Who Owns Threat and Exposure Management in Your Organization?

A study conducted by Enterprise Strategy Group, now part of Omdia, in partnership with Tenable shows responsibility for exposure management scattered across multiple teams with conflicting priorities. It’s time to build the team of the future — discover what ‘good’ looks like and how to get there.
Key takeaways
- Teams are fragmented, with most organizations lacking a dedicated vulnerability or exposure management team.
- Conflicting priorities slow progress as IT and security teams often have different KPIs, causing delays.
- Success requires collaboration, bringing key security functions under one umbrella and fostering cooperation across teams, not just tools.
- Start small and build momentum by proving value with one team, unit, or use case before expanding.
- Leverage existing resources, using an exposure management platform to maximize your people and tools.
Do you know who owns threat and exposure management in your organization?
It’s not a trick question. The obvious answer that springs to mind would be, “the vulnerability or exposure management team, of course!”
Yet, a recent study conducted by Enterprise Strategy Group in partnership with Tenable shows that for most organizations the responsibility for threat and exposure management spans multiple teams — dominated by IT operations, cloud security and the security operations center (SOC). Only 41% of organizations say the vulnerability or exposure management team is responsible for managing threats and exposures

Why is this the case? For many organizations, such a team simply doesn’t exist. According to the study, “The Evolution of Risk Reduction: Contextual Analysis and Automated Remediation in Threat and Exposure Management,” many organizations lack the available expertise to staff dedicated vulnerability or exposure management teams. So, responsibility falls to members of the IT, cloud and SOC teams instead.
But these three domains have very different priorities and are measured on different KPIs. IT is primarily responsible for system uptime and keeping things operational, while security teams are primarily responsible for preventing exposure and reducing business risk. This creates conflicts when security teams need their IT counterparts to remediate urgent threats — ultimately slowing risk reduction and increasing exposure.
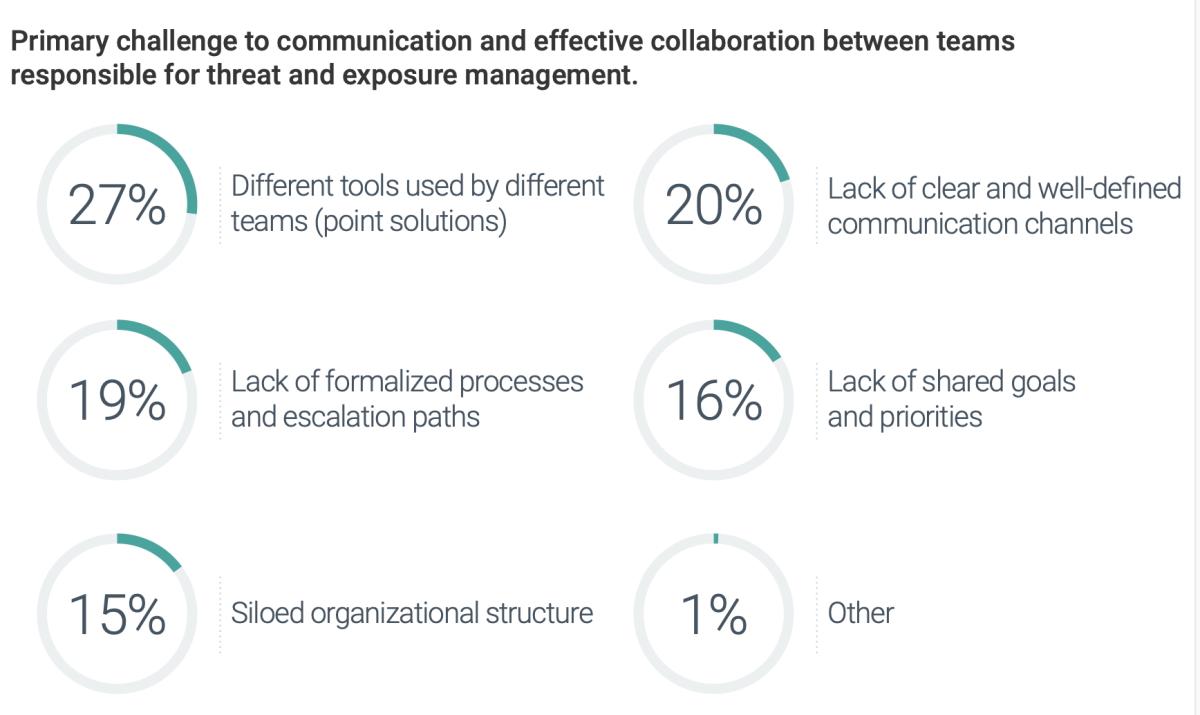
Siloed security tools, poor communication channels and a lack of formalized processes create friction and make effective cross-functional collaboration nearly impossible.
It’s time for organizations to rethink their approach.
As Tenable CSO Robert Huber shared in a past blog, we transformed our own vulnerability management policy into an exposure management policy. “More than just a name change, it represented a fundamental shift in scope for our vulnerability management team, which transformed into the exposure management team,” Huber wrote. “That team manages and owns the collaboration and workflows with the lines of business teams that need to fix issues.”
Transforming Tenable's vulnerability management policy into an exposure management policy is “more than just a name change, it represents a fundamental shift in scope for our vulnerability management team, which transformed into the exposure management team. That team manages and owns the collaboration and workflows with the lines of business teams that need to fix issues.”
Huber noted that specialized teams like cloud security and application security still exist, but instead of chasing down colleagues to fix specific issues they can now concentrate on their core business functions, like securely deploying infrastructure in new environments.
How to create the exposure management team of the future
So, what does the ideal threat and exposure management team look like? According to the Enterprise Strategy Group study, the skills required cover diverse areas of cybersecurity, including:
- Managing and monitoring remediation efforts
- Monitoring for security incidents
- Implementing security controls
- Identifying and assessing threats and vulnerabilities
- Responding to security incidents
- Prioritizing remediation efforts
- Reporting on current security posture
Bringing all these disciplines together is virtually impossible in a siloed organizational structure using siloed tools.
“Launching an exposure management program means shifting ownership of key, siloed security functions, which can require teams to work together in ways they haven’t before.”
— Jorge Orchilles, Senior Director of Readiness and Proactive Security, Verizon
The Enterprise Strategy Group report advises that these functions “must be consolidated under one management umbrella if security teams are to maximize efficiency.”
The bottom line? Moving to exposure management is as much about people as it is about tools.
In a guest blog for Tenable, “Exposure Management Is the Future of Proactive Security,” Jorge Orchilles, Senior Director of Readiness and Proactive Security at Verizon, discussed his approach. “While the right platform makes all the difference, implementing exposure management isn't purely technical. It’s organizational,” Orchilles wrote. “Launching an exposure management program means shifting ownership of key, siloed security functions, which can require teams to work together in ways they haven’t before.”
The change management involved is best done thoughtfully. “It required high-level buy-in and careful planning,” wrote Orchilles. “These teams weren’t just being asked to use a new tool, they were being asked to change the way they work. The only way to make that transition successful is by showing team members how this approach makes their jobs easier, not harder.”
3 recommendations for building an exposure management team
- Establish an exposure management policy framework: This is an evolution of your vulnerability management framework. It provides structure, establishes service level agreements (SLAs) and ensures accountability. An exposure management policy framework encompasses all inputs that produce information from every security tool: misconfigurations, vulnerabilities, identity weaknesses and more. You need a solid framework before you can begin building an exposure management team.
- Start small. Focus on a single team, a specific business unit or one critical use case. By showing success in one area, you can build momentum, secure broader buy-in and expand the program organically over time. This phased approach respects your team's limited resources while delivering incremental value.
- Make the most of the expertise — and tools — you already have. While the goal is to break down silos, the reality is that each security domain requires its own depth of expertise and skill in working with the appropriate tools. You don’t want to sacrifice that expertise in the effort to unify. Nor do you need to rip and replace your existing security stack. A platform like Tenable One is designed to ingest data from across your existing security tools. It gives all the domain experts on your exposure management team a contextualized view of your environment, improving communication and efficiency.
How Tenable can help
The Tenable One Exposure Management Platform unifies tools, data and teams across domains to enable seamless collaboration and deliver measurable risk reduction.
With Tenable One, exposure management teams can:
- Gain shared visibility into risk: See your entire cyber risk landscape as one connected picture, across every asset, risk and pathway in your attack surface, so you can spot the gaps that leave you exposed.
- Connect context across the attack surface: Combine data and intelligence from every domain, linking insights to reveal the real exposures that threaten your business, reputation and customer trust.
- Collaborate to drive effective risk reduction: Break down silos by enabling teams to work as one, focusing efforts where they matter most. Identify remediation bottlenecks and ownership gaps to ensure accountability, timely resolution of critical issues and adherence to SLA commitments.
- Make informed, data-driven decisions: Prioritize remediation based on business impact, optimize resource allocation and proactively address high-risk threats before they escalate.
- Demonstrate impact to stakeholders: Communicate measurable improvements and program effectiveness, showing how security initiatives support business goals and reduce overall organizational risk.
Learn more
- Read the Enterprise Strategy Group report, “The Evolution of Risk Reduction: Contextual Analysis and Automated Remediation in Threat and Exposure Management”
- Check out the Exposure Management Resource Center
- Visit the Exposure Management Academy
- Learn more about Tenable One
- Exposure Management


