CVE-2019-0604:Critical Microsoft SharePoint Remote Code Execution Flaw Actively Exploited

The SharePoint flaw first exploited in the wild in May continues to be exploited nine months after it was patched by Microsoft.
背景說明
On December 10, security researcher Kevin Beaumont published a tweet cautioning organizations to patch a Microsoft SharePoint flaw that’s been actively exploited in the wild since at least May, and has since remained a valuable asset to cybercriminals.
A reminder that all organisations should be patching SharePoint vulnerability CVE-2019-0604 (from February) as significant numbers of assets remain exposed, and the vulnerability is actively exploited in the wild.
— Kevin Beaumont (@GossiTheDog) December 10, 2019
分析
CVE-2019-0604 is a remote code execution (RCE) vulnerability in Microsoft SharePoint due to improper input validation in checking the source markup of an application package. Successful exploitation of the vulnerability by an attacker would grant them arbitrary code execution “in the context of the SharePoint application pool and the SharePoint server farm account.” The vulnerability was reported by security researcher Markus Wulftange, who shared a detailed write-up on his discovery in a blog for the Zero Day Initiative on March 13.
On May 9, security researcher Chris Doman published a tweet stating the flaw was being exploited in the wild based on reports from the National Cyber Security Centre in Saudi Arabia and the Canadian Centre for Cyber Security.
SharePoint CVE-2019-0604 now being exploited in the wild - reports by Saudi (https://t.co/m6VmF7n2Js) and Canadian (https://t.co/yhzY8qgxi8) National Cyber-Security Centres. Some additional IOCs @ https://t.co/gsGOoh6h9r pic.twitter.com/70LQCOmuTn
— chris doman (@chrisdoman) May 9, 2019
On May 28, Palo Alto Networks published a blog identifying the use of this vulnerability in the wild in targeted attacks by a threat actor known as Emissary Panda.
Additionally, CloudFlare published a blog about the vulnerability on May 28. CloudFlare confirmed the flaw could be exploited pre-authentication because “there were paths which could be reached without authentication.” As a result, they disputed the NVD score of 8.8 for the vulnerability, recommending it receive a 9.8 instead. They also found that proof-of-concept (PoC) code for the vulnerability “did not work out of the box,” requiring “weaponisation by a more skilled adversary.”
On November 25, Beaumont modified his BlueKeep honeypots, “BluePot,” to support SharePoint. One day later, Beaumont confirmed “the attackers arrived.” He reiterated the CVSS score for the vulnerability was wrong and should be a 9.8 because “it works without authentication.” He issued an additional reminder on December 10 because the flaw is still being exploited in the wild and a “significant numbers of assets remain exposed.”
概念驗證
Initially, there was a GitHub repository published containing PoC code for the vulnerability in May. However, that repository has since been removed. There is another PoC for the vulnerability that was published to a GitHub repository back in June and a write-up detailing the use of this PoC was published to GitHub in the last few days.
In September, security analyst Mansour Al-Saeedi published his analysis of the vulnerability based on the initial work by the Zero Day Initiative, demoing a quick PoC. Al-Saeedi also published a packet capture analysis of the RCE exploit being carried out along with Snort and Sigma rules to detect it to his GitHub repository.
解決方法
Microsoft initially patched the vulnerability on February 12 during Patch Tuesday. However, that patch was apparently incomplete, as Microsoft issued a follow-up release on March 12 to “comprehensively address” the flaw.
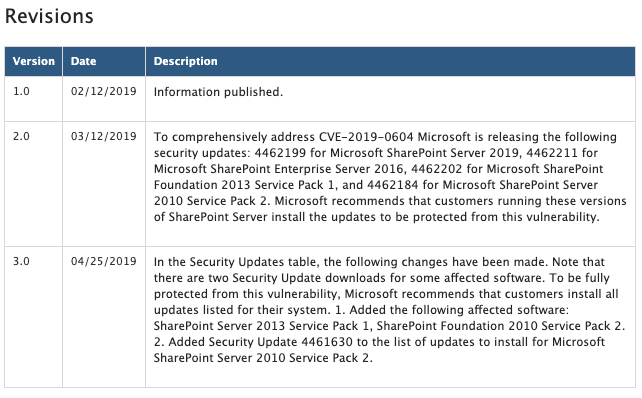
找出受影響的系統
A list of Tenable plugins to identify this vulnerability can be found here.
取得更多資訊
- Microsoft Advisory for CVE-2019-0604
- Detailed Write-Up for CVE-2019-0604 by Markus Wulftange
- Palo Alto Networks Blog on Exploitation of CVE-2019-0604 by Emissary Panda
- Cloudflare Blog on Stopping CVE-2019-0604
- Mansour Al-Saeedi’s Analysis of CVE-2019-0604
加入 Tenable Community 的 Tenable 安全回應團隊。
深入瞭解 Tenable,這是用於全面管理新型攻擊破綻的首創 Cyber Exposure 平台。
索取 Tenable.io Vulnerability Management 的 30 天免費試用。
- Vulnerability Management



