CVE-2024-5806: Progress MOVEit Transfer Authentication Bypass Vulnerability

Progress Software has patched a high severity authentication bypass in the MOVEit managed file transfer (MFT) solution. As MOVEit has been a popular target for ransomware gangs and other threat actors, we strongly recommend prioritizing patching of this vulnerability.
Update June 26: The Analysis section has been updated to include information about exploitation attempts.
Background
On June 25, Progress published an advisory for a vulnerability in MOVEit Transfer, a secure managed file transfer (MFT) solution:
| CVE | Description | CVSSv3 |
|---|---|---|
| CVE-2024-5806 | MOVEit Transfer Authentication Bypass Vulnerability | 7.4 |
Analysis
CVE-2024-5806 is an authentication bypass vulnerability affecting the SSH File Transfer Protocol (SFTP) module in Progress MOVEit Transfer. According to the advisory, this vulnerability is only exploitable in “limited scenarios,” however no further information was available on what those scenarios may be. A technical analysis of this vulnerability by researchers at watchTowr provides more analysis on how they recreated the vulnerability and we recommend reviewing their blog post for additional insight and indicators of compromise (IoCs) for defenders.
Past Exploitation of MOVEit Transfer
On May 27, 2023, the ransomware group known as CLOP (or TA505) began mass exploitation of MOVEit Transfer MFT’s by exploiting a then zero-day SQL injection vulnerability (CVE-2023-34362). Hundreds of organizations were impacted by these attacks, with data breach reports tallying millions of affected individuals in the weeks and months after the attacks were identified and disclosed. With MFTs offering a treasure trove of sensitive information, opportunistic attackers have targeted them in order to steal sensitive data and extort victims. Additional MFT related attacks by the nefarious Cl0p ransomware group also include the exploitation of Accellion’s File Transfer Appliance (FTA) in 2020 and Fortra’s GoAnywhere MFT in January 2023.
The attacks by Cl0p gained attention from The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) who issued a joint cybersecurity advisory for CVE-2023-34362 (AA23-158A) on June 7, 2023 as part of their #StopRansowmare campaign.
Given the mass exploitation of MOVEit Transfer in the past, we highly recommend taking action to patch this vulnerability as soon as possible.
Exploitation attempts have been observed
In a post on X (formerly Twitter), The Shadowserver Foundation noted that they began seeing exploitation attempts shortly after details emerged for CVE-2024-5806.
Very shortly after vulnerability details were published today we started observing Progress MOVEit Transfer CVE-2024-5806 POST /guestaccess.aspx exploit attempts. If you run MOVEit & have not patched yet - please do so now: https://t.co/AenLgqg1wM
NVD: https://t.co/OHQRNFNE9p— The Shadowserver Foundation (@Shadowserver) June 25, 2024
Proof of concept
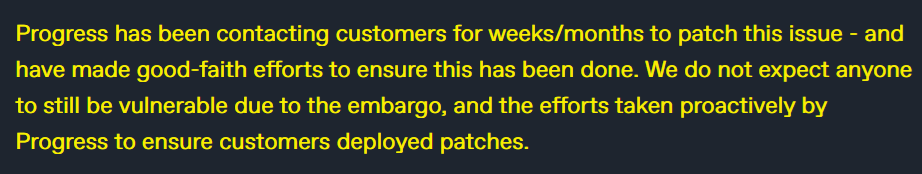
On June 25, researchers at watchTowr published a detailed technical writeup alongside exploit code that demonstrates this vulnerability. According to watchTowr, there are some barriers for exploitation, such as the attacker needing to know a valid username on the system and being able to bypass any IP-based restrictions that an organization may have in place. watchTowr notes that Progress has made many attempts, under embargo, to contact affected customers in order to ensure they had adequate time to apply patches prior to the security advisory being made public.
Credit: watchTowr blog
Solution
Progress has released fixed versions of MOVEit Transfer. The following table reflects the affected and patched versions:
| Affected Versions | Patched Version |
|---|---|
| 2023.0.0 before 2023.0.11 | 2023.0.11 |
| 2023.1.0 before 2023.1.6 | 2023.1.6 |
| 2024.0.0 before 2024.0.2 | 2024.0.2 |
According to the advisory from Progress, customers using MOVEit Cloud environments have already been patched and are not “vulnerable to this exploit.”
Identifying affected systems
A list of Tenable plugins for this vulnerability can be found on the individual CVE page for CVE-2024-5806 as they’re released. This link will display all available plugins for this vulnerability, including upcoming plugins in our Plugins Pipeline.
Change Log
Update June 26: The Analysis section has been updated to include information about exploitation attempts.
Get more information
- Security Advisory: MOVEit Transfer Product Security Alert Bulletin for CVE-2024-5806
- watchTowr Blog: Auth. Bypass In (Un)Limited Scenarios - Progress MOVEit Transfer (CVE-2024-5806)
- Tenable Blog: CVE-2023-34362: MOVEIt Transfer Critical Zero-Day Vulnerability Exploited in the Wild
- Tenable Blog: FAQ for MOVEit Transfer Vulnerabilities and CL0P Ransomware Gang
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management

