CVE-2023-34362: MOVEIt Transfer Critical Zero-Day Vulnerability Exploited in the Wild

Discovery of a new zero-day vulnerability in MOVEit Transfer becomes the second zero-day disclosed in a managed file transfer solution in 2023, with reports suggesting that threat actors have stolen data from a number of organizations.
Update June 15: The Tenable Security Response Team is aware of an additional SQL injection vulnerability in Progress MOVEit Transfer. At this time, there is no patch available. Please refer to Progress Software's latest advisory for more information. We will provide an update once more information becomes available.
Background
On May 31, Progress Software Corporation (“Progress Software”), published an advisory for a “critical” vulnerability in MOVEit Transfer, a secure managed file transfer (MFT) software used by a variety of organizations. Following the publication of its advisory, reports have emerged that the flaw had been exploited in the wild as a zero-day.
| CVE | Description | CVSSv3 | VPR* |
|---|---|---|---|
| CVE-2023-34362 | Progress MOVEit Transfer SQL Injection Vulnerability | 9.8 | 9.2 |
*Please note: Tenable’s Vulnerability Priority Rating (VPR) scores are calculated nightly. This blog post was updated on June 9 and reflects VPR at that time.
On June 9, Progress Software published a new advisory for additional SQL injection vulnerabilities that were discovered as part of a security audit conducted after the discovery of CVE-2023-34362.
| CVE | Description | CVSSv3 | VPR* |
|---|---|---|---|
| CVE-2023-35036 | Progress MOVEit Transfer SQL Injection Vulnerabilities | N/A | N/A |
Analysis
CVE-2023-34362 is a SQL injection vulnerability in the MOVEit Transfer web application. An unauthenticated, remote attacker could exploit this vulnerability by sending a specially crafted request to a vulnerable MOVEit Transfer instance. Successful exploitation would give an attacker access to the underlying MOVEit Transfer instance. Additionally, Progress Software notes that an attacker “may be able to infer information about the structure and contents of the database” depending upon the specific database engine in use (such as MySQL, Microsoft SQL Server, or Azure SQL).
In addition to the on-prem version of MOVEit Transfer, Progress Software confirmed in a statement to BleepingComputer that MOVEit cloud was also impacted, adding that it “took immediate action, including bringing down MOVEit Cloud, to ensure the safety of our customers, while we reviewed the severity of the situation.”
Critical MOVEit vulnerability has been exploited in the wild as a zero-day
While Progress Software has not explicitly referred to it as a zero-day, BleepingComputer reports that they have learned that “threat actors have been exploiting” the flaw as a zero-day to “perform mass downloading of data from organizations.” At the time this blog post was published, we are unaware of any specific threat actor that is responsible for the attacks. However, since publication, the Clop ransomware group has claimed responsibility for the attacks.
Clop claims it downloaded “lots of data” and U.S. agencies issued cybersecurity advisory
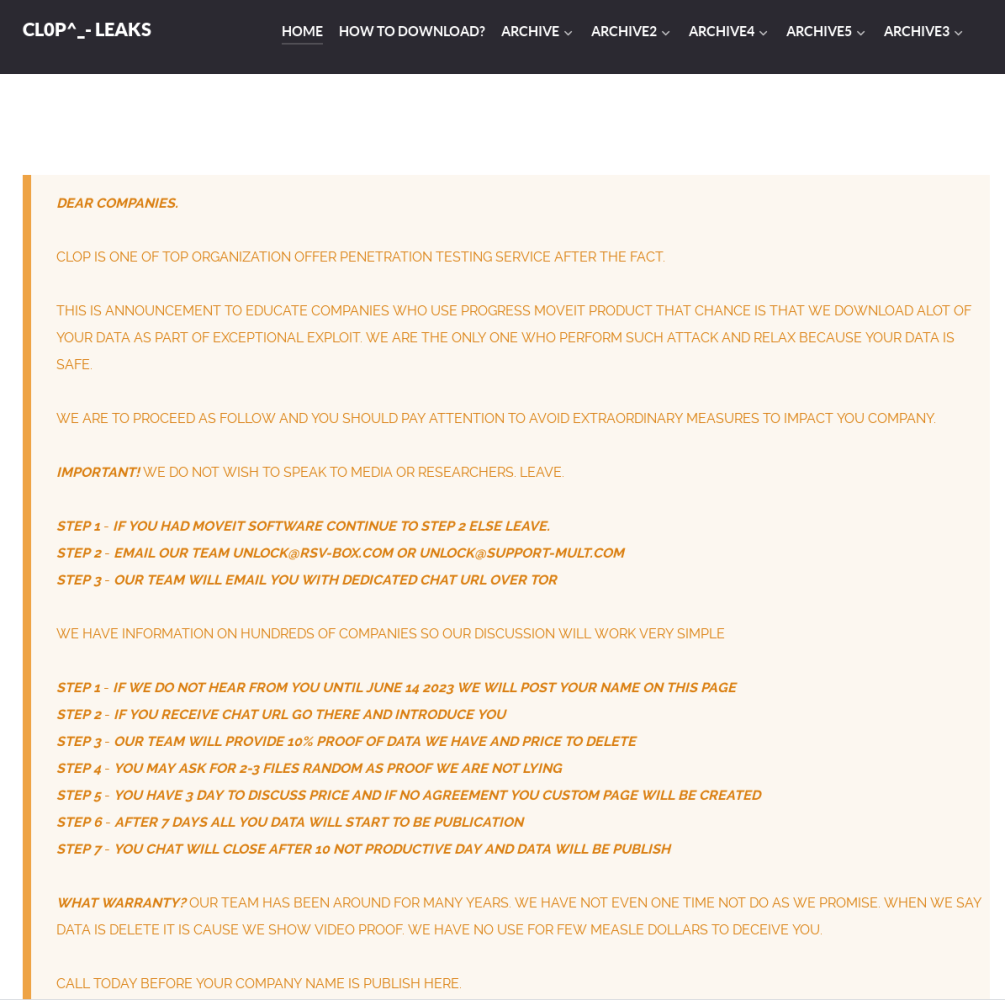 Image Source: Tenable, June 2023
Image Source: Tenable, June 2023
In a notice on its data leak site, Clop states they were able to “download alot of” data using the “exceptional exploit,” adding that they are the “only one who perform (sic) such attack (sic).” Instead of contacting or naming the victims beforehand, Clop has instructed potentially affected companies to “call” them before their “company name is publish (sic) here.” The group plans to publish the names of victim organizations on June 14.
The note also includes a message to specific entities, such as governments, cities or police services, claiming the group “erased all” data associated with these entities, adding that they have “no interest to expose such information.”
 Image Source: Tenable, June 2023
Image Source: Tenable, June 2023
Additionally, the Federal Bureau of Investigation (FBI) and Cybersecurity and Infrastructure Security Agency (CISA) published a joint cybersecurity advisory (CSA) on June 7 about the Clop ransomware group. In it, both agencies confirmed the attribution of the MOVEit attacks to the Clop ransomware group. Additionally, the CSA includes details about the tactics, techniques, and procedures (TTPs) associated with the Clop ransomware group.
At least 2,500 MOVEit Transfer potentially vulnerable instances publicly accessible
Based on a Shodan query from Shodan itself, there were 2,526 MOVEit Transfer potentially vulnerable instances publicly accessible as of June 2, 2023, with nearly three-quarters originating in the United States (73.4%) followed by the United Kingdom at 5% and Germany at 4.6%.
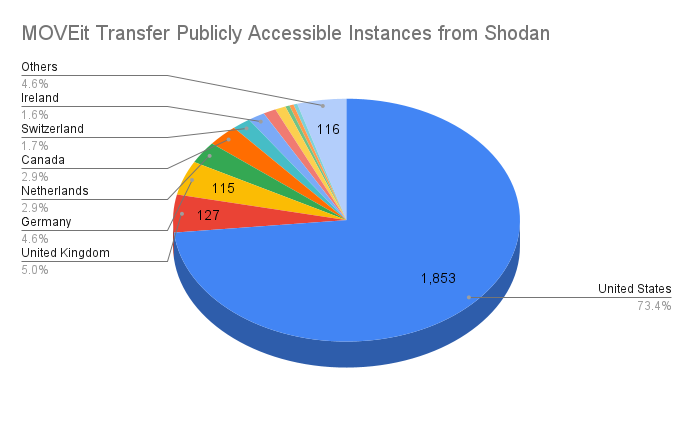
Image Source: Tenable, June 2023
Second MFT zero-day vulnerability discovered in 2023
The discovery of CVE-2023-34362 in MOVEit marks the second time in 2023 that a zero-day in an MFT solution has been exploited. In February, Fortra (formerly HelpSystems), disclosed a pre-authentication command injection zero-day vulnerability in its GoAnywhere MFT solution to customers as part of a technical bulletin as shared by journalist Brian Krebs. Identified as CVE-2023-0669, Fortra confirmed that GoAnywhere customers’ systems were accessed between January 28 and January 30 using the flaw as part of its summary investigation. The Clop ransomware group took credit for the attacks, claiming it had stolen data from “over 130 organizations.” Additionally, the BlackCat/ALPHV ransomware group was also observed exploiting CVE-2023-0669.
File transfer applications are a boon for data theft and extortion
Preceding the discovery of CVE-2023-0669, the Clop ransomware group was linked to a number of attacks stemming from four flaws in Accellion’s File Transfer Appliance (FTA), an end-of-life solution that was exploited in mid-to-late December 2020.
File transfer solutions are uniquely positioned as a valuable target for cybercriminals, particularly ransomware groups. While the rise in ransomware attacks over the last five years is largely attributed to the adoption of double-extortion, a technique that involves both data encryption as well as data theft and threatening to publish the stolen data on data leak sites, new groups have emerged foregoing data encryption altogether or existing groups have pivoted away from it, opting to focus on data theft.
The compromise of MFT solutions by threat actors creates a snowball-like effect, as in the coming days and weeks ahead, we’ll likely learn which organizations were impacted by this flaw, either through ransomware data leak sites or breach disclosures from affected organizations.
MOVEit Transfer customers should assume compromise; initiate incident response
As this vulnerability was exploited as a zero-day, MOVEit Transfer customers should view this as a suspected compromise and start the incident response (IR) process. The advisory from Progress Software includes a list of indicators of compromise (IOCs), including a webshell named “human2.aspx” and “human2.aspx.lnk” along with a list of command and control traffic signals that can be used as part of an IR investigation.
For additional technical analysis, please refer to several blog posts that have been published [1, 2, 3] since the advisory was released. Additionally, our partners at GreyNoise have recommended reviewing systems for IOCs dating back to at least 90 days prior to the public disclosure of this flaw.
Proof of concept
At the time this blog post was published, there was no proof-of-concept (PoC) exploit for CVE-2023-34362.
Solution
Progress Software has released the following fixed versions of MOVEit Transfer on-prem for CVE-2023-34362:
| Fixed MOVEit Transfer Version for CVE-2023-34362 |
|---|
| 2021.0.6 |
| 2021.1.4 |
| 2022.0.4 |
| 2022.1.5 |
| 2023.0.1 |
If upgrading to a fixed version is not feasible at this time, Progress Software recommends disabling HTTP (port 80) and HTTPS traffic (port 443) to MOVEit Transfer in the interim in order to prevent exploitation.
For CVE-2023-35036, which was disclosed on June 9, Progress Software released the following fixed versions of MOVEit Transfer on-prem:
| Fixed MOVEit Transfer Version for CVE-2023-35036 |
|---|
| 2021.0.7 |
| 2021.1.5 |
| 2022.0.5 |
| 2022.1.6 |
| 2023.0.2 |
A special patch is available for MOVEit Transfer 2020.1.x (12.1), while users of MOVEit Transfer 2020.0.x (12.0) or older are instructed to upgrade to a supported version.
Identifying affected systems
This section was updated on June 9.
Our detection plugin for Progress MOVEit Transfer has been updated and an additional version check plugin (ID: 177082) has been created. Both updated plugins should be available to customers shortly.
| Plugin ID | Title | Type | CVE |
|---|---|---|---|
| 90190 | "Progress MOVEit Transfer Installed (Windows)" | Detection | - |
| 176567 | "Progress MOVEit Transfer < 2021.0.6 / 2021.1.0 < 2021.1.4 / 2022.0.0 < 2022.0.4 / 2022.1.0 < 2022.1.5 / 2023.0.0 < 2023.0.1 Critical Vulnerability (May 2023)" | Version | CVE-2023-34362 |
| 177082 | "Progress MOVEit Transfer < 2020.1.9 / 2021.0.x < 2021.0.7 / 2021.1.x < 2021.1.5 / 2022.0.x < 2022.0.5 / 2022.1.x < 2022.1.6 / 2023.0.x < 2023.0.2 Critical Vulnerability (June 2023)" | Version | CVE-2023-35036 |
Get more information
- Progress Advisory: MOVEit Transfer Critical Vulnerability
- Article: New MOVEit Transfer zero-day mass-exploited in data theft attacks
- Blog: Progress’ MOVEit Transfer Critical Vulnerability
- Blog: MOVEit Transfer Critical Vulnerability Rapid Response
- Blog: CRITICAL VULNERABILITY IN PROGRESS MOVEIT TRANSFER: TECHNICAL ANALYSIS AND RECOMMENDATIONS
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
Change Log
Update June 15: The Tenable Security Response Team is aware of an additional SQL injection vulnerability in Progress MOVEit Transfer. At this time, there is no patch available. Please refer to Progress Software's latest advisory for more information. We will provide an update once more information becomes available.
Update June 12: This blog post has been updated to reflect the assignment of CVE-2023-35036 for additional SQL injection vulnerabilities disclosed to Progress Software on June 9.
Update June 9: Updated the Background section with information on a new SQL injection vulnerability in MOVEit Transfer disclosed on June 9 (CVE-Pending), the Analysis section to include attribution of the attack to the Clop ransomware group and the publication of a joint cybersecurity advisory from the FBI and CISA, and the Identifying Affected Systems section to highlight the updated detection plugin and new version check plugin for the new vulnerability.
- Exposure Management
- Vulnerability Management



