CVE-2019-11580:Proof-of-Concept for Critical Atlassian Crowd Remote Code Execution Vulnerability Now Available

A proof-of-concept for critical Atlassian Crowd vulnerability patched on May 22 is now available.
背景說明
On July 14, security researcher Corben Leo published a blog detailing the analysis of a recently patched vulnerability in Atlassian Crowd, a user management application for access control for Active Directory (AD), Lightweight Directory Access Protocol (LDAP), OpenLDAP and Microsoft Azure AD.
分析
On May 22, Atlassian published Crowd Security Advisory 2019-05-22 to address CVE-2019-11580. According to the advisory, Crowd and Crowd Data Center incorrectly enabled a development plugin for pdkinstall in release builds. A remote attacker could exploit this flaw to install arbitrary plugins by sending unauthenticated or authenticated requests to vulnerable Crowd or Crowd Data Center instances, which could grant them the ability to execute code.
Leo’s blog post provides analysis of the pdkinstall plugin and the PdkInstallFilter servlet, which he used to craft a proof-of-concept (PoC) that allowed him to gain pre-authenticated remote code execution in Atlassian Crowd.
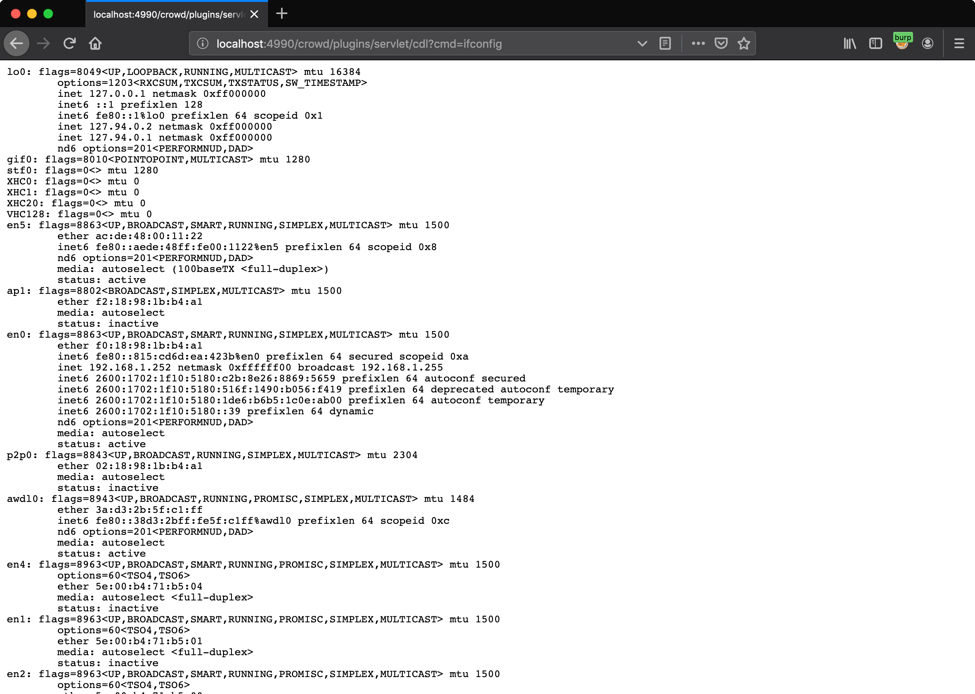
Image credit: Corben Leo
概念驗證
Leo published a malicious plugin on GitHub to be used as part of a PoC included in his blog post:
curl -k -H "Content-Type: multipart/mixed" \ --form "[email protected]" http://localhost:4990/crowd/admin/uploadplugin.action
解決方法
Atlassian published patched versions of Crowd and Crowd Data Center on May 22. The patched versions include 3.0.5, 3.1.6, 3.2.8, 3.3.5, and 3.4.4. The following table lists the vulnerable versions and the associated fixed versions.
|
Affected Versions |
Fixed Version |
|
2.1.0, 2.1.1, 2.1.2, 2.2.0, 2.2.1, 2.2.2, 2.2.3, 2.2.4, 2.2.5, 2.2.6, 2.2.7, 2.2.8, 2.2.9, 2.3.0, 2.3.1, 2.3.2, 2.3.3, 2.3.4, 2.3.5, 2.3.6, 2.3.7, 2.3.8, 2.3.9, 2.3.10, 2.4.0, 2.4.1, 2.4.2, 2.4.3, 2.4.4, 2.4.5, 2.4.6, 2.4.7, 2.4.8, 2.4.9, 2.4.10, 2.4.11, 2.5.0, 2.5.1, 2.5.2, 2.5.3, 2.5.4, 2.5.5, 2.5.6, 2.5.7, 2.6.0, 2.6.1, 2.6.2, 2.6.3, 2.6.4, 2.6.5, 2.6.6, 2.6.7, 2.7.0, 2.7.1, 2.7.2, 2.8.0, 2.8.1, 2.8.2, 2.8.3, 2.8.4, 2.8.6, 2.8.7, 2.8.8, 2.9.1, 2.9.2, 2.9.3, 2.9.4, 2.9.5, 2.9.6, 2.9.7, 2.10.1, 2.10.2, 2.10.3, 2.10.4, 2.11.0, 2.11.1, 2.11.2, 2.12.0, 2.12.1, 3.0.0, 3.0.1, 3.0.2, 3.0.3, 3.0.4 |
|
|
3.1.0, 3.1.1, 3.1.2, 3.1.3, 3.1.4, 3.1.5 |
|
|
3.2.0, 3.2.1, 3.2.2, 3.2.3, 3.2.4, 3.2.5, 3.2.6, 3.2.7 |
|
|
3.3.0, 3.3.1, 3.3.2, 3.3.3, 3.3.4 |
|
|
3.4.0, 3.4.1, 3.4.2, 3.4.3 |
If upgrading to a patched version of Atlassian Crowd is not feasible at this time, Atlassian provided mitigation steps in their Security Advisory to address the vulnerability as well as a bash script to automate the mitigation steps on Linux systems.
找出受影響的系統
A list of Tenable plugins to identify this vulnerability can be found here.
Get more information
加入 Tenable Community 的 Tenable 安全回應團隊。
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
