CVE-2017-9841:利用 Mailchimp 模組中的 PHPUnit 弱點攻擊 Drupal 網站, (PSA-2019-0904)

Attackers are leveraging a vulnerability patched nearly three years ago to target Drupal sites.
背景說明
On September 4, Drupal published PSA-2019-09-04, a public service announcement (PSA) for a vulnerability in a third-party library in a Drupal module that’s being actively exploited in the wild.
分析
CVE-2017-9841 is a code injection vulnerability in PHPUnit, a PHP unit testing framework. The PHPUnit library is part of the Mailchimp and Mailchimp E-Commerce modules in Drupal which, according to their modules pages, are currently used by over 25,000 sites combined.
In June 2017, a Twitter account called “vulnbusters” was created and published an advisory for the vulnerability on their now-defunct website, which is available through the Internet Archive’s Wayback Machine here.
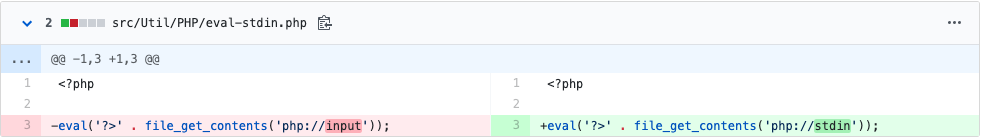
The advisory identifies the vulnerability within the /phpunit/src/Util/PHP/eval-stdin.php file through its use of the php://input wrapper. Patched versions of PHPUnit use the php://stdin wrapper instead. An unauthenticated attacker could exploit this vulnerability by sending an HTTP POST request to a web server containing the vulnerable eval-stdin.php file, leading to arbitrary code execution.
Previous versions of PHPUnit contained the code injection vulnerability which, according to the Vulnbusters advisory page, was unknowingly patched in November 2016 in PHPUnit version 4.8.28 and version 5.6.3 to address issues with insulated tests using phpdbg.
In February 2018, an issue was filed on the Mailchimp project on Drupal from a user who was contacted by their hosting provider, indicating that the eval-stdin.php on their web server was malicious. A different user, who commented on the same issue in May 2018, also received the same feedback from their hosting provider. Separately, in February 2018, Kevin Beaumont (@GossiTheDog) found attackers were targeting a Drupal honeypot attempting to exploit CVE-2017-9841.
Ok, MailChimp API ships PHPunit, which as a remote unauthenticated code execution bug https://t.co/fAQjErb2ed - there’s no known exploit I can see but somebody has one.
— Kevin Beaumont (@GossiTheDog) February 26, 2018
Outside of Drupal, CVE-2017-9841 has also been found in WordPress plugins, such as the Jekyll Exporter plugin, as well as MediaWiki and open source learning platform Moodle.
概念驗證
A proof-of-concept (PoC) was originally published in the Vulnbusters advisory from June 2017.
解決方法
As previously mentioned, CVE-2017-9841 was patched in PHPUnit back in November 2016. The vulnerability affected specific versions of PHPUnit, which are referenced in the table below.
| Vulnerable PHPUnit Versions | Fixed PHPUnit Versions |
|---|---|
| 4.8.19 - 4.8.27 | 4.8.28 or later |
| 5.0.10 - 5.6.2 | 5.6.3 or later |
For the Mailchimp and Mailchimp E-Commerce modules, version 1.0.7 or below for the Mailchimp API for PHP is considered vulnerable. The Drupal Security team notes even if Drupal customers had previously installed these modules, there may still be artifacts left over from the installation on the web server. Vulnerable servers may have the eval-stdin.php. If the file exists and it references the php://input wrapper instead of the php://stdin wrapper, then the server is vulnerable to CVE-2017-9841.
找出受影響的系統
A list of Tenable plugins to identify this vulnerability will appear here as they’re released.
取得更多資訊
- Drupal Advisory for CVE-2017-9841
- Tenable CVE Summary: CVE-2017-9841
- Archive.org Entry for Vulnbusters
加入 Tenable Community 的 Tenable 安全回應團隊。
深入瞭解 Tenable,這是用於全面管理新型攻擊破綻的首創 Cyber Exposure 平台。
Get a free 60-day trial of Tenable.io Vulnerability Management.
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning


