Simplify Azure cloud security with Tenable
Get comprehensive Azure cloud visibility from build to runtime
Secure your entire development lifecycle, boost your team's Microsoft Azure security expertise and accelerate collaboration across cloud, development and identity and access management (IAM) teams with Tenable Cloud Security.

"We’re just two clicks away from seeing what is really going on in our Azure cloud —
that’s value for us."
Business Solution Lead, Industrial Services Provider
Decrease exposures across Azure and multi-cloud environments
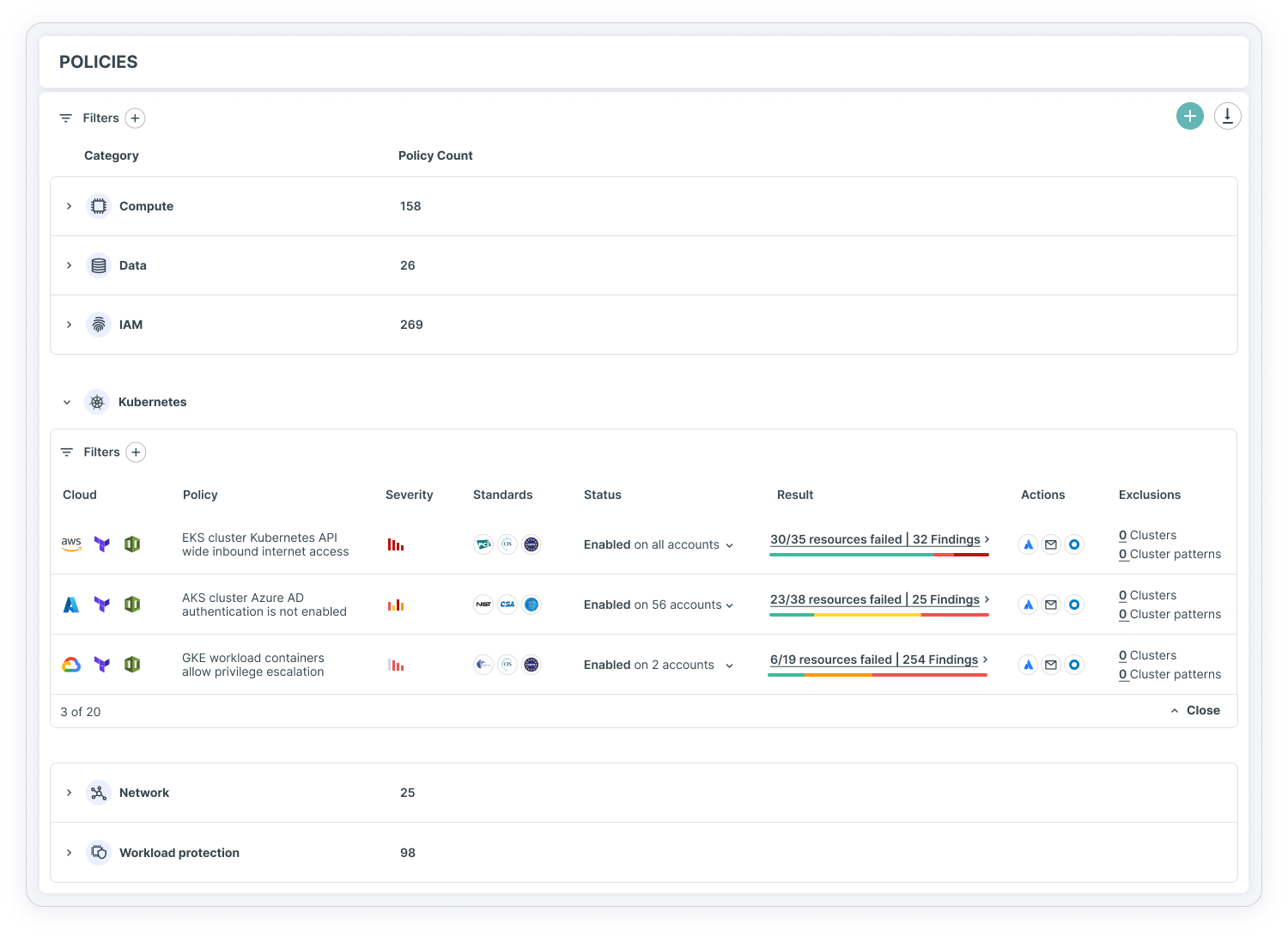
Bridge security gaps with in-depth understanding of Azure architecture
Tenable Cloud Security applies an automated, identity-first holistic approach to empower your teams with accurate risk detection, guided remediation and least privilege at scale. Assess the risk of Azure resources by discovering vulnerabilities and prioritizing them in context with your entire multi-cloud and hybrid environment.
Harden cloud applications with Azure integrations
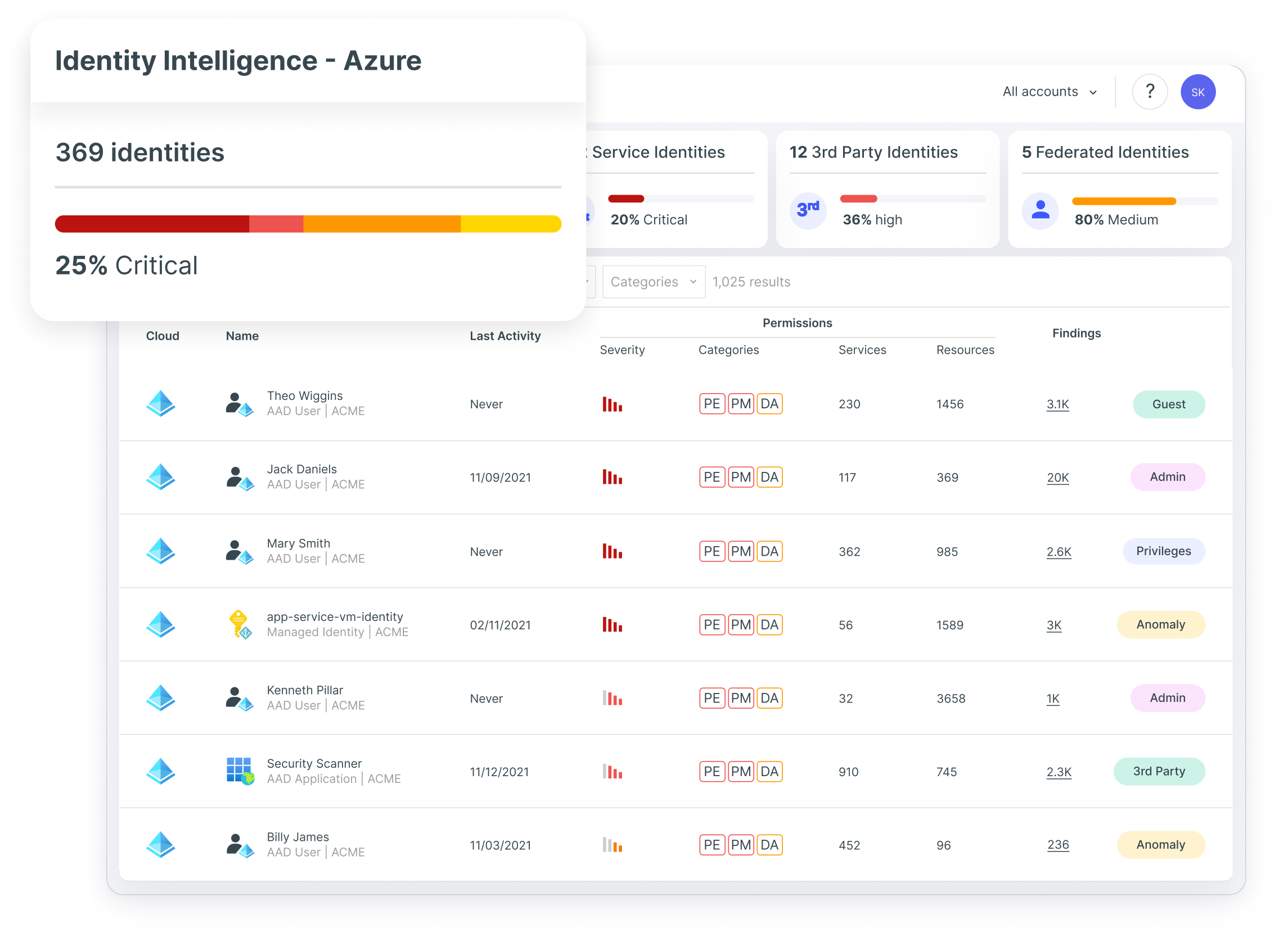
Tenable supports security team efforts to harden cloud applications in Azure environments by effectively addressing critical infrastructure as a service (IaaS) risks such as misconfigured identities, access and privileges. By integrating with native features like Entra ID and Azure Pipelines to secure the identity and access management (IAM) lifecycle, you can reduce your Azure and multi-cloud attack surface through pinpointed visualization, accurate prioritization and guided remediation.
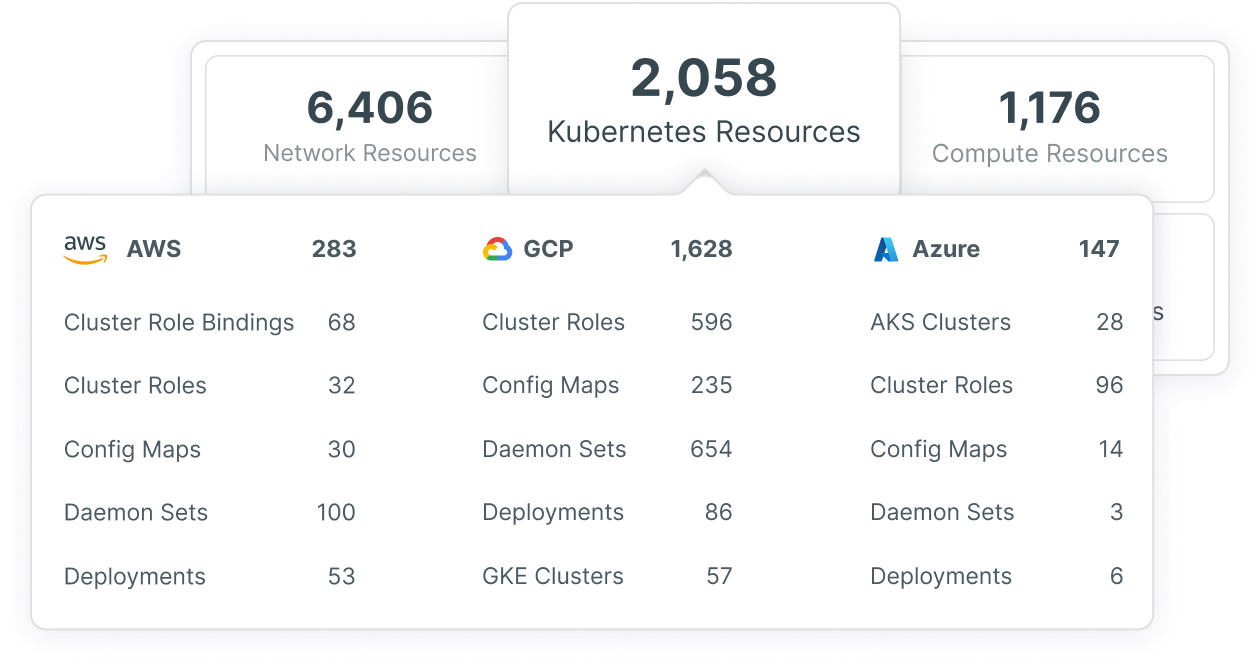
Fortify AKS clusters across all environment
View the status, configuration and risk of your Azure Kubernetes clusters. Through dynamic risk assessment, get insight into which clusters require immediate remediation and which team is responsible for the fix.
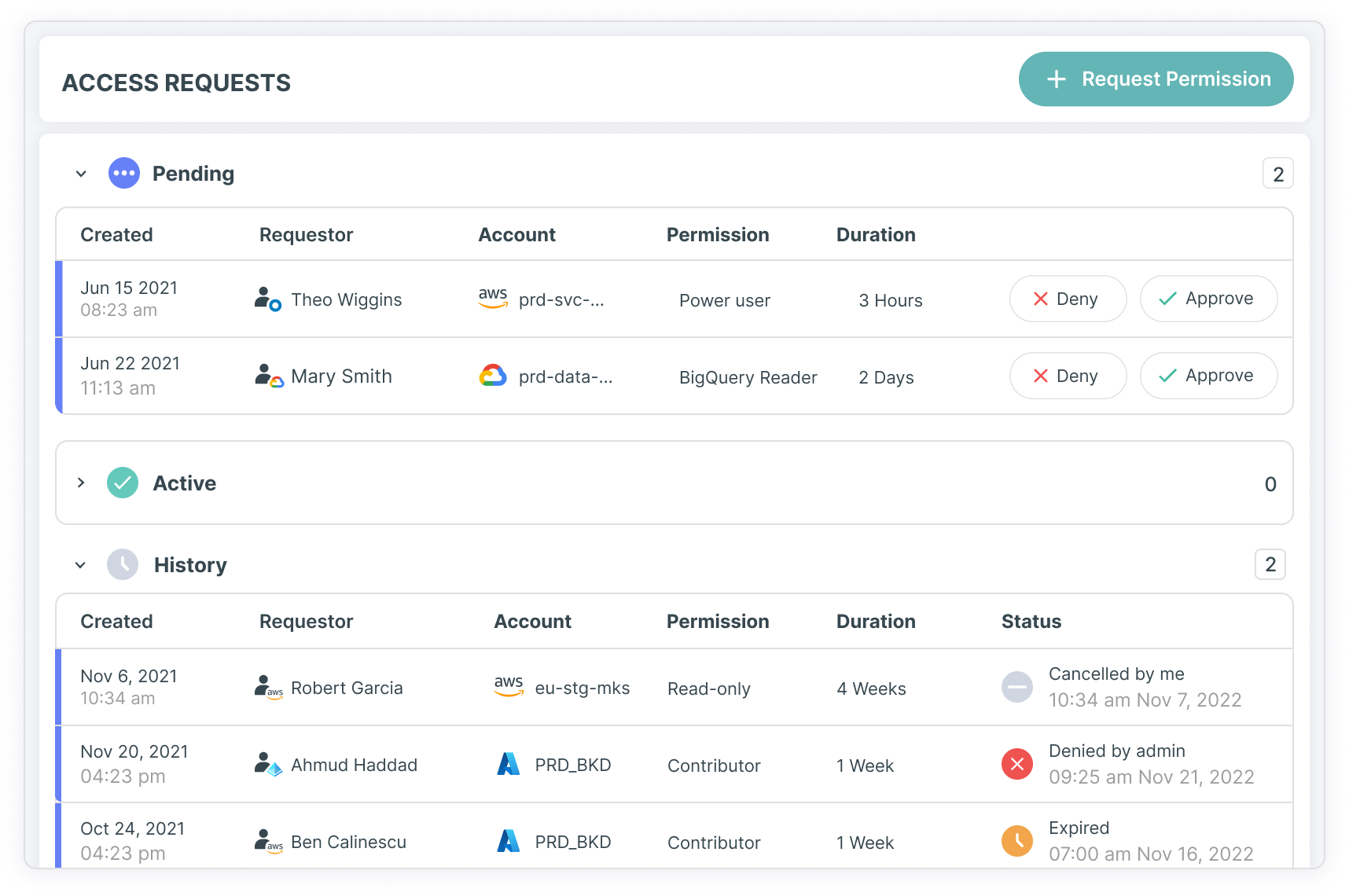
Generate least privilege roles and automate access
Simplify least privilege in Azure with Tenable's Just-in-Time (JIT) portal. Give your team a simplified approval process to ensure the right people have the right access — and for just the right amount of time. You can also automatically generate customized roles based on observed activity for service or machine identities in Azure to grant minimum privileges needed.
深入瞭解 Tenable Cloud Security
使用 [Tenable Cloud Security] 的自動化功能,讓我們免除了讓人筋疲力竭的手動流程,並且在幾分鐘內執行過去可能需要 2 或 3 位安全人員好幾個月時間才能完成的工作。
- Tenable Cloud Security