by Cody Dumont
July 28, 2025
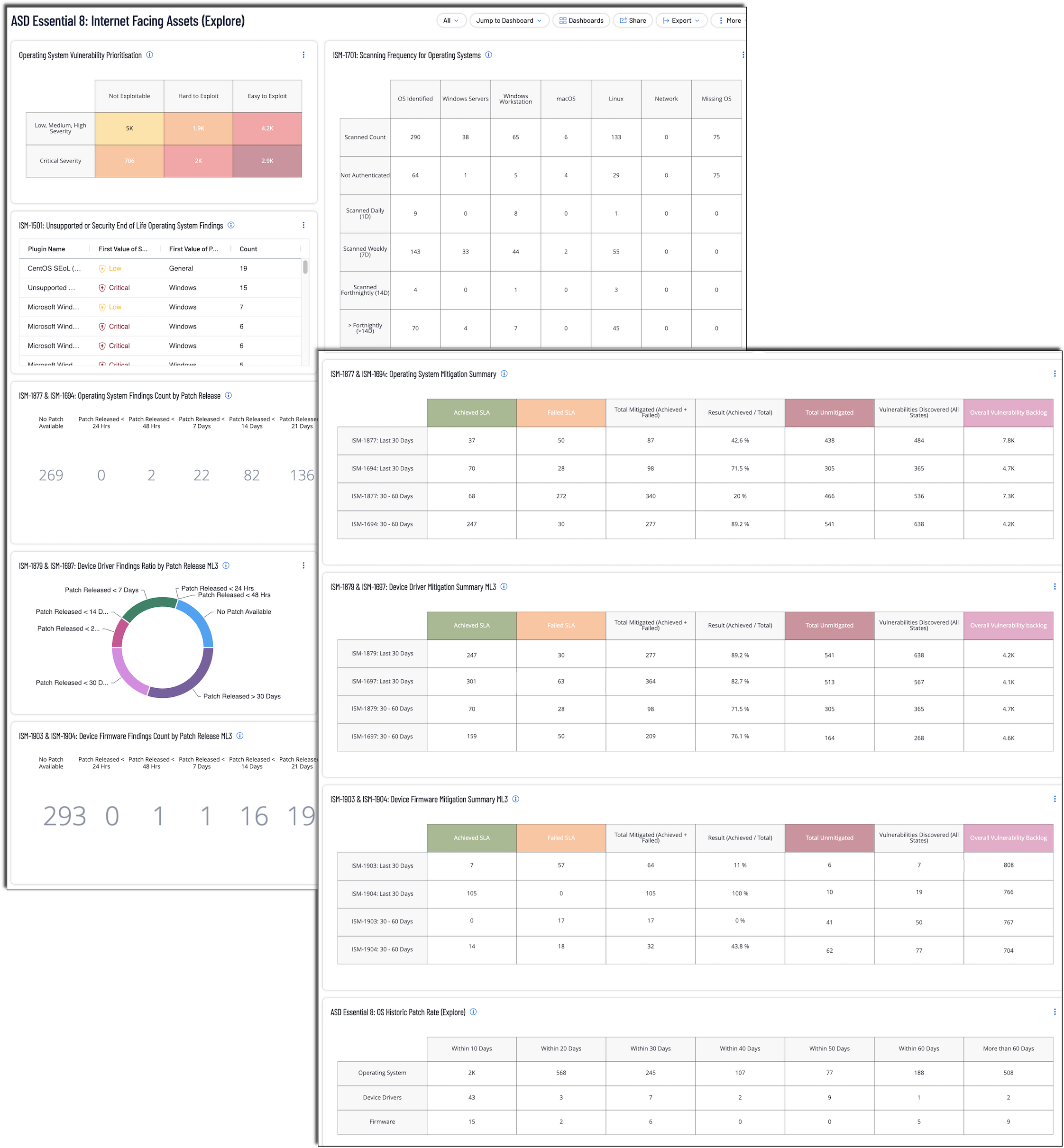
The ASD Essential 8: Internet Facing Assets dashboard is designed to support organisations in implementing and monitoring the Essential Eight Strategies for mitigating cybersecurity risks. This comprehensive dashboard provides actionable insights into asset discovery, patch management, compliance, and exploitability to ensure a robust security posture across applications.
The Australian Cyber Security Centre (ACSC) under the Australian Signals Directorate (ASD) provides guidance to address targeted cybersecurity intrusions through its Strategies to Mitigate Cyber Security Incidents. Among these, the Essential Eight describes the minimum set of preventative cybersecurity measures organisations should implement. This guidance, complemented by the Information Security Manual (ISM) controls, forms a robust framework to ensure the confidentiality, integrity, and availability of information technology and operational technology systems. This dashboard aligns with these controls to provide critical insights into the implementation of the Essential Eight.
The ISM designates two categories for patch operating systems, they are: internet-facing and non-internet-facing. Per the ISM, an internet-facing asset (server, network equipment, etc) is any asset that is directly accessible over the internet. Each of the categories is separated into three patch classifications, they are: operating system, device drivers, and firmware. To identify the three classifications, Tenable security engineering working with partners identified three properties that reliably identified the finding in question, they are: plugin name, common platform enumeration (CPE) string, and the solution property. The ISM's covered by this dashboard are:ISM-1501, ISM-1694, ISM-1697, ISM-1701, ISM-1877, ISM-1879, ISM-1903, and ISM-1904.
The ASD's Blueprint for Secure Cloud Patch Operating Systems (https://blueprint.asd.gov.au/security-and-governance/essential-eight/patch-os/) provides recommendations with respect to how the assets should be scanned and evaluated. The blueprint discusses scanning strategies, maturity levels, and other aspects of a healthy exposure management program. While the recommendations provided by the blueprint do not provide specific guidance, the samples help illustrate a healthily Exposure Management program. The dashboard brings together information that provides evidence of the material impact to the organisations risk exposure.
To maximize relevance, organisations should leverage Asset Tagging. This feature ensures that the dashboard can be filtered to focus on data critical to implementing the Essential Eight. Tagging assets differentiation for stricter service-level agreements (SLAs). For example, critical business systems may require stricter consideration, while other systems may have a longer patching window. Asset tags, composed of Category:Value pairs (e.g., Connectivity:Internet Facing), can be applied manually or automatically using filtering rules such as public IP ranges, open ports (e.g., 80, 443), or cloud metadata. This categorisation simplifies monitoring and prioritisation for Essential Eight compliance, ensuring that organisations address vulnerabilities in their most critical assets. Tagging by application risk level (e.g., High Risk, Low Risk) or system role further enhances visibility. For more details, refer to Tenable's Tagging Documentation.
The Tenable One Platform combines a suite of sensors to facilitate efficient vulnerability scanning, regardless of network complexity. By leveraging Tenable's capabilities, organisations can effectively discover, assess, and understand their attack surface, gaining comprehensive insights into exposure points. This is coupled with Exposure Response features that prioritise remediation efforts based on contextual risk. The dashboard includes critical features to highlight asset discovery, identify unsupported systems, monitor patch management timelines, track compliance rates, and classify exploitable vulnerabilities, ensuring comprehensive coverage of the Essential Eight. By combining Tenable's comprehensive vulnerability scanning, exposure insights, and asset prioritisation with the ASD's Essential Eight Strategies. By using the dashboard in conjunction with ISM controls and asset tagging, organisations can enhance their cybersecurity maturity, address vulnerabilities more effectively, and ensure compliance with Australia's cybersecurity standards.
Widgets
- Operating System Vulnerability Prioritisation - This widget provides a detailed breakdown of vulnerabilities in operating systems based on their severity (Low, Medium, High, and Critical) and exploitability ease. Exploitability is determined using the CVSSv3 Attack Complexity metric, where vulnerabilities with 'High' complexity are categorized as 'Hard to Exploit,' and others are labelled as 'Easy to Exploit.' The widget also identifies vulnerabilities that are 'Not Exploitable.' This matrix enables organisations to prioritize patching efforts by focusing on vulnerabilities with lower attack complexity (easy to exploit) while addressing critical vulnerabilities that could pose significant risks.
- ASD Essential 8: Scanning Frequency for Operating Systems - This widget uses asset tags to set the correct content and assists organisations in achieving compliance with Australia Signal Directive (ASD) Information Security Manual 1701 (ISM-1701) and ISM-1702. This widget monitors vulnerability scanning on internet-facing devices or non-internet-facing devices, to ensure scans are conducted daily, in compliance with ISM-1701 or ISM-1702. ISM-1701 requires Internet-facing devices to be scanned daily, resulting in rapid identification of security weaknesses, enabling timely remediation and helping organisations meet Essential Eight maturity requirements. ISM-1702 requires vulnerability scanning at least fortnightly (14 days) to identify missing patches or updates for vulnerabilities in non-internet-facing assets.
- ASD Essential 8: Unsupported or Security End of Life Operating System Findings - This table displays top 200 unsupported applications by plugin name, sorted by count. Displayed is the plugin name, plugin family, severity and the total findings. This widget identifies unsupported applications by the 'unsupported_by_vendor' definition and wildcard 'cpe:/o' CPE field. Unsupported software is any application, or operating system that is no longer maintained by the vendor. Unsupported software will typically no longer receive any updates, and will lack support. Organizations with unsupported software may be exposing themselves to security, operational, and compliance risks. The information in this table assists organisations in achieving compliance with Australia Signal Directive (ASD) Information Security Manual 1501 (ISM-1501). These ISM apply to Maturity Levels 1 - 3 and require software products that are no longer supported by vendors are removed.
- ASD Essential 8: Operating System Findings Count by Patch Release - The sections of this chart provide a ratio view of the findings within the organisation. The leadership teams are able to use this view to understand the relative work needed to address the different patch categories. This widget monitors the publication of security patches for internet-facing and non-internet-facing servers and network devices, aligned with relevant ISM controls. For internet-facing assets ISM-1877 mandates that critical or exploitable patches be deployed within 48 hours, and ISM-1694 requires management of non-critical patches within two weeks. ISM-1695 (ML1 & ML2) focuses on non internet-facing asset vulnerability mitigation within 1 month of detection. ISM-1696 and ISM-1902, both Maturity Level 3 requirements, provide further guidance on patching practices and deployment monitoring for non internet-facing assets based on criticality and exploitability. By tracking adherence to these timelines, the widget helps organisations reduce risk and maintain compliance with Essential Eight maturity standards for critical infrastructure.
- ASD Essential 8: Operating System Findings Ratio by Patch Release - Using Asset tags to set the correct context, ASD Essential 8: Operating System Findings Ration by Patch Release widget tracks the timely publication and deployment of security patches for operating systems based on their criticality and exploitability. The sections of this chart provide a ratio view of the findings within the organisation. The leadership teams are able to use this view to understand the relative work needed to address the different patch categories. This widget monitors the publication of security patches for internet-facing and non-internet-facing servers and network devices, aligned with relevant ISM controls. For internet-facing assets ISM-1877 mandates that critical or exploitable patches be deployed within 48 hours, and ISM-1694 requires management of non-critical patches within two weeks. ISM-1695 (ML1 & ML2) focuses on non internet-facing asset vulnerability mitigation within 1 month of detection. ISM-1696 and ISM-1902, both Maturity Level 3 requirements, provide further guidance on patching practices and deployment monitoring for non internet-facing assets based on criticality and exploitability. By tracking adherence to these timelines, the widget helps organisations reduce risk and maintain compliance with Essential Eight maturity standards for critical infrastructure.
- ASD Essential 8: Device Driver Findings Ratio by Patch Release ML3 - This tracks the timely publication and deployment of security patches for drivers based on their criticality and exploitability. The sections of this chart provide a ratio view of the findings within the organisation. The leadership teams are able to use this view to understand the relative work needed to address the different patch categories. The information in this widget assists organisations in achieving compliance with Australia Signal Directive (ASD) Information Security Manual 1879 (ISM-1879) and ISM-1697. The ISM applies to Maturity Levels 3. To be compliant with the ISM, the patches addressing critical vulnerabilities must be deployed within 48 hours, while patches for non-critical vulnerabilities must be deployed within one month. By providing visibility into patch status and compliance with these timelines, the widget helps organisations maintain secure drivers and reduce risks associated with unpatched device drivers.
- ASD Essential 8: Device Driver Findings Count by Patch Release ML3 - This tracks the timely publication and deployment of security patches for drivers based on their criticality and exploitability. The first cell provides a count of findings that are present without a vendor released patch or mitigation strategy. The values in the remaining cells provide a count of findings that have not been mitigated after a patch has been released from the vendor. The information in this widget assists organisations in achieving compliance with Australia Signal Directive (ASD) Information Security Manual 1879 (ISM-1879) and ISM-1697. The ISM applies to Maturity Levels 3. To be compliant with the ISM, the patches addressing critical vulnerabilities must be deployed within 48 hours, while patches for non-critical vulnerabilities must be deployed within one month. By providing visibility into patch status and compliance with these timelines, the widget helps organisations maintain secure drivers and reduce risks associated with unpatched device drivers.
- ASD Essential 8: Operating System Findings by Patch Publication Date - This tracks the timely publication and deployment of security patches for firmware based on their criticality and exploitability. The first cell provides a count of findings that are present without a vendor released patch or mitigation strategy. The values in the other cells provide a count of findings that have not been mitigated after a patch has been released from the vendor. The information in this widget assists organisations in achieving compliance with Australia Signal Directive (ASD) Information Security Manual 1903 (ISM-1903) and ISM-1904. The ISM applies to Maturity Levels 3. To be compliant with the ISM, the patches addressing critical vulnerabilities must be deployed within 48 hours, while patches for non-critical vulnerabilities must be deployed within one month. By providing visibility into patch status and compliance with these timelines, the widget helps organisations maintain secure firmware and reduce risks associated with unpatched device firmware.
- ASD Essential 8: Asset Firmware Findings Ratio by Patch Release ML3 - This tracks the timely publication and deployment of security patches for firmware based on their criticality and exploitability. The sections of this chart provide a ratio view of the findings within the organisation. The leadership teams are able to use this view to understand the relative work needed to address the different patch categories. The information in this widget assists organisations in achieving compliance with Australia Signal Directive (ASD) Information Security Manual 1903 (ISM-1903) and ISM-1904. The ISM applies to Maturity Levels 3. To be compliant with the ISM, the patches addressing critical vulnerabilities must be deployed within 48 hours, while patches for non-critical vulnerabilities must be deployed within one month. By providing visibility into patch status and compliance with these timelines, the widget helps organisations maintain secure firmware and reduce risks associated with unpatched device firmware.
- ASD Essential 8: Device Internet Facing OS Mitigation Summary - By using the applied asset tags, ASD Essential 8: Device Internet Facing OS Mitigation Summary widget assists organisations in achieving compliance with Australia Signal Directive (ASD) Information Security Manual 1877 (ISM-1877) and ISM-1694. The ISM applies to Maturity Levels 1 - 3. ISM-1877 requires that critical patches be deployed within 48 hours, while ISM-1694 requires non-critical patches to be deployed within two weeks. The matrix is broken down into groups of rows, the top two rows are for findings discovered in the last 30 days, and the bottom two rows are findings from 30 to 60 days. This view allows the leadership and auditors the ability to track progress over time. The first 4 columns track the SLA as required by the ISM, the last 3 columns show the unmitigated in the same timeframes and vulnerabilities past the timeframe.
- ASD Essential 8: Device Driver Mitigation Summary - This widget assists organisations in achieving compliance with Australia Signal Directive (ASD) Information Security Manual 1879 (ISM-1879) and ISM-1697. This widget monitors the deployment of security patches for operating system drivers, aligned with ISM-1879 and ISM-1697, which are Maturity Level 3 requirements. Patches for critical vulnerabilities must be published within 48 hours, while patches for non-critical vulnerabilities are to be deployed within one month. By tracking adherence to these timelines, the widget supports organisations in maintaining secure, up-to-date OS drivers and reducing the risk of exploitation. The matrix is broken down into groups of rows, the top two rows are for findings discovered in the last 30 days, and the bottom two rows are findings from 30 to 60 days. This view allows the leadership and auditors the ability to track progress over time. The first 4 columns track the SLA as required by the ISM, the last 3 columns show the unmitigated in the same timeframes and vulnerabilities past the timeframe.
- ASD Essential 8: Device Firmware Mitigation Summary - This widget assists organisations in achieving compliance with Australia Signal Directive (ASD) Information Security Manual 1903 (ISM-1903) and ISM-1904. This widget tracks the deployment of security patches for device firmware in alignment with ISM-1903 and ISM-1904, which are Maturity Level 3 requirements. To be compliant with the ISM, the patches addressing critical vulnerabilities must be deployed within 48 hours, while patches for non-critical vulnerabilities must be deployed within one month. By providing visibility into patch status and compliance with these timelines, the widget helps organisations maintain secure firmware and reduce risks associated with unpatched device firmware. The matrix is broken down into groups of rows, the top two rows are for findings discovered in the last 30 days, and the bottom two rows are findings from 30 to 60 days. This view allows the leadership and auditors the ability to track progress over time. The first 4 columns track the SLA as required by the ISM, the last 3 columns show the unmitigated in the same timeframes and vulnerabilities past the timeframe.