Cryptocurrency Scams: Fake Giveaways Impersonate Followers of Political and Other Notable Figures

“Thank you Elon,” “God Bless You Elon” and “God Bless You Donald” – scammers have been lurking in the Twitter replies of the U.S. President, Tesla CEO and other notable figures, impersonating followers and using photoshopped tweets to promote fake cryptocurrency giveaways.
Since the beginning of 2020, scammers have been capitalizing on the high engagement on tweets from some of the most followed Twitter accounts in a scheme to trick followers to participate in cryptocurrency giveaways.
The crypto scam level on Twitter is reaching new levels. This is not cool.
— Elon Musk (@elonmusk) February 1, 2020
Old scam, new twist
Since 2018, a variety of cryptocurrency scams have circulated on Twitter impersonating cryptocurrency figures as well as Elon Musk and President Trump, two of the most popular personalities in these impersonations.
Image source: BuzzFeedNews
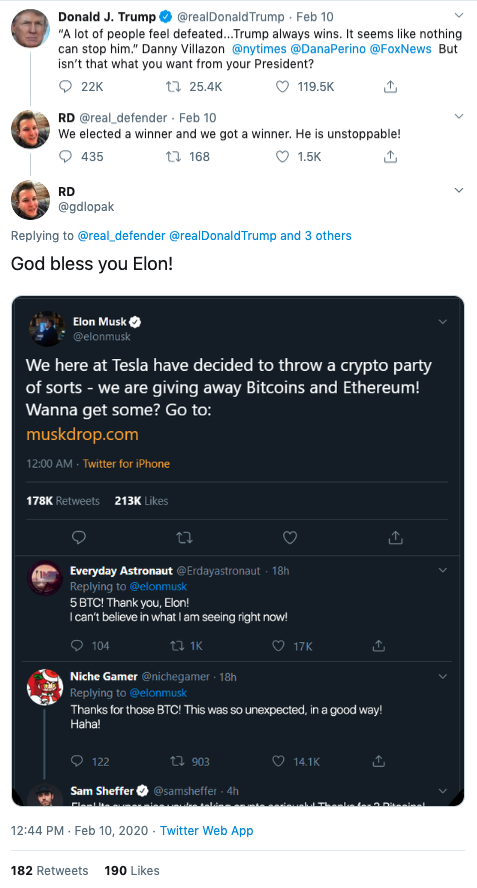
Impersonation of President Trump’s Twitter followers
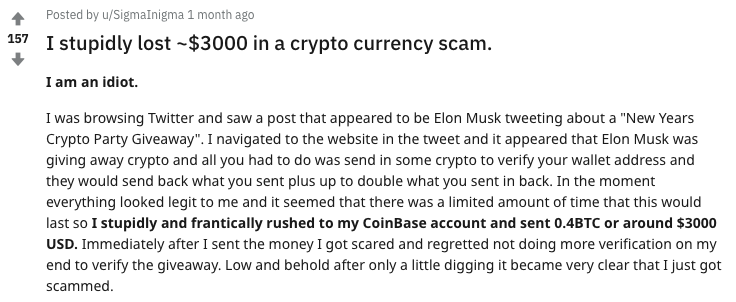
The latest tactic used by cryptocurrency scammers is to impersonate vocal Twitter users who regularly respond to tweets from President Trump.
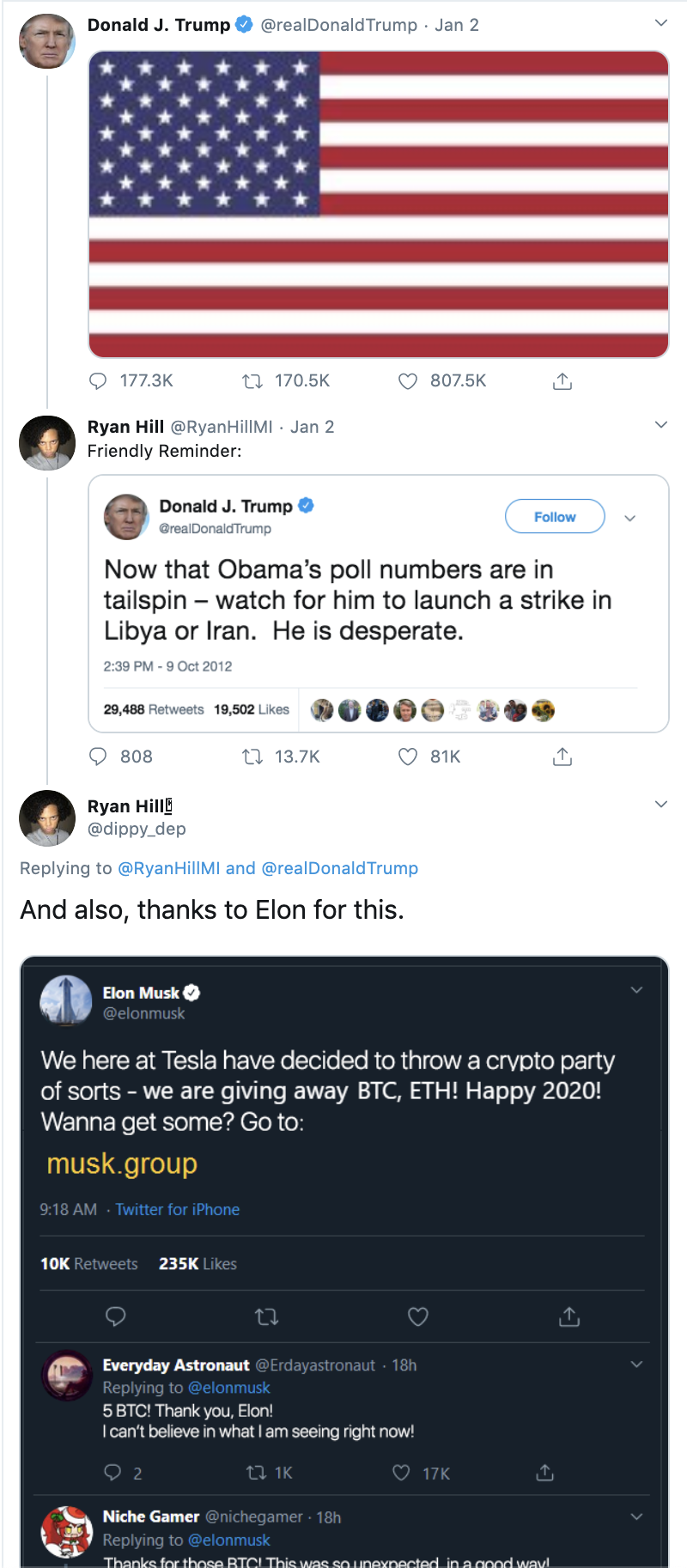
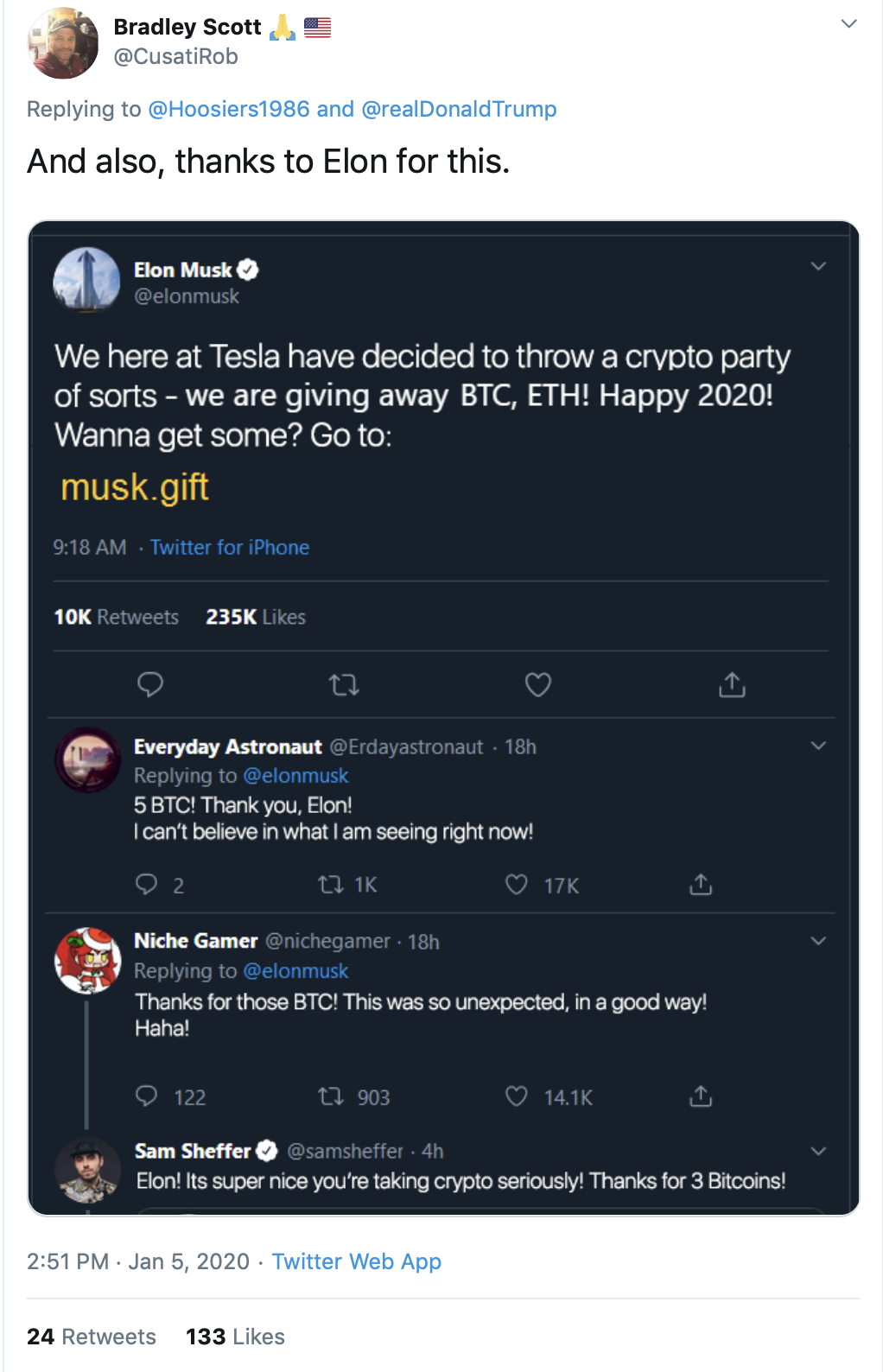
One of the earliest instances of this tactic was seen on January 2. Scammers used an impersonation account of Ryan Hill, a vocal Twitter user who regularly responds to President Trump. The scammers responded to one of Hill’s tweets to Trump. Their tweet included the quote, “And also, thanks to Elon for this,” and a photoshopped image of a fake tweet from Elon Musk. The photoshopped tweet from Musk claimed Tesla decided to “throw a crypto party,” where they would be giving away Bitcoin and Ethereum, two of the most popular cryptocurrencies. It included a link to a website with details about the supposed “crypto party.” The photoshopped tweet also contains fake replies from users claiming the supposed giveaway is legit.
Variety of impersonations
A variety of impersonations of vocal Twitter users appear in President Trump’s tweets. And most of these impersonators respond directly to the person they’re impersonating rather than the tweet from the president.
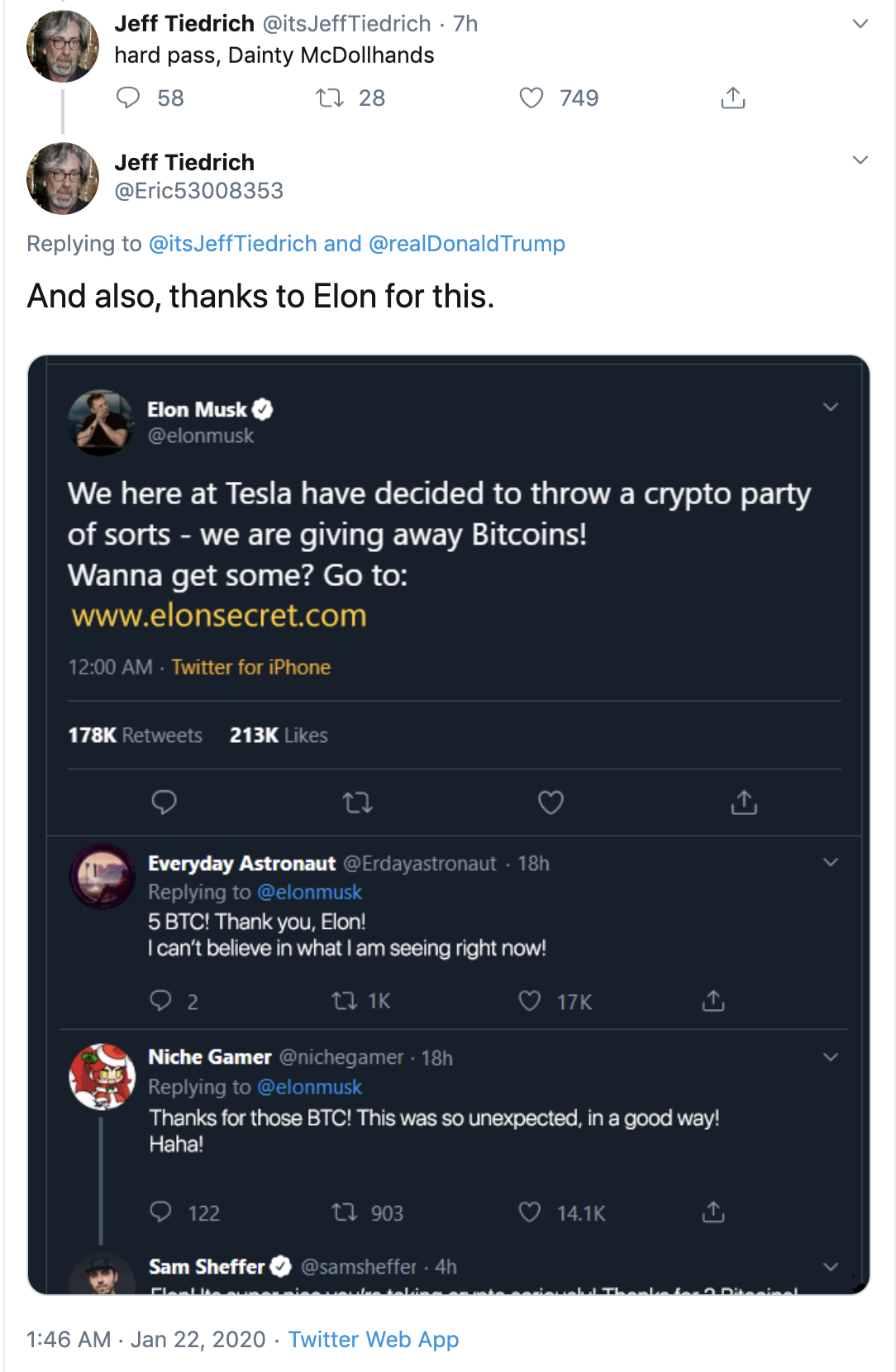
Falsifying social proof to provide legitimacy
To support the presence of these impersonation accounts and create a sense of legitimacy, scammers are leveraging other accounts to falsify social proof.
Many of the impersonators’ tweets have up to several hundred retweets and/or likes.
Unsurprisingly, however, many of these retweets and likes appear to be manufactured.
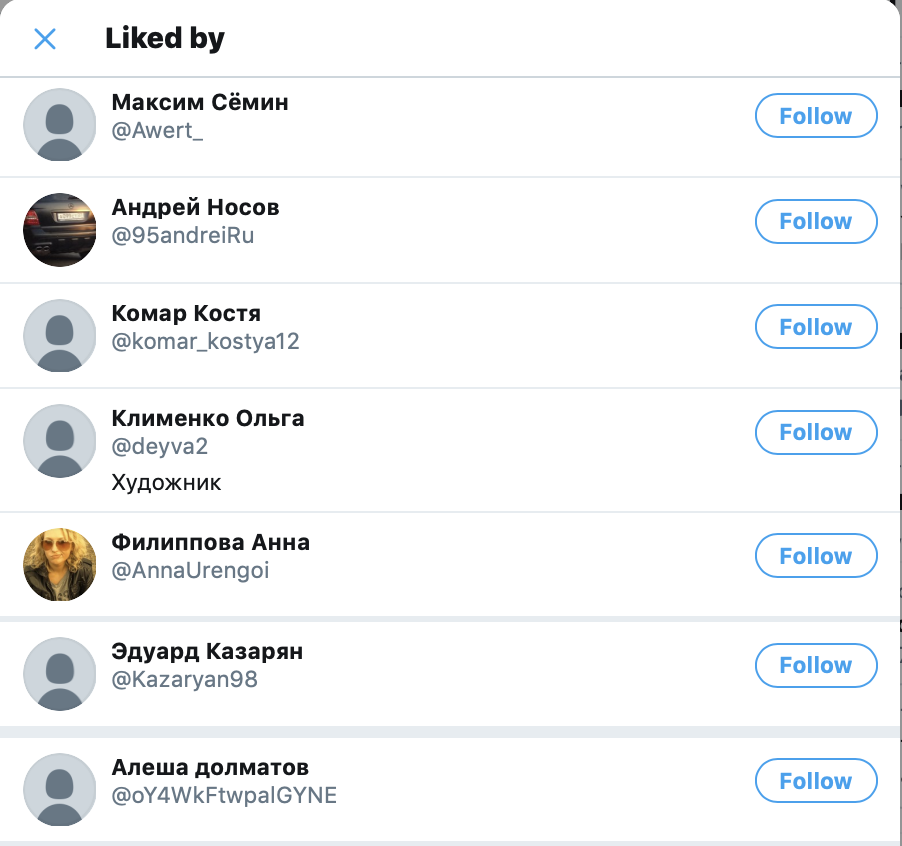
Looking at some of the likes associated with these tweets, we can make some observations. A subset of the accounts have no profile pictures, which typically signifies new or inactive user accounts or those who choose not to publish a profile photo. Their display names appear to be Russian.
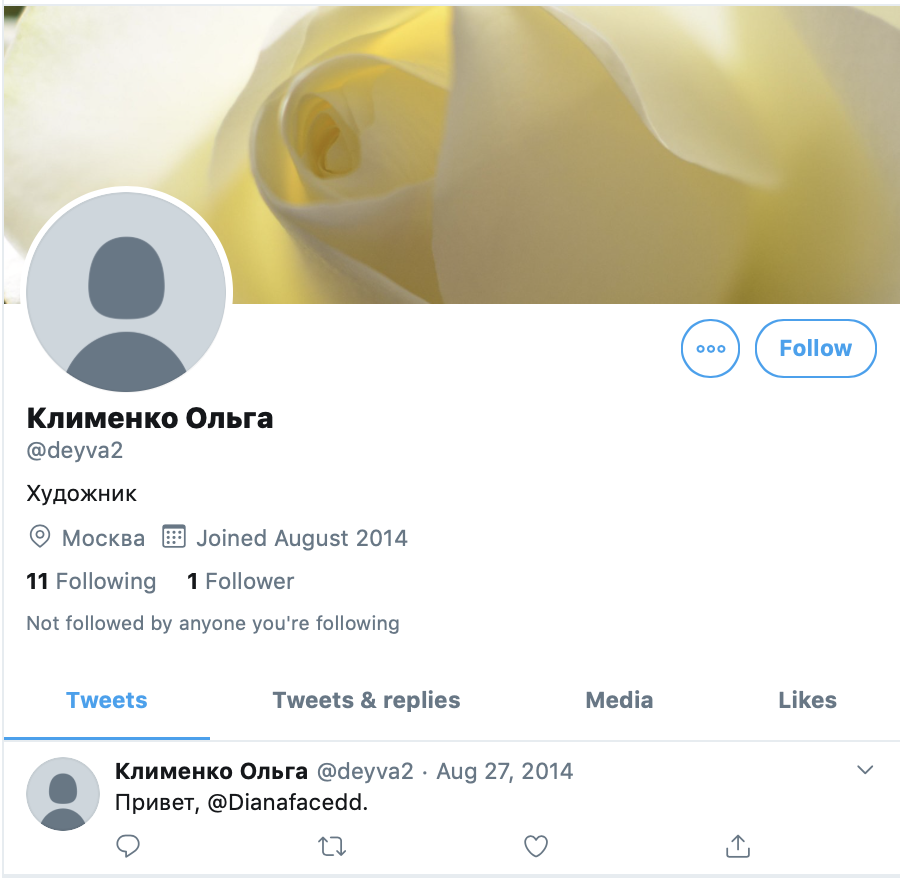
If we look at some of these accounts, we can see they show minimal previous activity. Likely, they are abandoned Twitter accounts that were sold in an underground forum, or had weak passwords on their accounts, and have been repurposed by these scammers.
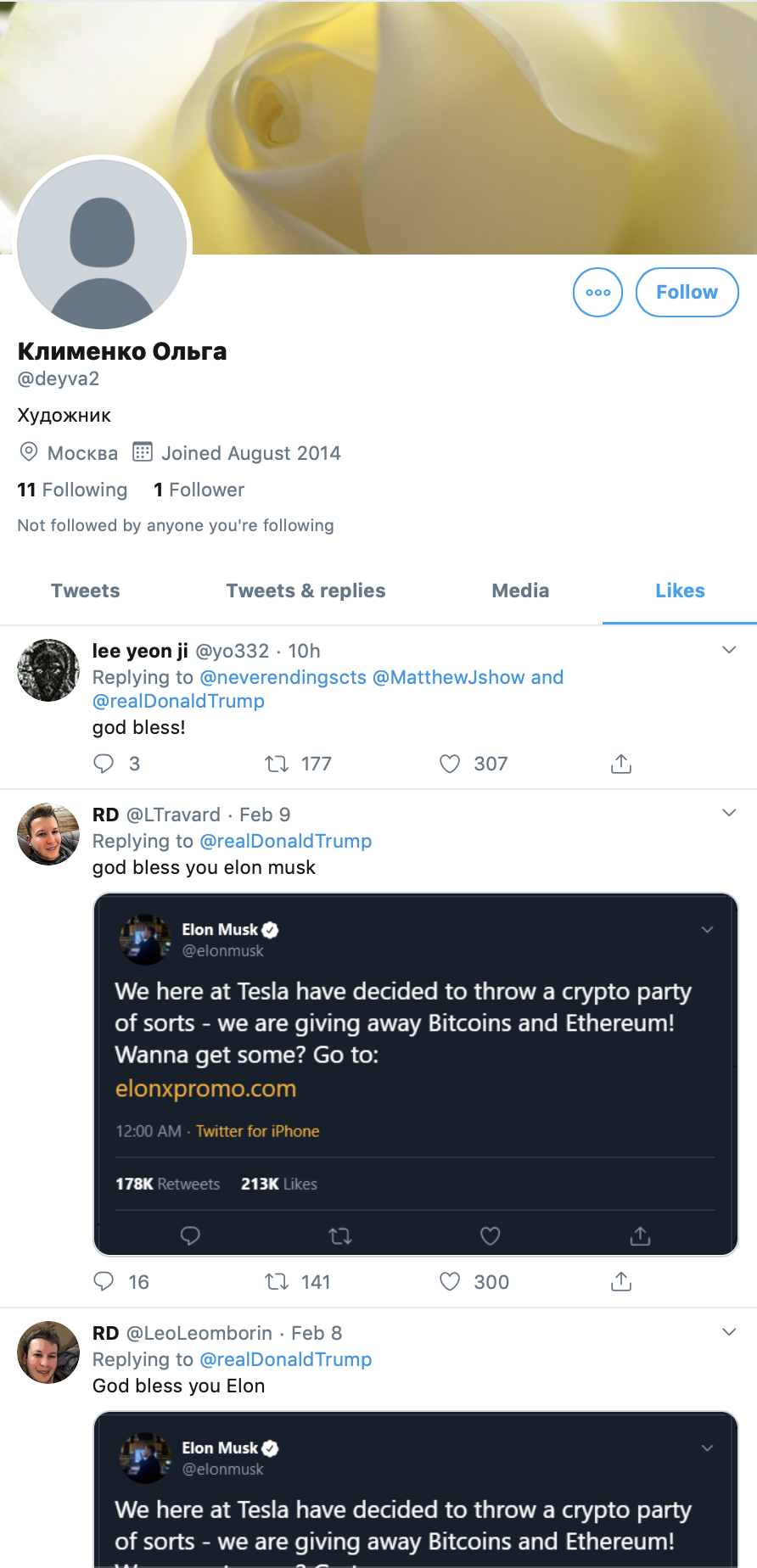
When digging into the likes associated with these accounts, we can verify they are primarily being used to like and retweet accounts associated with these fake giveaways.
Outside of likes and retweets, scammers are also using accounts to reply to these fake giveaway tweets, claiming they are legitimate.
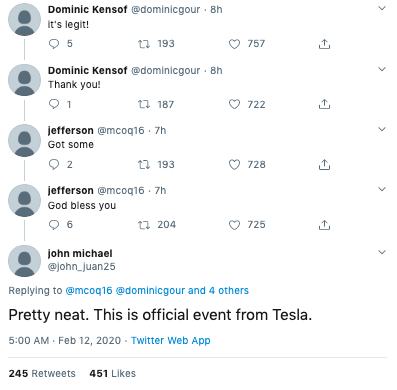
These tweets often have hundreds of likes and retweets as well, once again as a way to provide falsified social proof.
Verified accounts compromised
I’ve observed some instances where the scammers have compromised verified accounts and use them to prop up these scam tweets.
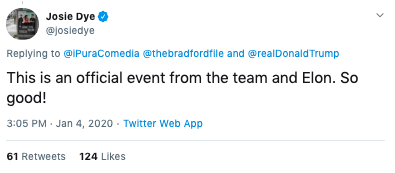
For instance, the scammers compromised the account of Canadian radio and television personality Josie Dye and used it to claim the giveaway is an “official event.”
Recently, scammers used the Twitter account of The Florida Times-Union reporter Ann Friedman in the same way as Dye’s account to claim the giveaway was an “official event,” adding she “can confirm it.”
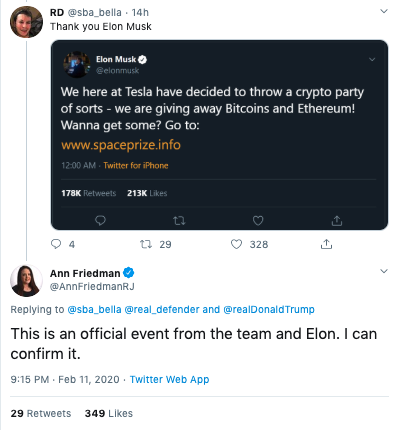
Clearly, neither of these verified accounts legitimately tweeted out support for these giveaways. But, the verified badge helps the scammers trick victims into believing their giveaways are real.
Historically, when scammers compromised verified Twitter accounts, they used them to pivot to impersonate Musk because the verified badge creates more of a sense of legitimacy. So, why aren’t scammers using these verified accounts to impersonate Elon Musk or President Trump directly? While I cannot confirm this, I suspect Twitter may have implemented some mechanisms to detect when a verified account suddenly changes its profile image and/or username to that of known public figures such as Musk. Therefore, the scammers are trying to preserve their access to these accounts, opting instead to leverage them to falsify social proof.
Pivoting from Musk to Trump
While Musk has proven to be a successful figure for scammers in their pursuit of stealing cryptocurrency, they’ve recently begun experimenting, pivoting away from Musk to President Trump.
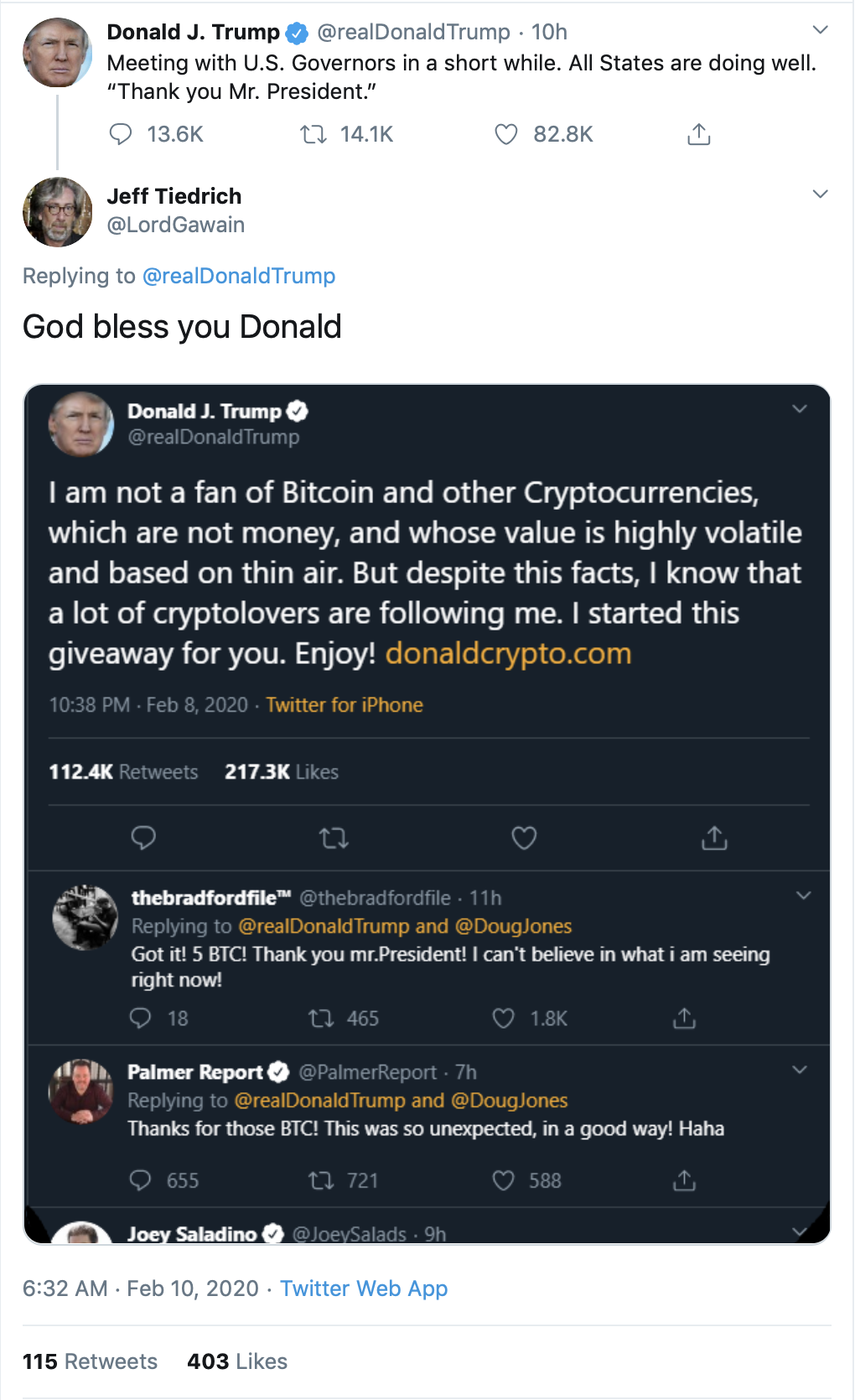
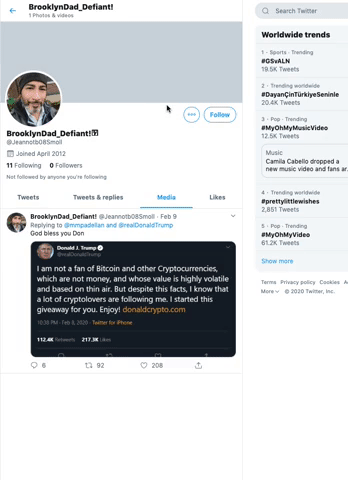
I spotted a tweet from an impersonator of Jeff Tiedrich, a Twitter user who regularly replies to the president’s tweets. The Tiedrich impersonator’s tweet said, “God bless you Donald,” and included a photoshopped tweet that appeared to be from the president. What’s interesting about this tweet is it’s not fully photoshopped. President Trump actually tweeted about Bitcoin and cryptocurrencies back in July 2019.
I am not a fan of Bitcoin and other Cryptocurrencies, which are not money, and whose value is highly volatile and based on thin air. Unregulated Crypto Assets can facilitate unlawful behavior, including drug trade and other illegal activity....
— Donald J. Trump (@realDonaldTrump) July 12, 2019
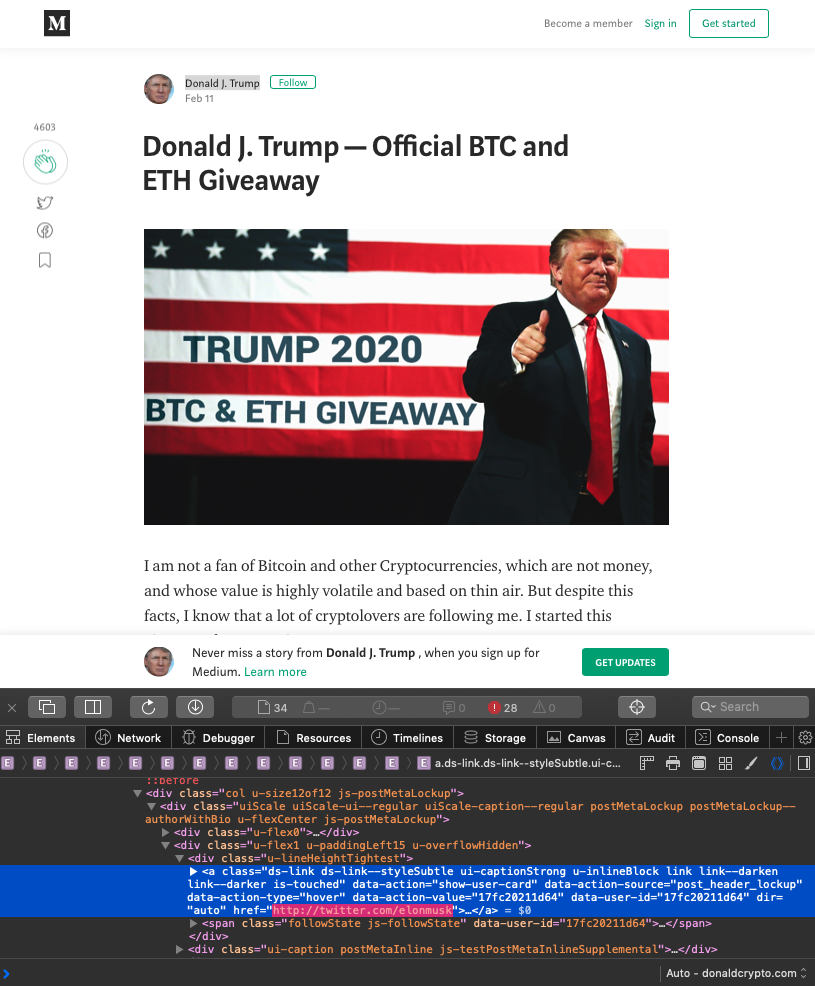
Scammers have apparently repurposed this tweet and modified it to make it seem like President Trump started a giveaway for his followers who are “cryptolovers.” The fabricated tweet also includes a link to a newly registered domain, donaldcrypto[.]com.
Impersonation of other figures
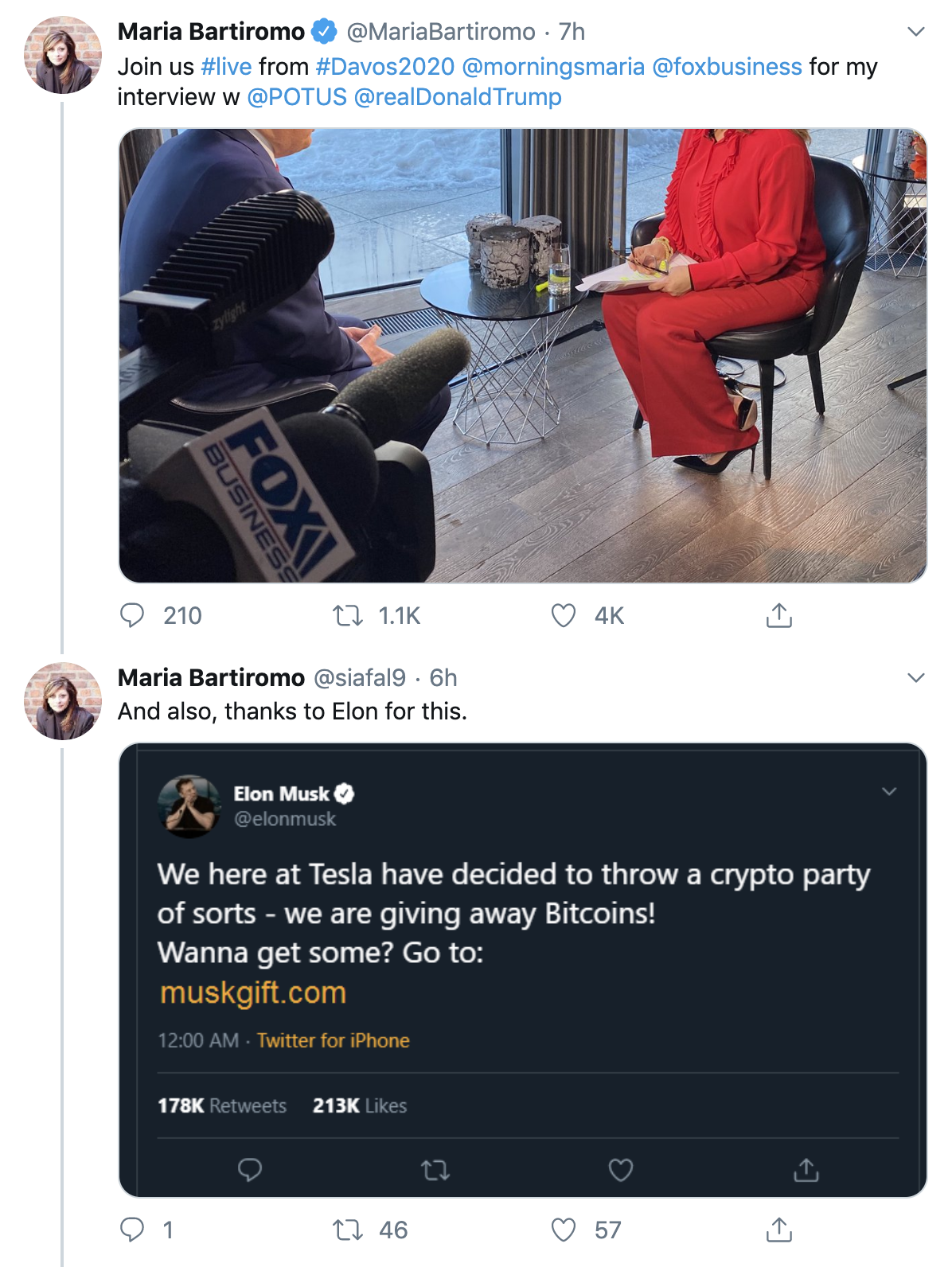
In addition to these impersonations, I’ve seen impersonations of political commentators and other political figures associated with Trump. For instance, scammers impersonated political commentator Maria Bartiromo in response to a tweet regarding her interview with President Trump, pushing the same Musk “crypto party” giveaway.
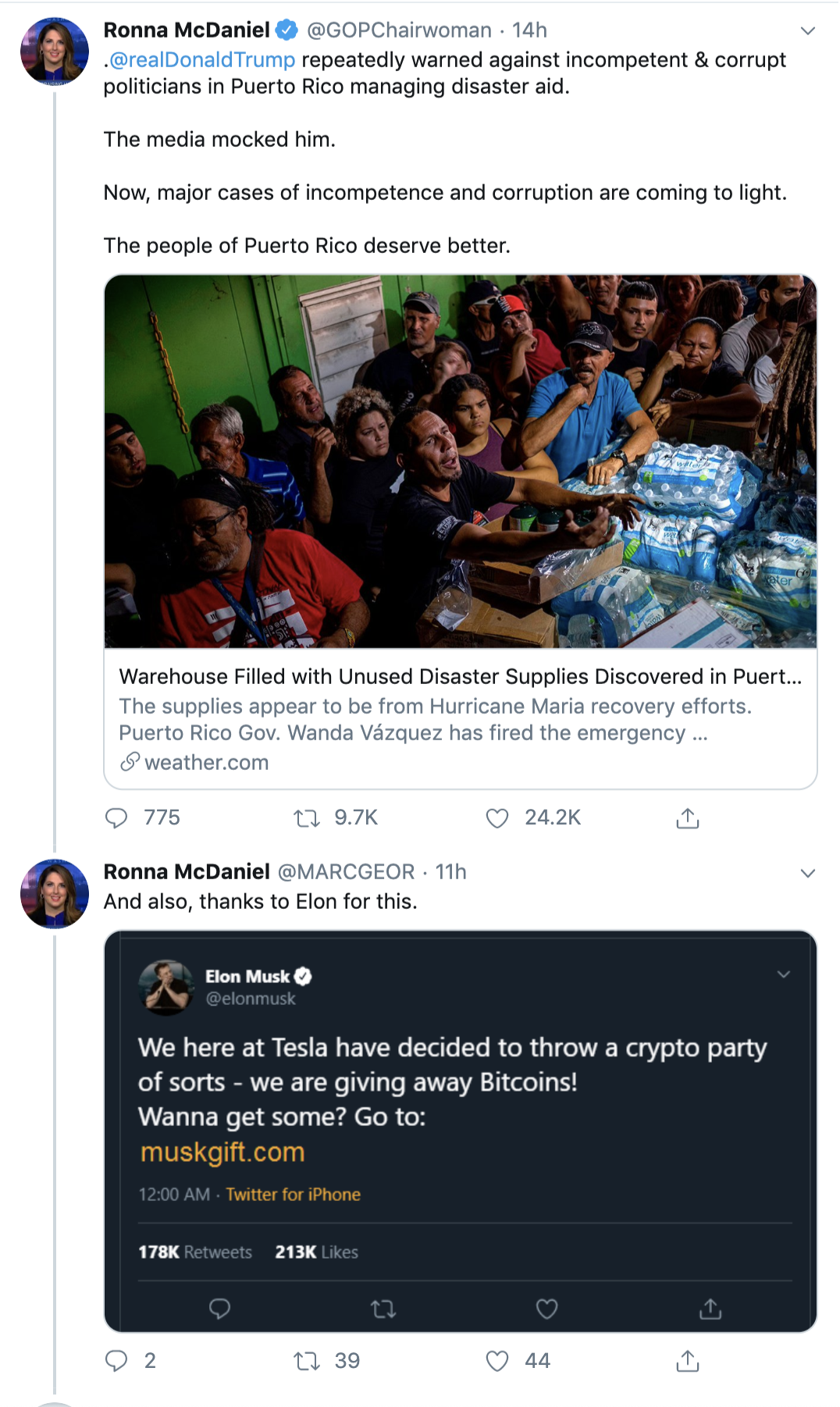
Additionally, I’ve seen scammers impersonate Ronna McDaniel, chairwoman of the Republican National Committee, promoting the same photoshopped tweet used by the Bartiromo impersonator.
Replying to other political figures
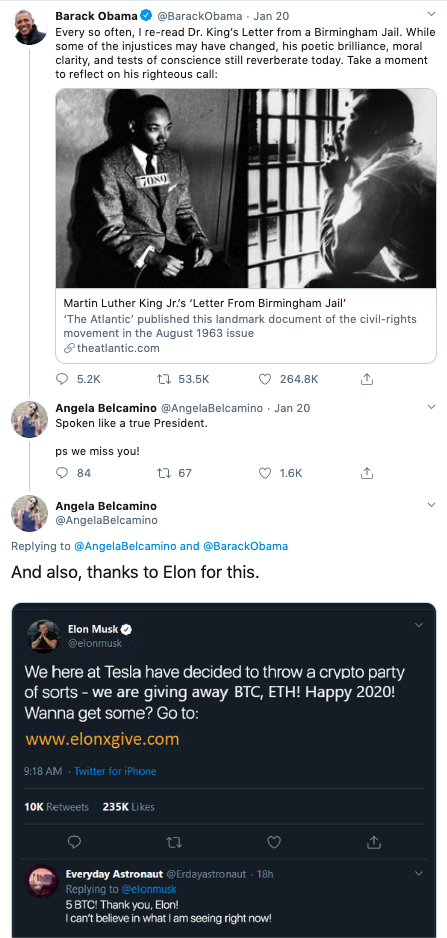
While many of these cryptocurrency scam tweets operate within replies to President Trump, I’ve also seen tweets directed at other political figures, such as former President Barack Obama, members of Congress, political commentators and others.
President Barack Obama
Rep. Jim Jordan
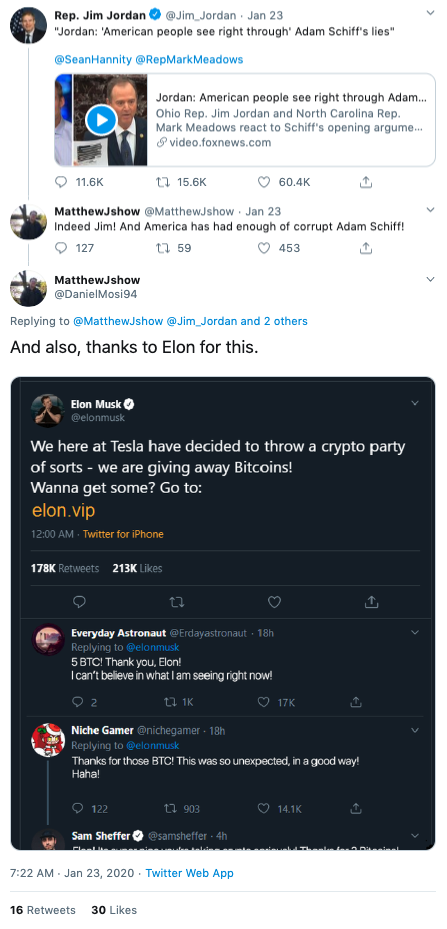
Entrepreneur and Political Activist Kim Dotcom
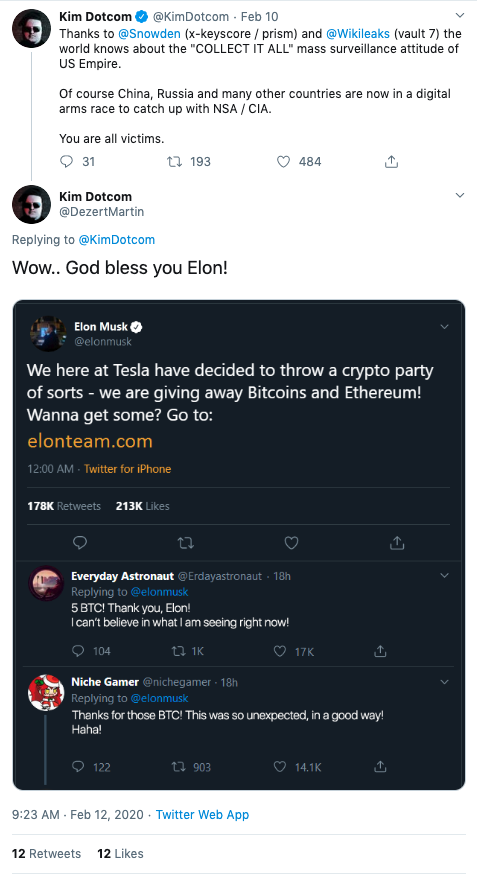
Political Commentator John Solomon
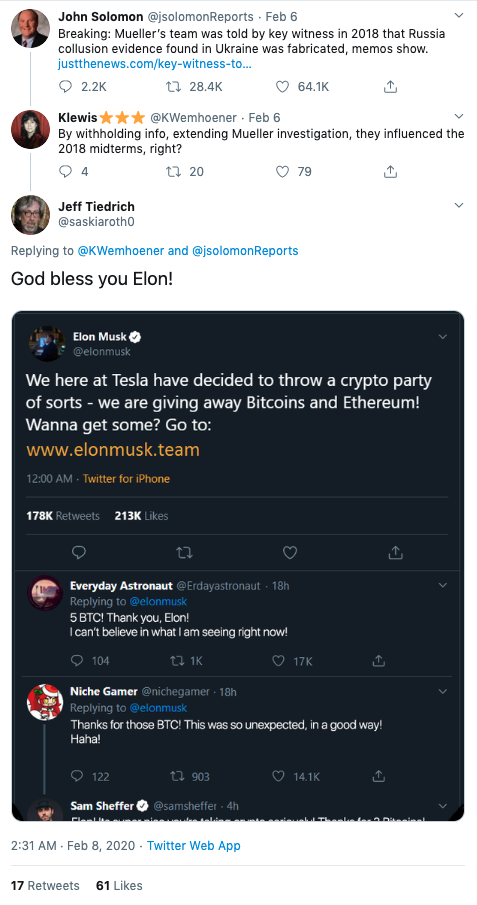
As you can see in the example above, not every impersonator responds directly to the person they’re impersonating. It’s unclear if this is intentional or a bug in the process.
Additional observations
Not all the tweets followed the same template. For instance, one of the tweets had a different image with text that didn’t match up with the style of a real tweet. In the example below, the photoshopped image looks shoddy, as it does not align with Twitter’s design aesthetic and may have been a rush job.
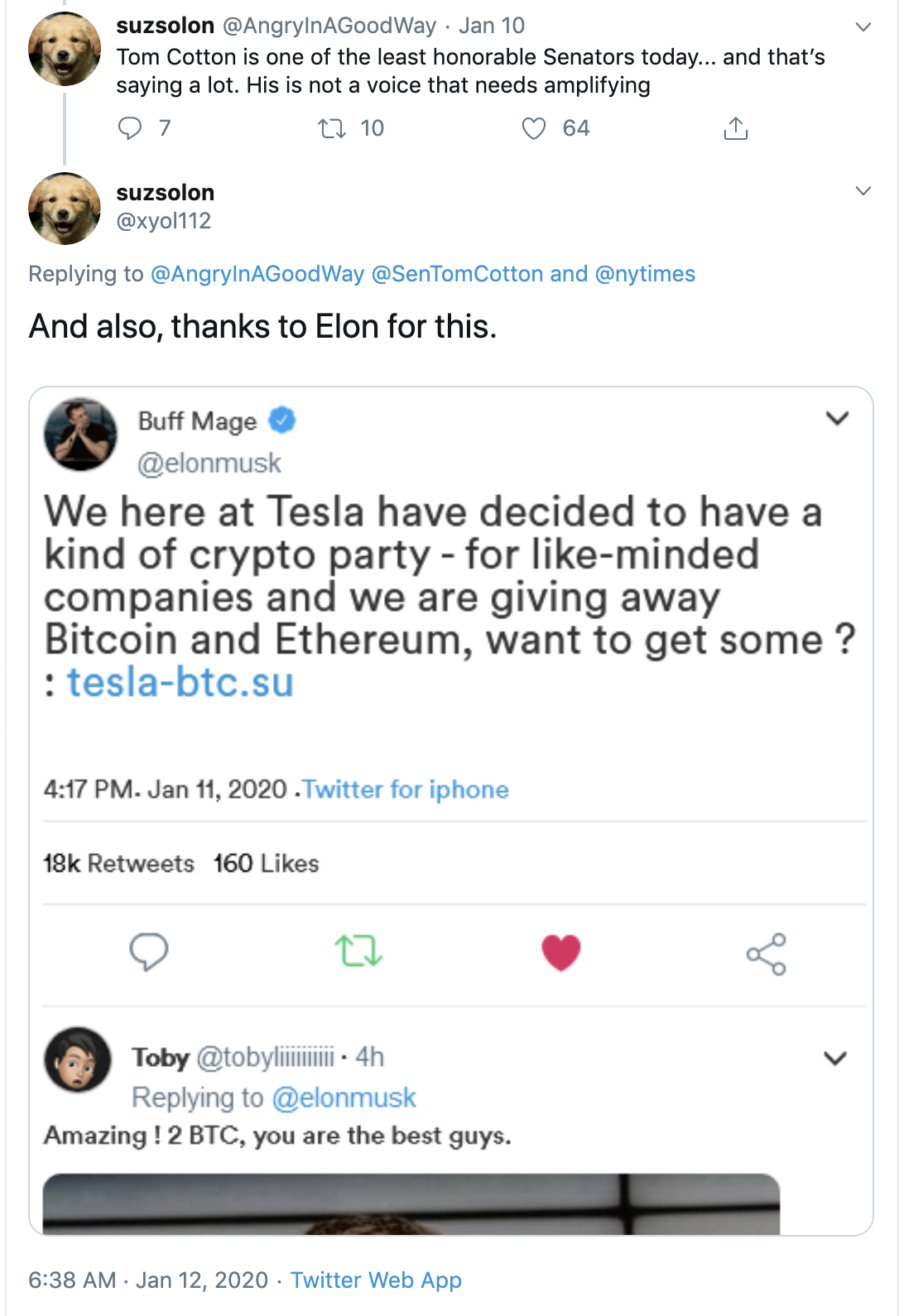
In some cases, the impersonation accounts aren’t actually impersonating when they respond. In the example below, the “Emre” account is responding to Jeff Tiedrich, but it appears the account was never modified to include the name and avatar of Tiedrich in order to operate as an impersonator.
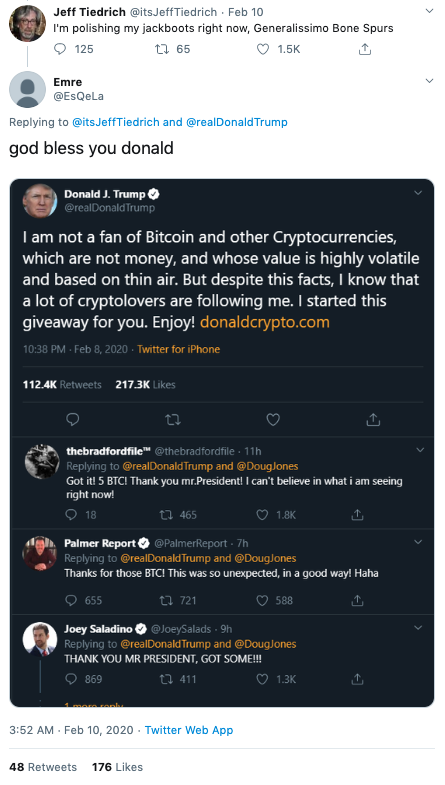
In some cases, I found the scammers would respond to their own tweets, either intentionally or unintentionally, which appears to me as some type of misconfiguration of whatever automated software the scammers are using to identify and respond to these tweets.
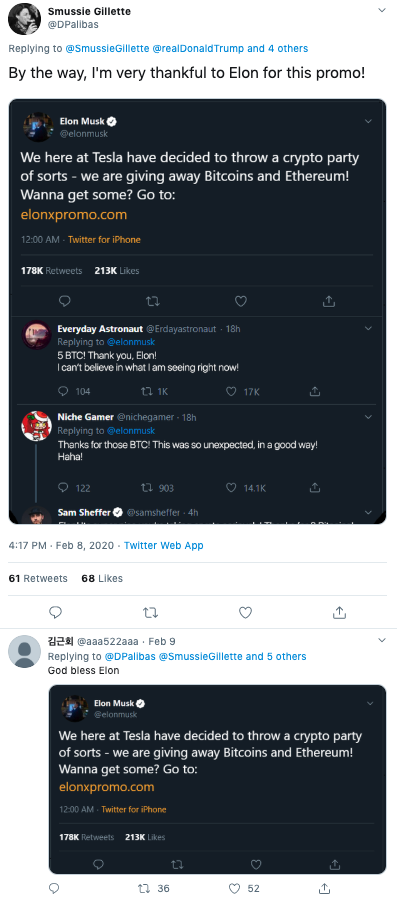
Lastly, I’ve seen instances where scammers tried to prop up these tweets with falsified social proof, but in doing so, they neglected to update their scripts.
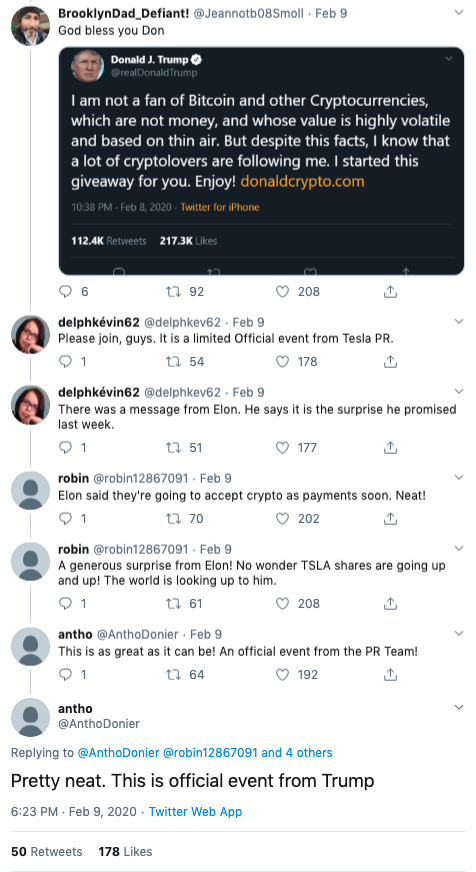
In the example above, several of the tweets reference Tesla PR and Elon even though the photoshopped image is of President Trump. Only the last tweet shown actually mentions President Trump (“Pretty neat. This is official event from Trump.”).
A continuous cat-and-mouse game
There has been a perpetual cat-and-mouse game between Twitter and cryptocurrency scammers since they appeared in 2018, as scammers try to evade detection and removal of their accounts. As a result, scammers keep modifying their tactics in a variety of ways.
In the beginning, direct impersonation of notable figures was the intention. The impersonators’ tweets would contain Bitcoin and Ethereum cryptocurrency addresses. To combat efforts to remove their accounts, the scammers would thread their tweets, talking about the supposed giveaway in the initial tweet, followed by a secondary tweet linking users to an external website instead of listing the Bitcoin or Ethereum cryptocurrency addresses directly. Eventually, they pivoted away from including links directly in their tweets, opting instead to post the URL in an image. Recently, the scammers switched to bypassing that entire process, creating photoshopped tweets of notable figures that contained a URL to the supposed giveaway page.
Fake Medium pages for cryptocurrency scams
For external websites, scammers lifted the template from the popular publishing platform, Medium, using it to promote the so-called “official” giveaways from Musk and President Trump.
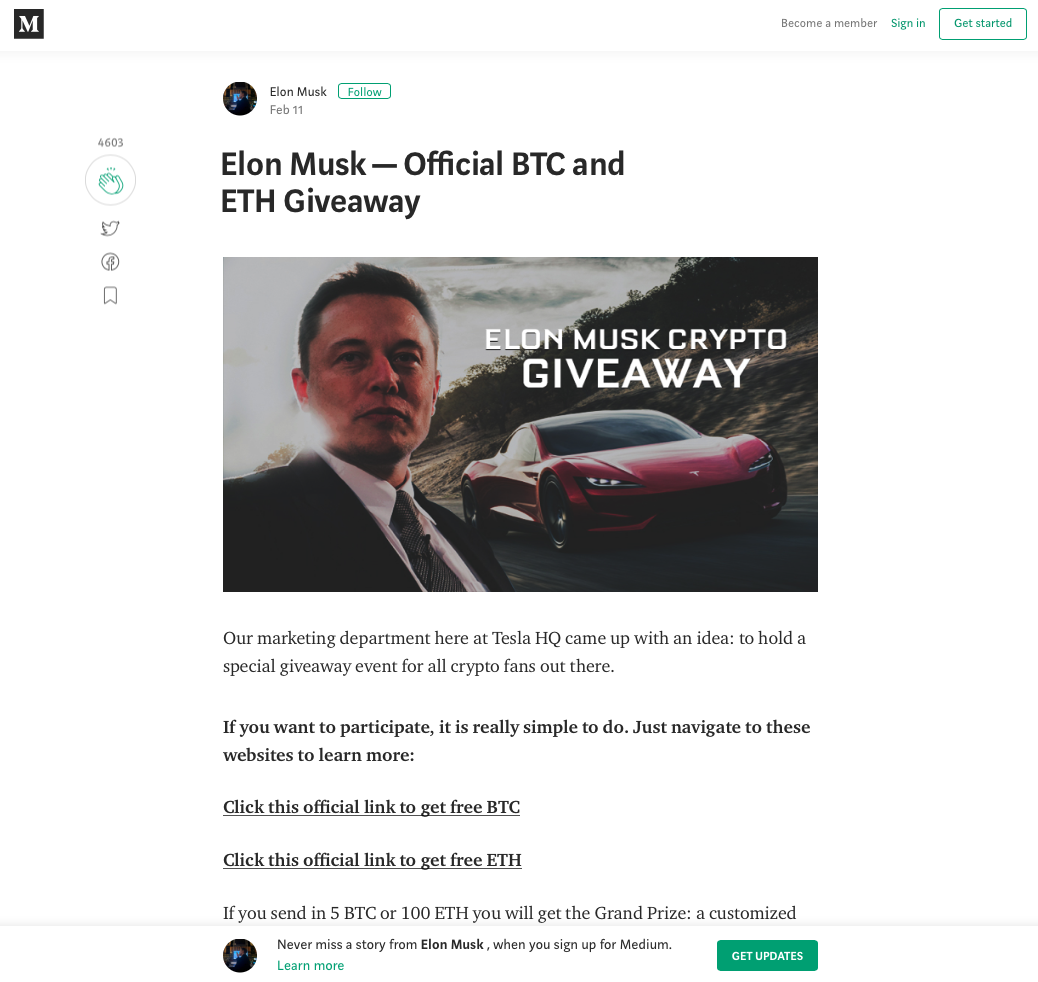
The scammers also create a fake “comment” section with posts from users claiming to have received Ethereum from the giveaway.
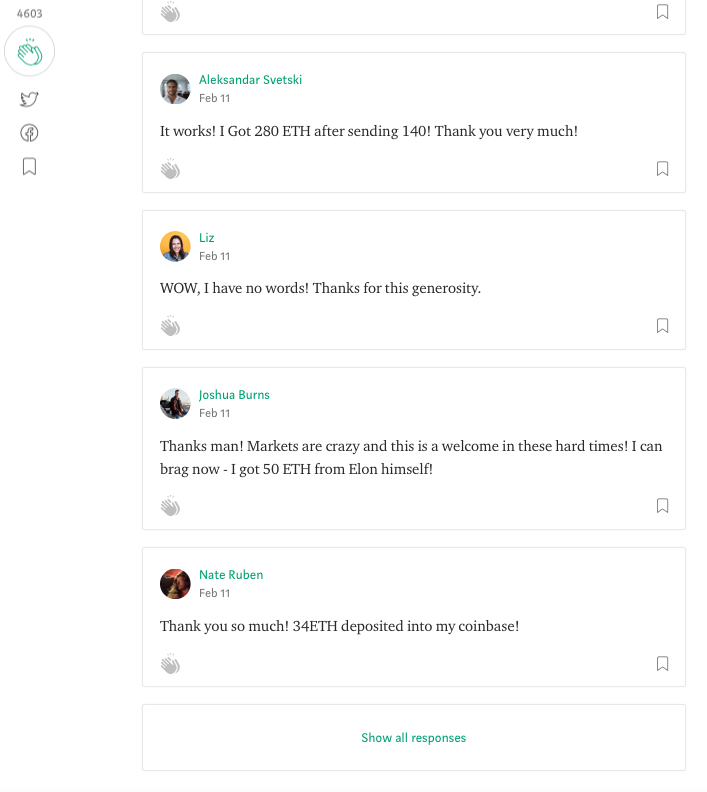
The same template was also used for the website, donaldcrypto.com. In this instance, the scammers forgot to update the link pointing to President Trump’s Twitter account, leaving it to point to Musk’s.
Verify address, double your cryptocurrency?
The principal part of the ruse is the scammers offer to double a user’s cryptocurrency. They ask users to send anywhere between 0.1 to 10 Bitcoin or Ethereum, promising to send them between 0.2 to 20 Bitcoin or Ethereum back. This is akin to the premise of “flipping,” which I talked about in my Cash App Friday scam blog series. The general concept is the same: You send money to “verify” yourself (or your cryptocurrency wallet address) and, in return, you receive more money than you sent. In this case, you supposedly double your cryptocurrency.
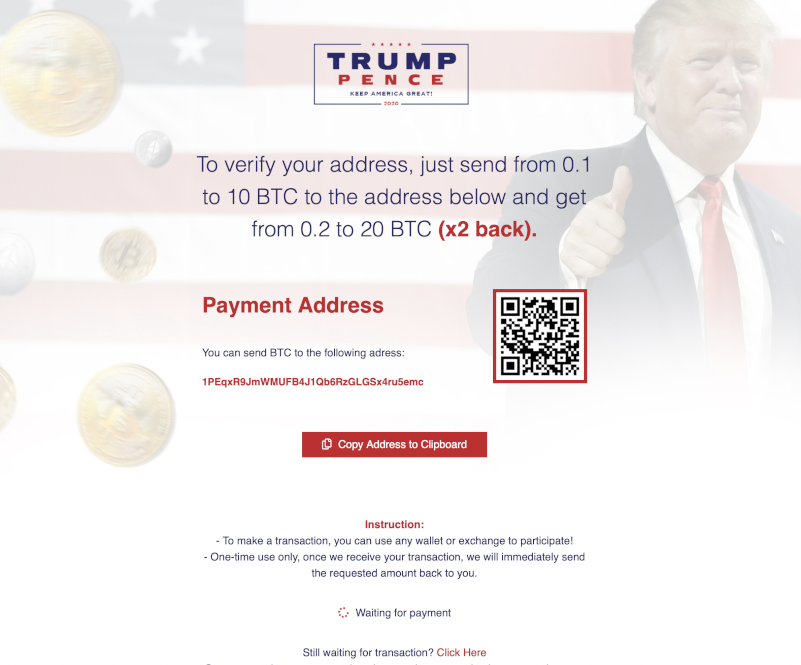
As you might expect, there is no giveaway. The promise of doubling your cryptocurrency is just a way for scammers to steal yours.
Impact of cryptocurrency scams
It’s hard to gauge the true impact of these scams based on the rotating cryptocurrency addresses and the potential for scammers to fake transactions by sending cryptocurrency to themselves. However, a recent Reddit thread shed light on a real example of a cryptocurrency enthusiast losing their cryptocurrency in one of these scams.
According to the thread, a user stumbled across one of these tweets containing a photoshopped tweet from Elon Musk. The user said they “frantically rushed” to send 0.4 Bitcoin, which was worth $3,000 at the time of the transaction, to the address. The user acknowledged that “after only a little digging it became very clear that I just got scammed.” Unfortunately, there are likely more cases like this that remain unreported.
Resist: Cryptocurrency scams persist
It’s clear from the previous example that there is enough incentive for scammers to continue to pursue these schemes on Twitter and other platforms, even if they don’t net large sums of cryptocurrency. So, we shouldn’t expect them to walk away anytime soon. They’re just participating in a continuous cat-and-mouse game with Twitter’s Trust & Safety team.
If you’re a Twitter user, you can help combat the scourge of scammers by reporting these fraudulent accounts to Twitter through their built-in reporting tools.
Here are a few options for reporting these accounts:
Report as Suspicious or Spam
Under the “It’s suspicious or spam” option, you can flag these scam accounts as “sharing links to potentially harmful, malicious or phishing sites.” Since they’re promoting photoshopped tweets with links in them, this is a great option.
Report as Impersonation
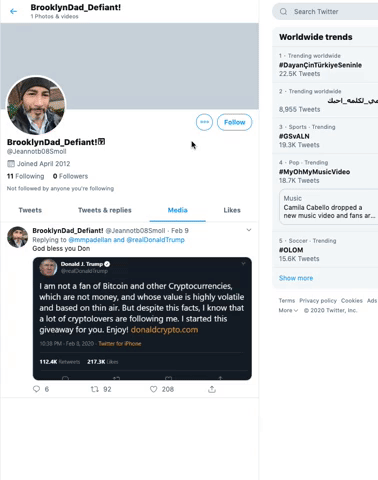
The other option is to report the accounts as impersonators. Navigate to the option “They’re pretending to be me or someone else” and specify that they’re impersonating someone else. It’s also helpful to have the username of the account being impersonated. In the case above, scammers are impersonating @mmpadellan. Adding that context will help Twitter when reviewing your report.
When asked what people can do, Musk himself encouraged reporting these accounts “as soon as you see it.”
Report as soon as you see it. Troll/bot networks on Twitter are a *dire* problem for adversely affecting public discourse & ripping people off. Just dropping their prominence as a function of probable gaming of the system would be a big improvement.
— Elon Musk (@elonmusk) February 1, 2020
Because this remains a game of cat and mouse, the x-factor in all this is the Twitter community. It’s up to Twitter users to participate in keeping the platform free from these scammers because as long as there is money to be made, they’re going to keep iterating and finding new ways to peddle their scams.