Securing Critical Infrastructure: What We've Learned from Recent Incidents

Learn about well-known vulnerabilities and attacks and how they affected critical infrastructure — from Phone Phreaking to recent ransomware.
Cyberattacks against critical infrastructure are on the rise. The FBI’s Internet Crime Complaint Center (IC3) highlighted in its 2021 Internet Crime Report that 649 complaints of ransomware attacks were received from organizations in the critical infrastructure sector, a 7% increase over the prior year. Organizations in the healthcare, public health, financial services and information technologies sectors — which are among the 16 critical infrastructure sectors identified by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) — are the most frequent victims of ransomware, according to the study. And the IC3 anticipates a surge of attacks against critical infrastructure in 2022.
The Colonial Pipeline ransomware attack serves as an example of how the surge in vulnerabilities in IT systems can severely impact operations and, potentially, the overall U.S. economy at large.
Industries are investing more into Supervisory Control and Data Acquisition (SCADA) systems, with a market forecast reach of $15 billion USD by 2030 with a CAGR of 7% according to a recent research report by Market Research Future. While recognizing that otherwise simple security measures like patching can have impact on operations for OT systems like SCADA systems, neglecting it leaves the door wide open for substantial consequences.
While IT and OT systems have common touch points each faces a diverse set of challenges. For example, patching vulnerabilities in OT systems is challenging because small errors can shut down entire plants and facilities. OT often involves legacy systems that require specialized know-how that, if not consistently shared and passed to future employees, can add to the complexity of both operating devices as well as patching them.
However, the effects of security incidents on the supply chain can be overwhelming.
Back to the future
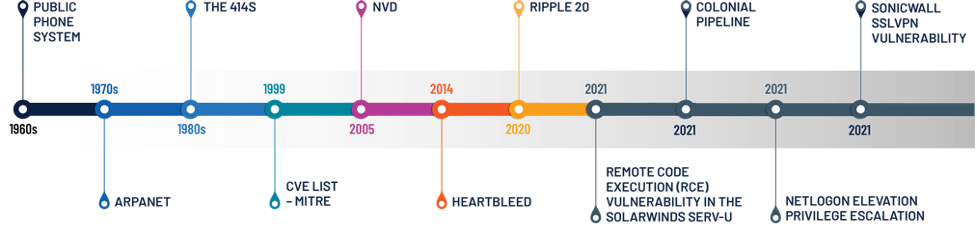
The need to protect critical infrastructure certainly is not new. First attacks date back to the 1960s when the first phone hacking mechanisms exploited the public phone systems.
ARPANET, the first public packet-switched computer network, was first used in 1969. Shortly after, in 1971, the first instance of a “worm” (CREEPER) was created and the first Denial of Service attacks were born. During the early 1980s, the 414s marked the hacking scene’s break into computer systems at several institutions.
As internet connectivity became ubiquitous, organizations needed a way to easily share relevant vulnerability data across organizations and industries. In 1999, MITRE introduced the Common Vulnerabilities and Exposures (CVE) list system. In 2005, CVEs were followed by the National Institute of Standards and Technologies’ (NIST) National Vulnerability Database (NVD). Meanwhile, vulnerabilities and threats continued to proliferate.
Heartbleed left its mark on industrial control systems in 2014. More recently, vulnerabilities such as the Ripple20 set — which affects a software library widely used in OT, IoT and IT devices — remain a significant concern. Attacks against the software supply chain, such as the 2020 breach of the SolarWinds Orion platform, have upped the ante by targeting the auto-update features of a vendor’s software. And, attacks don’t always need to target OT systems directly to have a significant impact on critical infrastructure. The 2021 ransomware attack against the IT systems of Colonial Pipeline is a case in point: although the organization’s OT systems were not compromised, the decision was made to take the pipeline out of service out of an abundance of caution, causing fuel shortages up and down the densely populated East Coast of the United States.
Vulnerability landscape: Behind the scenes
Securing critical infrastructure requires accounting for the complexities of IT and OT systems, understanding their diverse challenges and being prepared to overcome the obstacles stemming from their integration.
The recent attacks and threats discussed in this blog are critical and sophisticated. The table below is a selected list of widely covered vulnerabilities which have implications for critical infrastructure operators.
| CVE | 說明 | CVE Rating |
|---|---|---|
|
高 |
||
|
CVE-2020-11896, CVE-2020-11897, CVE-2020-11901 (out of 19) |
Medium to Critical |
|
|
Remote code execution (RCE) vulnerability in the SolarWinds Serv-U |
重大 |
|
|
重大 |
||
|
Netlogon Elevation Privilege Escalation- privilege escalation |
重大 |
原文:Tenable, July 2022
As previously noted, each vulnerability in the above table affected critical infrastructure in different ways.
Colonial Pipeline: From IT systems to OT shutdown
The ransomware attack against the IT system of Colonial Pipeline, one of the biggest U.S. fuel pipeline operators, is an example of how an attack on IT systems can also have significant impact on critical infrastructure.
The group responsible for the Colonial Pipeline incident and many other notable ransomware attacks is known to use these vulnerabilities:
- CVE-2021-20016, a zero-day vulnerability affecting SonicWall Secure Mobile Access (SMA100), used for attack initiation; and
- CVE-2020-1472, a Zerologon vulnerability that — when successfully exploited — allows for privilege escalation by establishing a Microsoft Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC).
The attack led to a ransom payment of roughly $4.4 million and, while the OT systems controlling the pipeline itself were not breached, the organization opted to shut down operations for five days out of an abundance of caution. The case exemplifies how the convergence of IT/OT systems, and the related pursuit of digital transformation as a business driver, affects critical infrastructure operators.
總結
While vulnerability management remains a powerful tool to integrate into the overall business lifecycle, it’s not without its challenges in critical infrastructure environments. Among the challenges:
- In many cases, devices running on OT networks are no longer supported. The companies behind them may have long gone out of business.
- In other cases, there’s a lack of a clear update mechanism, such as an interface or software update utility, so even if an OT vendor wanted to release a patch, it would be difficult to deploy.
- Without an effective way to patch or remediate, an organization is left to figure out how to reduce or mitigate an attack surface by isolating network traffic and devices, firewalls and VPNs and unique routing tables.
Critical infrastructure providers are also heavily focused on uptime above all else, which introduces several challenges for patching OT systems, including:
- The potential for patching to cause downtime of critical operational technologies,
- A lack of fixes for legacy systems,
- A lack of staff with the right expertise on how to secure legacy systems.
Resolving these and other challenges related to critical infrastructure security requires a concerted effort by operators, vendors and government agencies around the world. Finding and fixing vulnerabilities in the IT and OT systems used in these environments is just the first step.
Editor's note: This blog was revised on July 15 to more accurately reflect the context in which we discuss CVE-2021-20016 and CVE-2020-1472.
取得更多資訊
Read our blog posts:
- The State of OT Security a Year Since Colonial Pipeline
- Securing Critical Infrastructure: It's Complicated
- Colonial Pipeline 勒索軟體攻擊: 如何降低 OT 環境的風險
Listen to the The State of OT Security, a Year Since Colonial Pipeline podcast
Download the whitepaper Prediction of an OT Attack.
Read the report A look inside the ransomware ecosystem.
We recently held a transport-focused OT webinar – Unpacking Some of the Most Common Cybersecurity Challenges Facing Your Transportation-Sector Business. The session included panelists from the U.S. Transportation Security Administration (TSA) and two of our partners. If you missed it make sure you catch the recording and keep an eye on our list of future webinars as we’ve more planned around this topic.
- OT Security
- Risk-based Vulnerability Management
- SCADA
- Threat Management
- Vulnerability Management



