識別受 Cisco ASA 關鍵弱點 (CVE-2018-0101) 影響的系統

On January 29, Cisco released an advisory for a critical vulnerability in their Adaptive Security Appliance (ASA) software. The critical flaw, assigned CVE-2018-0101, has a CVSS score of 10.0 and could allow for a denial-of-service attack and remote code execution. On February 5, Cisco updated the advisory indicating they’d found additional attack vectors and more affected products. They also determined the original fix was incomplete. Early adopters of the patch will need to revisit the advisory and apply the latest update to their devices.
Vulnerability details
The vulnerability was originally found by NCC Group and has since been presented at REcon Brussels. The slides have been made available and the details of the vulnerability are now widely available. A denial-of-service proof of concept has already been published to Pastebin as well.
The vulnerability is reportedly a seven-year-old flaw within a Cisco XML parser. Using a crafted XML payload, a remote, unauthenticated attacker could cause a reload on an affected device or potentially execute arbitrary code. The original exploit, as written by NCC Group, uses IKEv1 fragmentation to leverage the XML vulnerability into code execution. As such, the additional interfaces added in the February 5, 2018, update (ASDM, CSM, Cut-Through Proxy, Local CA, MDM Proxy, and REST API) may only be vulnerable to denial-of-service attacks.
找出受影響的系統
Tenable has released Nessus® plugins manageable via Security Center or Tenable.io to detect systems affected by this critical flaw. The following table summarizes Tenable's coverage. Cisco has updated the advisory several times since the initial release to update the affected vectors as well as to make corrections to the patch versions. Tenable continues to monitor this situation and update our coverage as necessary.
|
Plugin ID |
Description |
|
106484 |
Cisco ASA Remote Code Execution and Denial of Service Vulnerability (cisco-sa-20180129-asa1) |
|
106630 |
Cisco Firepower Threat Defense (FTD) Adaptive Security Appliance Remote Code Execution and Denial of Service Vulnerability (cisco-sa-20180129-asa1) |
|
107004 |
Cisco ASA Remote Code Execution and Denial-of-Service Vulnerability (cisco-sa-20180129-asa1) (destructive check) |
請注意:Plugin ID 107004 will directly exploit the Denial-of-Service (DoS) vulnerability. However, this check will only run if you have disabled "safe checks" in your scan policy (see below). Disabling "safe checks" should be reserved for non-production environments, as this will allow DoS checks, such as plugin ID 107004, to execute, potentially crashing a system.
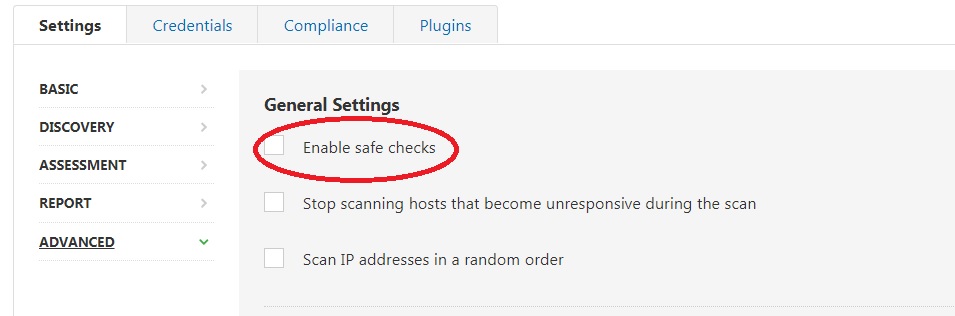
What should you do?
If you’re running affected devices on your network, make sure you’re running the most current software release. Cisco notes in their advisory that customers should regularly review their security advisories to ensure they’re current and up-to-date on any new patches or software releases.
取得更多資訊
- Learn more about Tenable.io, the first Cyber Exposure platform for holistic management of your modern attack surface
- Get a free 60-day trial of Tenable.io Vulnerability Management
- Cisco cisco-sa-20180129-asa1Advisory
- Cisco Blog on CVE-2018-0101
- NCC Research
Thanks to Jacob Baines for his contributions to this blog post.
- Plugins


