques and procedures used in recent attacks by a Chinese state-sponsored threat actor.
Update May 26: The blog has been updated to include an update to the VPR score of CVE-2021-27860.
Background
On May 24, several international agencies — including the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI) and the National Security Agency (NSA) in the U.S, the Australian Cyber Security Centre (ACSC), the Communications Security Establishment’s Canadian Centre for Cyber Security (CCCS), the New Zealand National Cyber Security Centre (NCSC-NZ), and the United Kingdom National Cyber Security Centre (NCSC-UK) — issued a joint cybersecurity advisory (CSA), AA23-144a, about Volt Typhoon, a People’s Republic of China (PRC) state-sponsored threat actor. In addition to the joint CSA, Microsoft’s Threat Intelligence Team published a separate blog post that also highlights activity associated with Volt Typhoon.
Analysis
The following are some of the key points detailed in the joint cybersecurity advisory:
Where does the name “Volt Typhoon” come from?
It is part of a new naming convention used by Microsoft.
How long has Volt Typhoon been operating?
Reports suggest that the group has been active since “at least 2021.”
What are some of the geographical regions and industries targeted by Volt Typhoon?
In both the joint CSA and Microsoft’s blog post, Volt Typhoon has been observed targeting critical infrastructure organizations in the United States as well as the U.S. island territory of Guam.
What is notable about Volt Typhoon’s activity?
The threat actor has a strong focus on “stealth” activity by using what are known as living-off-the-land (LOTL) techniques and hands-on-keyboard activity.
LOTL techniques include the use of legitimate networking tools preloaded onto operating systems in order to mask their activities, such as certutil, ntdsutil, xcopy and more. Hands-on-keyboard, as its name implies, involves a human attacker manually executing commands on a compromised system with “hands-on-keyboard” instead of using automated or programmed tools. These techniques are employed by threat actors to evade detection by common security solutions, such as endpoint detection and response (EDR).
Volt Typhoon is known to primarily focus on espionage and information gathering and recent activity by the group has centered around critical infrastructure, prompting the joint CSA to warn defenders of the threat actor’s activity as well as their tactics, techniques, and procedures.
Does Volt Typhoon use any other techniques to hide their activity?
Yes, the CSA notes the group’s use of Small-Office-Home-Office (SOHO) devices as a source of obfuscation, such as a variety of devices from different vendors including:
- ASUS
- Cisco RV
- Draytek Vigor
- FatPipe IPVPN/MPVPN/WARP
- Fortinet Fortigate
- Netgear Prosafe
- Zyxel USG
The group uses these compromised SOHO devices to proxy network traffic in attempts to appear as legitimate network activity. While no information was provided about how these devices were compromised, we strongly recommend ensuring that any SOHO devices are kept up to date with the latest security patches.
Additionally, if these devices have been configured to publicly expose their management interfaces, follow the vendors’ recommendations on how to secure these configurations or disable external facing access to these devices where possible.
How does Volt Typhoon gain initial access to targeted organizations?
Exploitation of internet-facing assets, such as Fortinet Fortiguard devices, ManageEngine ADSelfService Plus and FatPipe’s WARP, IPVPN and MPVPN products.
Does Volt Typhoon exploit any known vulnerabilities?
Yes, the joint CSA highlights two vulnerabilities in ManageEngine and FatPipe products that have been linked to Volt Typhoon. The agencies note that the vulnerabilities exploited by the threat actor include but are not “limited to” the following:
| CVE | Description | CVSSv3 | VPR* |
|---|---|---|---|
| CVE-2021-40539 | ManageEngine ADSelfService Plus Authentication Bypass Vulnerability | 9.8 | 9.2 |
| CVE-2021-27860 | FatPipe WARP, IPVPN, MPVPN Unrestricted Upload of File with Dangerous Type | 8.8 | 9.2 |
*Please note: Tenable’s Vulnerability Priority Rating (VPR) scores are calculated nightly. This blog post was updated on May 26 and reflects VPR at that time.
Are there any other vulnerabilities used by Volt Typhoon?
While Microsoft’s blog post notes that Volt Typhoon targets Fortinet Fortiguard devices, no specific CVEs were mentioned. However, we know that Fortinet devices are a popular target for APT groups, including APT5, and there’s been some recent activity linking Chinese threat actors to multiple Fortinet flaws, such as CVE-2022-42475 and CVE-2022-41328. However, we cannot definitively connect these vulnerabilities to Volt Typhoon activity.
Historically, PRC state-sponsored threat actors have exploited known vulnerabilities for years at a time, as shown in similar, older advisories, identified as U/OO/179811-20 from 2020 and AA22-279A from 2022. For instance, CVE-2021-40539, noted earlier, is featured in AA22-279A. Additionally, a flash alert issued by the FBI in November 2021, AC-000155-MW, discussed a zero day vulnerability in FatPipe that was eventually assigned to CVE-2021-27860. In the flash alert, the FBI details its use by an APT actor dating back to “at least May 2021” along with the implantation of webshells on vulnerable devices.
As we outlined in our 2022 Threat Landscape Report, known and exploitable vulnerabilities continue to be favored by a variety of threat actors. Identifying and remediating vulnerabilities with readily available proof-of-concept (PoC) code should remain a top priority for every organization to reduce your exposure.
Does Volt Typhoon use any malware?
According to the Microsoft blog post, the group rarely uses malware, but appears to prefer relying on LOTL methods through the use of legitimate tools in an attempt to steal credentials as part of post-compromise activity.
Does Volt Typhoon target Active Directory?
Yes, the threat actor does make attempts to extract credentials from Active Directory (AD), as well as make a copy of the ntds.dit database. With a copy of ntds.dit, the threat actor can exfiltrate the database and use password cracking tools to compromise additional user accounts while remaining stealthy.
Proof of concept
Of the two vulnerabilities listed in the CSA, publicly available PoC exploit code exists for just CVE-2021-40539.
Identifying affected systems
A list of Tenable plugins to identify the two vulnerabilities highlighted in the CSA can be found here. This link uses a search filter to ensure that all matching plugin coverage will appear as it is released. We also recommend scanning for and remediating these top 20 CVEs known to be exploited by threat actors associated with the PRC.
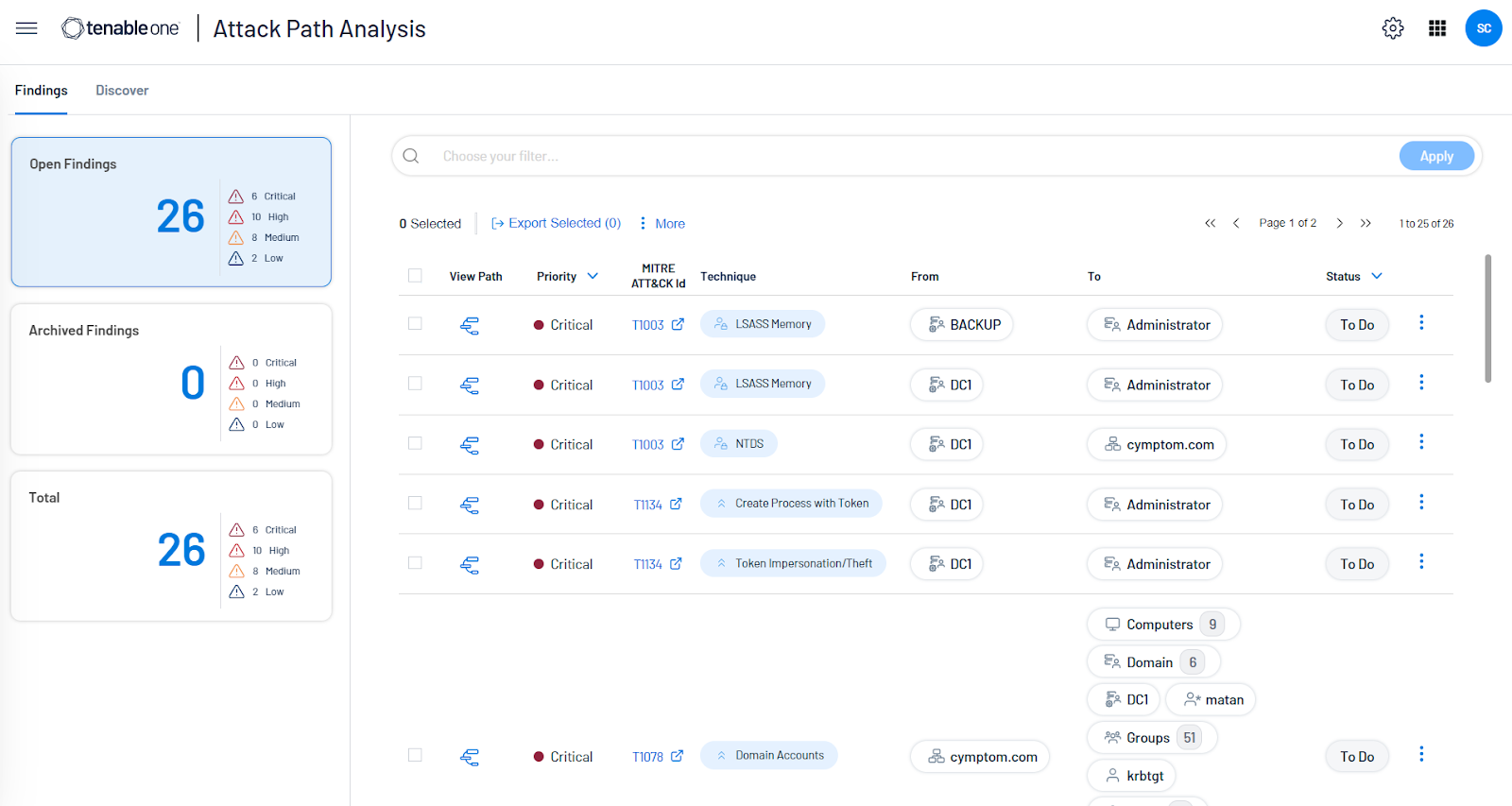
The following is a list of MITRE ATT&CK Techniques associated with Volt Typhoon mapped to the Tenable Identity Exposure Indicators of Attack (IOA) as well as the associated Attack Path Analysis Techniques:
| Technique ID | Description | Indicators of Attack | Attack Path Technique |
|---|---|---|---|
| T1003.001 | OS Credential Dumping: LSASS Memory | I-ProcessInjectionLsass | T1003.001_Windows |
| T1003.003 | OS Credential Dumping | I-NtdsExtraction | T1003.003_Windows |
| T1047 | Windows Management Instrumentation | N/A | T1047_Windows |
| T1059.001 | Command and Scripting Interpreter: PowerShell (Windows) | N/A | T1059.001_Windows |
| T1069.001 | Permission Groups Discovery: Local Groups | I-ReconAdminsEnum | T1069.001_Windows |
| T1069.002 | Permission Groups Discovery: Domain Groups | N/A | T1069.002_Windows |
| T1110.003 | Brute Force: Password Spraying (Windows) | I-PasswordSpraying | T1110.003_Windows |
As both Microsoft and the joint CSA point out, Volt Typhoon has been known to target and exploit internet-facing assets for initial compromise of networks. The external attack surface represents one of the greatest risk factors to organizations today. To minimize the risk of breach, it is essential that organizations fully understand their external attack surface and the opportunities for exploitation that are presented there. Tenable Attack Surface Management (formerly Tenable.asm) provides comprehensive visibility into all of your internet-connected assets, helping you to better assess and manage external risk.
Additionally, the joint CSA strongly recommends following best practices for identifying and addressing AD weaknesses and misconfigurations. To aid in these efforts, Tenable Identity Exposure (formerly Tenable.ad) can be utilized to reduce your exposure and find and fix flaws before they become business-impacting issues.
Get more information
- Joint Cybersecurity Advisory AA23-144a
- Microsoft Threat Intelligence blog post on Volt Typhoon
- Blog for Tenable’s 2022 Threat Landscape Report
- Top 20 CVEs Exploited by People's Republic of China State-Sponsored Actors (AA22-279A)
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management

