Ransomware Preparedness: Why Organizations Should Plan for Ransomware Attacks Like Disasters

As ransomware has cemented itself as one of the biggest cybersecurity threats to companies around the globe, it has become increasingly important that organizations treat ransomware attacks like they would a natural disaster and establish a robust preparedness plan.
背景說明
In 2020, Chris Krebs, the former director of the Cybersecurity and Infrastructure Security Agency (CISA) called ransomware the “most visible, disruptive cyber threat” as he saw it then. Nearly two years later, Lindy Cameron, the chief executive of the National Cyber Security Centre (NCSC) in the United Kingdom calls ransomware the “biggest global cyber threat” today.
Over the last four years, CISA, NCSC and other global agencies including the FBI and the Australian Cyber Security Centre (ACSC) have issued multiple warnings about the risk of ransomware, yet it remains the most dominant threat facing organizations today.
In a recent survey of chief information security officers, nearly 70% expect to be impacted by a ransomware attack within the next year, with nearly a quarter of companies saying they were impacted by ransomware attacks on more than one occasion.
Despite the prevalence of these attacks, many organizations are not adequately prepared to respond to ransomware incidents. Organizations should ready themselves for ransomware like they do for any other emergency.
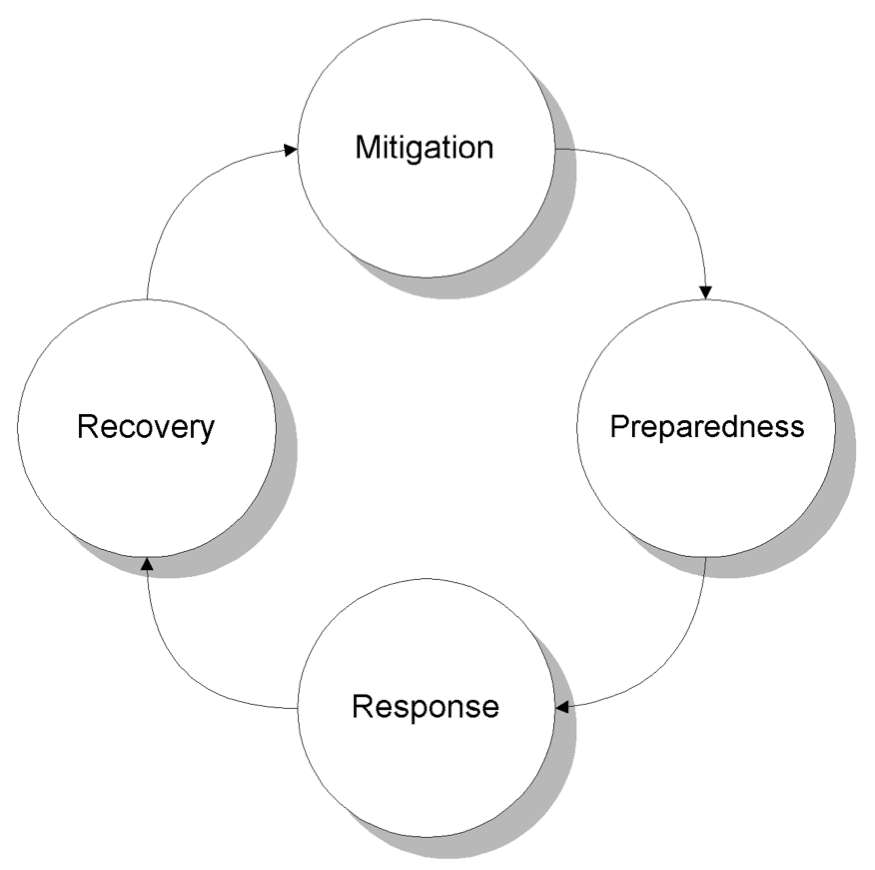
The Federal Emergency Management Agency (FEMA) in the United States has outlined the four phases of emergency management for disasters and emergencies as: mitigation, preparedness, response and recovery. This same framework can be applied to ransomware attacks.
Mitigation is the natural first step in defense
For any organization looking to defend against ransomware attacks, their primary focus should be placed on mitigation. You are likely familiar with the mitigation steps you and your organization have taken to prepare for the sorts of disasters covered by FEMA’s guidance: evacuation maps around the office in the case of a fire, maintaining insurance, battening down the hatches.
When it comes to ransomware, we know many of the tactics and techniques used by the key members in the ransomware ecosystem, from spearphishing and targeting Remote Desktop Protocol (RDP) to exploiting unpatched and zero-day vulnerabilities. Mitigation relies on identifying and securing these known attack paths, whether it’s through the use of antivirus or anti-malware and email gateways, user awareness training and vulnerability management solutions. However, even with this wealth of knowledge, organizations continue to fall victim to ransomware attacks.
Organizations should prioritize preparedness
Regardless of the emergency for which you are preparing, having a plan is critical. Most organizations likely already have incident response plans for events like natural disasters; mature organizations likely also have technology or cybersecurity focused incident response plans. As FEMA notes in one of its sample emergency management documents, it’s not just about writing the plan, but about drilling the plan and refining it.

Preparedness is an often overlooked element in the emergency management of ransomware attacks. It is not just about focusing on the various mitigation measures as a form of preparation, it is also imperative for organizations to prepare by conducting simulated attacks against their networks to test incident response plans with various stakeholders. CISA has published a variety of CISA Tabletop Exercise Packages (CTEPs) that can be the foundation for your organization’s preparedness. Walking through a simulated ransomware attack enables an organization to identify gaps in their incident response plans. Additionally, being prepared makes the various stakeholders within your organization feel confident that in the event of a real ransomware attack, the response will be measured instead of chaotic.
Response and recovery is sometimes chaotic
Response is when you put your tested plans into practice and see whether your mitigations meet their intended purpose. According to FEMA, “business and other functions do not operate normally” during these phases. The focus is on understanding and limiting the disaster’s scope of impact, shaping public perception of the incident and beginning the process of returning to “business as usual.”
How an organization responds to a ransomware attack has become more important over the last few years, as ransomware groups not only encrypt files within a company’s network, but also exfiltrate and threaten to publish these files on leak websites hosted on the dark web. This tactic creates a sense of urgency, as ransomware groups provide little time for negotiations. So while an organization is tasked with trying to recover from an attack and restore network operations, they also face the added pressure of reputational harm from the leak of confidential information.
Because of the public nature of leak websites and the ardent tracking by reporters, ransomware response is often done in the public eye. This means that response operations are not limited to security and IT teams. Teams including customer support, legal, public relations and investor relations may all end up involved in the response. Those groups should also be part of preparedness efforts.
A challenge when responding to a ransomware attack is that organizations must negotiate with individuals or groups that weren’t responsible for attacking them. In the ransomware ecosystem, third parties such as ransomware affiliates and initial access brokers are the ones gaining a foothold within an organization before selling that access or partnering with ransomware groups directly. This distributed involvement can complicate negotiations and the investigations necessary for recovery.
Several moving parts are involved in the response and recovery process, but organizations don’t need to operate from a reactive position. They can be proactive through preparedness.
A global preparedness initiative is needed
In the United States, the Department of Homeland Security’s ready.gov resource provides low cost and free preparedness guides. We believe a similar resource should be created for ransomware preparedness and made available for organizations around the world, since ransomware is a global threat, as the NCSC’s Cameron has pointed out.
Steps you can take right now to be more prepared
- Review your incident response plans (or start developing one) and confirm it’s sufficient to address a ransomware attack.
- Conduct tabletop exercises with various stakeholders within your organization at least once a year if not more often.
- Cut off known attack vectors by patching known, exploited vulnerabilities and addressing Active Directory misconfigurations. Tenable Research has produced scan templates and dashboards for Tenable.io, Tenable.sc and Nessus that can help identify known vulnerabilities used by ransomware affiliates and IABs.
- Establish visibility for your organization’s full attack surface and how attackers may seek to breach your defenses.
取得更多資訊
- Tenable Report: A Look Inside The Ransomware Ecosystem
- Tenable Blog on Understanding the Ransomware Ecosystem
- Tenable Blog on the LAPSUS$ Extortion Group
加入 Tenable Community 的 Tenable 安全回應團隊。
深入瞭解 Tenable,這是用於全面管理新型攻擊破綻的首創 Cyber Exposure 平台。
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Research Reports
- Vulnerability Management


