CVE-2019-14994:Jira Service Desk 的 URL 路徑周遊弱點導致資訊洩露

Path traversal flaw in Jira Service Desk can be used by attackers to view protected information in Jira projects.
背景說明
On September 18, Atlassian published a security advisory for a vulnerability in Jira Service Desk, an IT ticketing application used by over 25,000 organizations to accept, manage and track requests from customers and employees through a web portal.
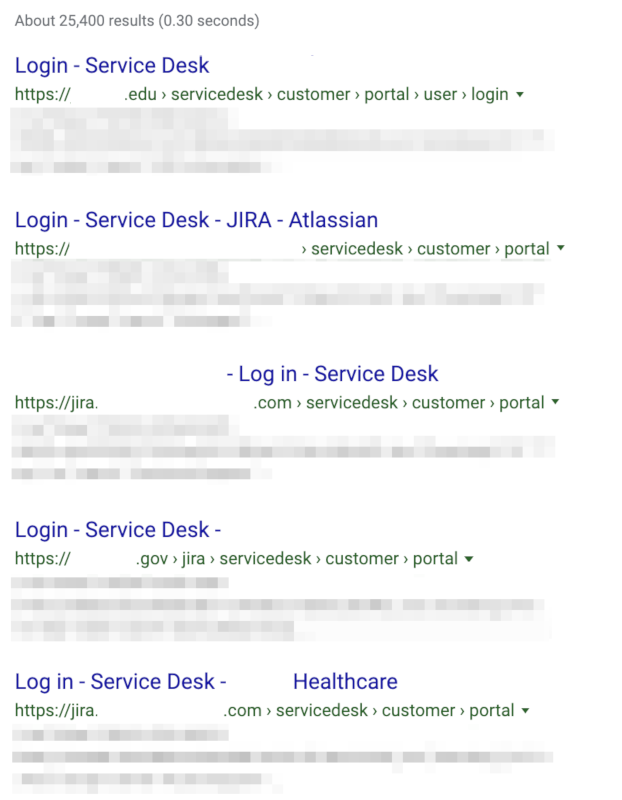
Tenable Research has identified many publicly accessible Jira Service Desk instances belonging to organizations in healthcare, government, education and manufacturing in the United States, Canada, Europe and Australia. The following is a screenshot of search engine results listing publicly accessible Jira Service Desk portals.
In related news, Atlassian has also released a security advisory for CVE-2019-15001, an authenticated template injection vulnerability in the Jira Importers Plugin for Jira Server reported by security researcher Daniil Dmitriev. Dmitriev discovered and reported another template injection vulnerability, CVE-2019-11581, back in July.
分析
CVE-2019-14994 is a URL path traversal vulnerability in Jira Service Desk and Jira Service Desk Data Center. By default, the ticketing system restricts customers’ or employees’ access to certain privileges, such as opening new requests or viewing existing requests without accessing the company’s Jira instance directly.
According to the advisory, an attacker with access to the web portal can send a specially crafted request to the Jira Service Desk portal to bypass these restrictions and view protected information. In order to exploit the vulnerability, the Customer Permissions settings for who can raise a request must be set to “Anyone can email the service desk or raise a request in the portal,” which may be a common configuration because the other two options limit who can open requests. In addition to viewing protected information within Jira Service Desk, an attacker could also view protected information from Jira Software and Jira Core if the “Browse Project” permission is set to Group - Anyone.
While full details about the vulnerability are not public at this time, Sam Curry, the researcher who discovered the vulnerability, tweeted that he plans to publish more details, including a proof-of-concept (PoC), soon. Curry also credited DEVCORE researcher Orange Tsai’s previous work, which stems from a Black Hat and DEFCON presentation from 2018 called “Breaking Parser Logic! Taking Your Path Normalization off and Pop 0days Out.”
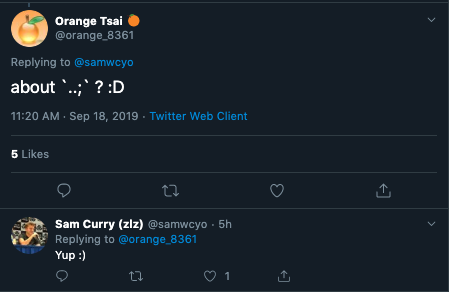
Researcher Sam Curry responds to Orange Tsai on Twitter
Curry confirmed to Tsai his findings are linked to Tsai’s example of accessing Uber’s internal Jira server, appending “..;” to the URL path parameter, which gets treated as a parent directory. Atlassian appears to confirm this in its knowledgebase article for the vulnerability.
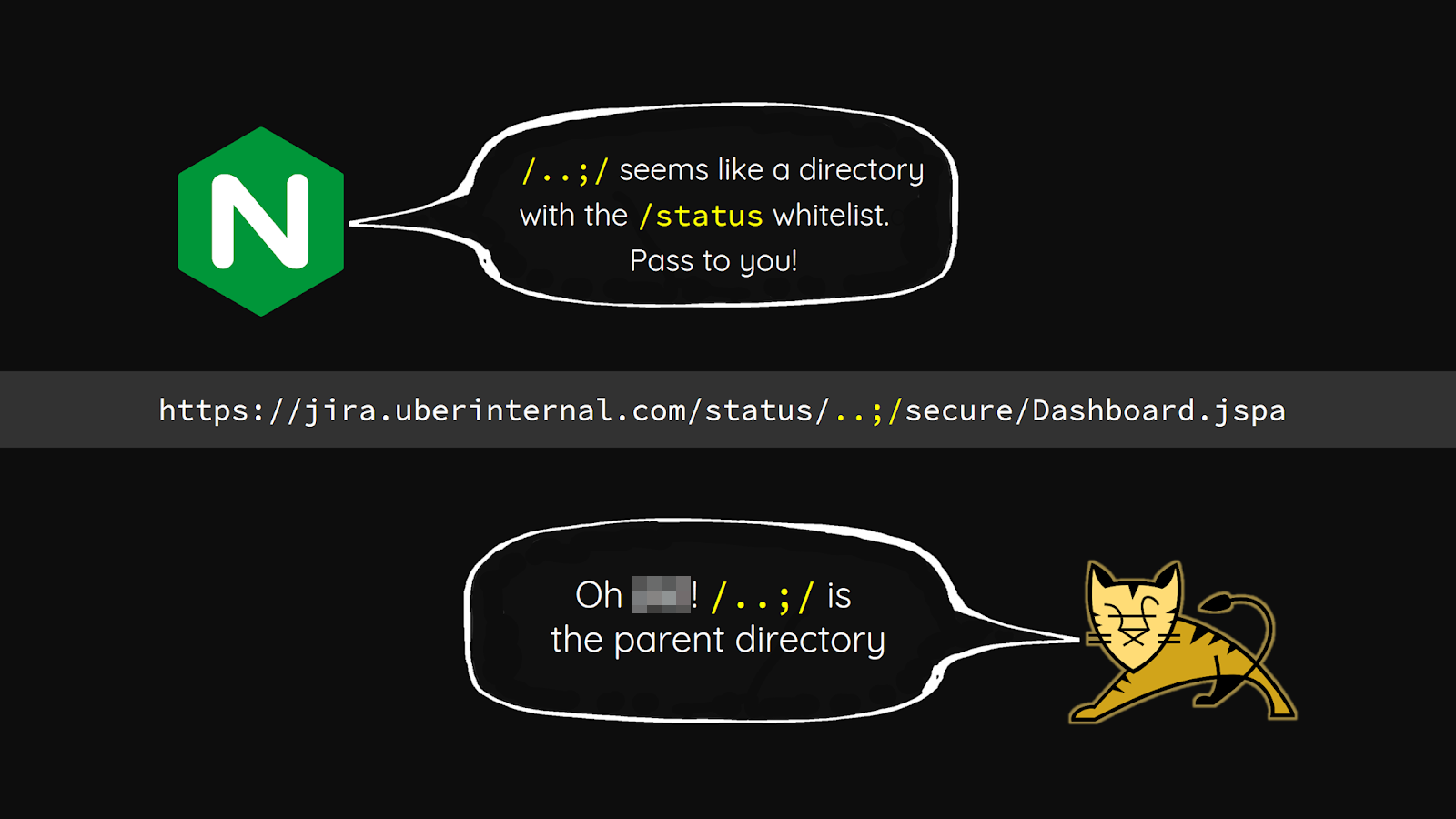
Slide deck from Orange Tsai’s Black Hat presentation on accessing Uber’s internal Jira server
概念驗證
While there was no PoC available when this blog was published, the researcher plans to release a PoC soon.
解決方法
Atlassian has released updated versions of Jira Service Desk Server and Jira Service Desk Data Center to address this vulnerability. The following table contains the list of vulnerable versions with the associated fixed versions.
| Affected Version | Fixed Version |
|---|---|
| 3.9.16 and prior | 3.9.16 or 3.16.8 |
| 3.10.0 through 3.16.7 | 3.16.8 |
| 4.0.0 through 4.1.2 | 4.1.3 |
| 4.2.0 through 4.2.4 | 4.2.5 |
| 4.3.0 through 4.3.3 | 4.3.4 |
| 4.4.0 | 4.4.1 |
Fixed versions can be retrieved from Atlassian’s Service Desk update page.
If upgrading to a patched version of Jira Service Desk Server or Service Desk Center is not feasible at this time, Atlassian has also provided temporary workarounds to thwart attacks.
Organizations using Jira Service Desk Server or Service Desk Center should consider patching as soon as possible ahead of the release of a PoC and exploit attempts from attackers.
找出受影響的系統
A list of Tenable plugins to identify this vulnerability will appear here as they’re released.
取得更多資訊
加入 Tenable Community 的 Tenable 安全回應團隊。
深入瞭解 Tenable,這是用於全面管理新型攻擊破綻的首創 Cyber Exposure 平台。
Get a free 60-day trial of Tenable.io Vulnerability Management.
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning


