by David Schwalenberg
March 31, 2015
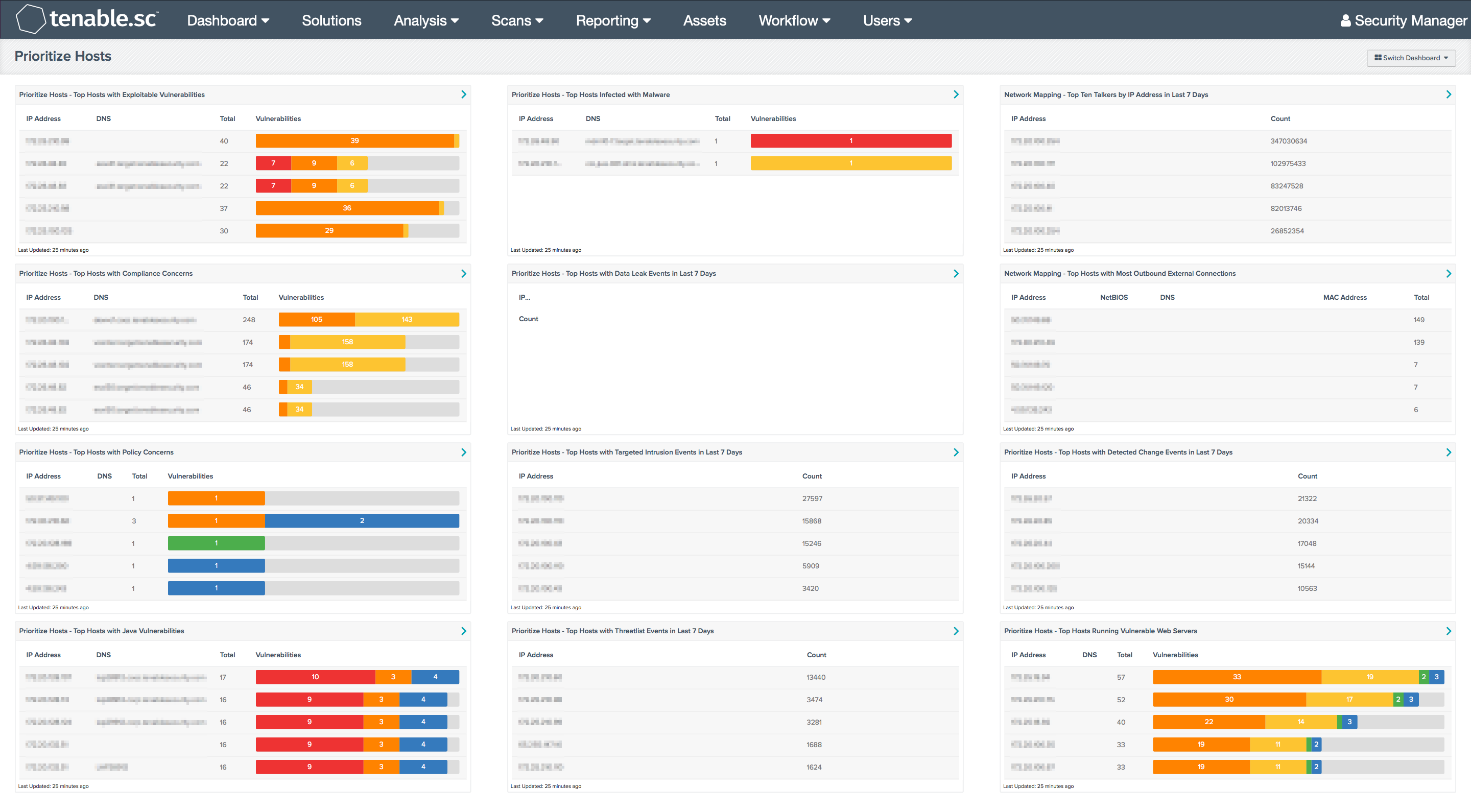
What systems need attention now? What systems can be safely ignored for the time being? System administrators often have so much to do that it can be difficult for them to prioritize their host administration and mitigation efforts. This dashboard can assist in that prioritization by presenting multiple top ten lists of hosts in various categories, such as most vulnerable, most infected with malware, most policy violations, most out of compliance, most detected changes, etc. The components on this dashboard make use of active scan information from Nessus, passive scan information from the Nessus Network Monitor (NNM), and event data from the Log Correlation Engine (LCE). In this way, a system administrator can obtain the most comprehensive and integrated view of the network, in order to make the best prioritization decisions about administration and mitigation efforts.
This dashboard contains many helpful lists of hosts, but a system administrator may want to prioritize hosts based on a different criteria. Several of the components on this dashboard contain suggestions in their descriptions on how to modify the components to generate additional lists of hosts, if desired. The system administrator can thus customize this dashboard to best help in prioritization decisions.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Monitoring.
The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.10.0
- NNM 5.11.0
- LCE 6.0.3
Prioritizing administration and mitigation efforts also involves risk management. Risk is the potential that a threat will exploit a vulnerability to cause harm to an organization. An organization that does not properly manage risk may incur substantial losses because mitigation efforts are focused in the wrong areas. The Understanding Risk dashboard can assist an organization in understanding and managing their risk.
Tenable's Tenable.sc Continuous View (Tenable.sc CV) is the market-defining continuous network monitoring platform. Tenable.sc CV includes active vulnerability detection with Nessus and passive vulnerability detection with Tenable's Nessus Network Monitor(NNM), as well as log correlation with Tenable's Log Correlation Engine (LCE). Using Tenable.sc CV, an organization will obtain the most comprehensive and integrated view of its network, in order to best prioritize its administration and mitigation efforts.
Listed below are the included components:
- Prioritize Hosts - Top Hosts with Exploitable Vulnerabilities - This table displays the top hosts on the network that have the most severe exploitable vulnerabilities. The list is sorted so that the most vulnerable host is at the top. A count of exploitable vulnerabilities and a bar graph indicating the severity of the vulnerabilities are given for each host. Use this table to determine the most vulnerable hosts on the network.
- Prioritize Hosts - Top Hosts with Compliance Concerns - This table displays the top hosts on the network that have either compliance failures or compliance checks that must be performed manually. The list is sorted so that the host with the worst compliance concerns is at the top. A count of compliance concerns and a bar graph indicating the severity of the concerns are given for each host. Use this table to determine the hosts most out of compliance on the network.
- Prioritize Hosts - Top Hosts with Policy Concerns - This table displays the top hosts on the network that have actively or passively detected policy concerns or violations such as game or social network activity. The list is sorted so that the host with the worst policy concerns is at the top. A count of policy concerns and a bar graph indicating the severity of the concerns are given for each host. Use this table to determine the hosts with the most policy violations on the network.
- Prioritize Hosts - Top Hosts with Java Vulnerabilities - This table displays the top hosts on the network that have actively or passively detected Java vulnerabilities. The list is sorted so that the host with the worst Java vulnerabilities is at the top. A count of vulnerabilities and a bar graph indicating the severity of the vulnerabilities are given for each host. Use this table to determine the hosts with the most Java vulnerabilities on the network. In the component filter, the Plugin Name is set to the "java" keyword to find those plugins that detect Java vulnerabilities. This component can be copied and other keywords used to detect other types of vulnerabilities. Some keyword suggestions are "adobe", "unsupported", "default", "malicious process", and "xss".
- Prioritize Hosts - Top Hosts Infected with Malware - This table displays the top hosts on the network that have actively or passively detected malware infections. The list is sorted so that the host with the worst malware problem is at the top. A count of malware detections and a bar graph indicating the severity of the malware are given for each host. Use this table to determine the hosts with the biggest malware problems on the network.
- Prioritize Hosts - Top Hosts with Data Leak Events in Last 7 Days - This table displays the top hosts on the network that had data leak events detected in the last 7 days. These events are normalized under the "data-leak" event type, and include events forwarded via syslog from NNM. The list is sorted so that the host with the most data leak events is at the top. Use this table to determine the hosts with the biggest data leakage problems on the network.
- Prioritize Hosts - Top Hosts with Targeted Intrusion Events in Last 7 Days - This table displays the top hosts on the network that had targeted intrusion events detected in the last 7 days. The list is sorted so that the host with the most targeted intrusion events is at the top. A targeted intrusion is an intrusion attack that targeted systems and ports likely to be exploited by the attack. Use this table to determine the hosts with the most dangerous intrusion attack problems on the network.
- Prioritize Hosts - Top Hosts with Threatlist Events in Last 7 Days - This table displays the top hosts on the network that interacted with malicious IP addresses (such as IPs that are part of a botnet) in the last 7 days. These events are normalized under the "threatlist" event type, and include events forwarded via syslog from NNM. The list is sorted so that the host with the most threatlist events is at the top. Use this table to determine hosts on the network that are part of a botnet or that connect to IP addresses with a known hostile reputation. In the component filter, the event Type is set to "threatlist" to find the threatlist events. This component can be copied and other event types can be used to filter on other events. Some event type suggestions are "virus", "intrusion", "scanning", "login-failure", "access-denied", and "web-error". The LCE also analyzes event trends and triggers secondary events in order to highlight unusual activity. Event types can also be used to filter on these secondary events. Some event type suggestions are "stats" (statistical anomalies in event trends), "continuous" (event trend indicates long-term activity), and "indicator" (a suspicious sequence of events has occurred).
- Network Mapping - Top Ten Talkers by IP Address in Last 7 Days - This table presents host information for the top ten most active systems on the network in the last seven days based on the number of network traffic events generated. LCE records network traffic events from the Tenable Network Monitor and the Tenable NetFlow Monitor; the most active hosts will have the highest counts of these events. The table is sorted so that the system with the highest count of events is at the top. This information can assist an organization in tracking normal activity, as well as discovering any unusual activity.
- Network Mapping - Top Hosts with Most Outbound External Connections - This table presents information on those hosts with the most passively detected outbound external connections. The table is sorted so that the host with the highest count of detections is at the top. This information can assist an organization in understanding who is talking to whom, as well as detecting any unauthorized or suspicious host connections. The Total column displays the number of detections. This number of detections may be greater than the number of external hosts to which this host is connecting, as multiple connections to the same host may have been detected. Note that only passively detected outbound external host connections will be displayed, and this may not include all possible external connections.
- Prioritize Hosts - Top Hosts with Detected Change Events in Last 7 Days - This table displays the top hosts on the network that had changes detected in the last 7 days. These events are normalized under the "detected-change" event type, and include events forwarded via syslog from NNM. The list is sorted so that the host with the most detected-change events is at the top. Use this table to determine hosts on the network on which changes happened; any unauthorized changes should be investigated.
- Prioritize Hosts - Top Hosts Running Vulnerable Web Servers - This table displays the top hosts on the network that are running vulnerable web servers. The vulnerabilities are detected both actively and passively. The list is sorted so that the host running the most vulnerable web server is at the top. A count of vulnerabilities and a bar graph indicating the severity of the vulnerabilities are given for each host. Use this table to determine the hosts running the most vulnerable web servers on the network. In the component filter, the Plugin Family is set to the active and passive Web Servers families to find those plugins that detect web server vulnerabilities. This component can be copied and other plugin families can be used to detect other types of vulnerable devices. Some plugin family suggestions are Databases, Firewalls, SCADA, Cisco, and local security checks for various operating systems.