by David Schwalenberg
November 5, 2014
The most recent version of IRS Publication 1075 – Tax Information Security Guidelines for Federal, State, and Local Agencies took effect on January 1, 2014, and provides thorough guidance for organizations that deal with Federal Taxpayer Information (FTI). Not only does Publication 1075 outline the technical and physical security requirements, but it also details incident response and data disclosure requirements. According to Publication 1075, the FTI guidelines not only apply to the organization receiving FTI; they also apply to contractors or consolidated data centers that may come into contact with the FTI as well. This means that organizations need to take a comprehensive approach to securing this sensitive information.
This dashboard focuses on IRS Publication 1075. Tenable’s Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring platform, which includes active vulnerability detection with Nessus, passive vulnerability detection with the Nessus Network Monitor (NNM), and log correlation with the Log Correlation Engine (LCE). Tenable.sc CV assists organizations in discovering compliance and vulnerability concerns on the network, assessing their impact, reporting on the results, and taking action to remediate issues. Tenable.sc CV provides the tools that state and local government agencies can use to meet and demonstrate FTI compliance.
IRS Publication 1075 is largely based on the standard NIST Special Publication 800-53, but with special considerations for additional sensitive information. Tenable Network Security has extensive expertise in helping customers meet the requirements of NIST Special Publication 800-53, and as a result, the Tenable.sc CV solution is well suited for meeting IRS Publication 1075 requirements as well.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessments.
The dashboard requirements are:
- Tenable.sc 4.8.1
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.0
Download the Analysis and Compliance to Meet CJIS and FTI Security Standards whitepaper.
Listed below are the included components:
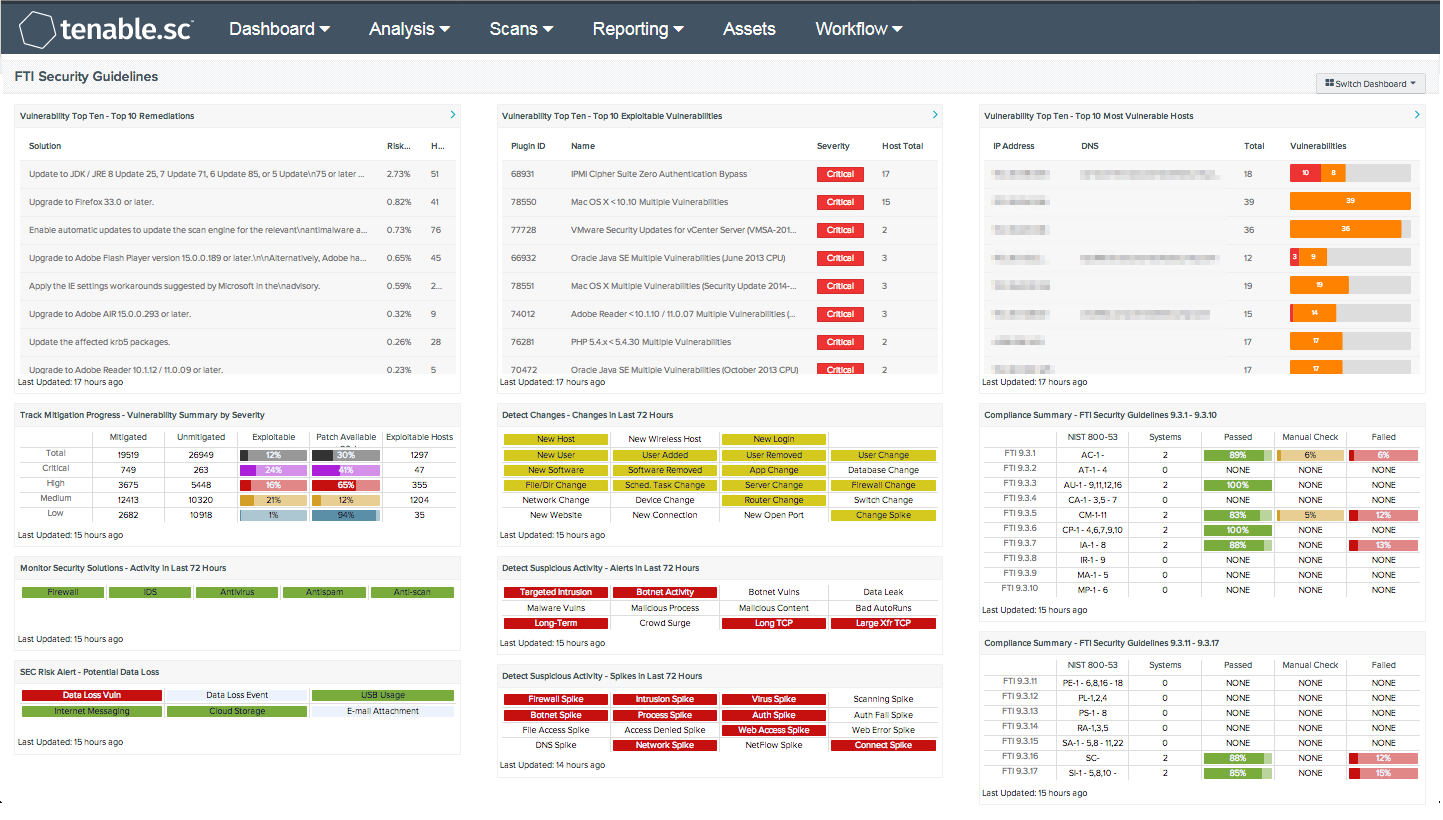
- Vulnerability Top Ten - Top 10 Remediations - This table displays the top 10 remediations for the network. For each remediation, the risk reduction for the network if the remediation is implemented is shown, along with the number of hosts affected. The list is sorted so that the highest risk reduction is at the top of the list. Implementing the remediations will decrease the vulnerability of the network.
- Vulnerability Top Ten - Top 10 Exploitable Vulnerabilities - This table displays the top 10 exploitable vulnerabilities on the network. The list is sorted so that the most critical vulnerability is at the top of the list. For each vulnerability, the severity and the number of hosts affected is shown.
- Vulnerability Top Ten - Top 10 Most Vulnerable Hosts - This table displays the 10 hosts on the network that have the greatest number of exploitable critical and high severity vulnerabilities. The list is sorted so that the most vulnerable host is at the top of the list. For each host, a bar graph of its critical and high severity vulnerabilities are shown.
- Track Mitigation Progress - Vulnerability Summary by Severity - Tenable.sc records when vulnerabilities are discovered, when patches are issued, and when vulnerabilities are mitigated. This component assists in tracking vulnerability mitigations. The matrix presents vulnerability summary information by severity. In the matrix, the row with purple is critical severity vulnerability information, the row with red is high severity, the row with orange is medium severity, and the row with blue is low severity. The Mitigated column displays the total number of mitigated vulnerabilities. The Unmitigated column displays the total number of vulnerabilities that have not yet been mitigated. The Exploitable column displays the percentage of those unmitigated vulnerabilities that are known to be exploitable. The Patch Available column displays the percentage of the unmitigated, exploitable vulnerabilities that have had a patch available for more than 30 days. Ideally, both of these percentages should be 0%, because all exploitable vulnerabilities and all vulnerabilities with patches available should have been mitigated already. The Exploitable Hosts column displays the number of hosts on the network that have unmitigated, exploitable vulnerabilities.
- Monitor Security Solutions - Activity in Last 72 Hours - This component assists in monitoring security solutions. The matrix presents activity indicators for various security solutions: Firewall, IDS, Antivirus, Antispam, and Anti-scanning. This component assumes that if log events were received in the last 72 hours from a particular technology, then that technology is active on the network, so the indicator is highlighted green. Further investigation is warranted if a protection technology should be active, but no events are being received.
- SEC Risk Alert - Potential Data Loss - This matrix displays various indications of potential for data leakage and loss. Red indicators signify that activity of high severity has occurred. Green indicators signify that activity that has the potential for data loss has occurred and further investigation may be warranted.
- Detect Changes - Changes in Last 72 Hours - This component can assist in maintaining up-to-date inventories and detecting changes. The matrix presents indicators for network changes detected in the last 72 hours. Each indicator is based on one or more Log Correlation Engine (LCE) events; the indicator is highlighted yellow if the event occurred in the last 72 hours. Any changes should be investigated to determine if they are authorized. More information can be obtained on these events (such as change details, time, and IP address) by clicking on the specific indicator and viewing the raw syslog.
- Detect Suspicious Activity - Alerts in Last 72 Hours - This matrix presents warning indicators for potentially suspicious network activity detected in the last 72 hours. Each indicator is based either on one or more Log Correlation Engine (LCE) events, or on active or passive vulnerability detections. The indicator is highlighted red if the event occurred in the last 72 hours. Any warnings should be further investigated. More information can be obtained on these events (such as details, time, and IP address) by clicking on the specific indicator and viewing the raw syslog (for events) or the detailed vulnerability list (for vulnerabilities).
- Targeted Intrusion – An intrusion attack was detected that targeted systems and ports likely to be exploited by the detected attack
- Botnet Activity – Traffic to or from a known malicious IP address was detected
- Botnet Vulns – Botnet activity was actively detected
- Data Leak – Potential data leakage was detected
- Malware Vulns – Malware was actively or passively detected
- Malicious Process – A malicious process was actively detected
- Malicious Content – Malicious hosted web content was actively detected
- Bad AutoRuns - Windows AutoRun and scheduled task registry entries known to be associated with malware were actively detected
- Long-Term – Potentially suspicious activity occurring over a long period of time was detected
- Crowd Surge – A large number of local hosts visiting the same server was detected
- Long TCP – A TCP session lasting more than a day was detected
- Large Xfr TCP – A TCP session which transferred more than 1GB was detected
- Detect Suspicious Activity - Spikes in Last 72 Hours - This matrix presents warning indicators for potentially suspicious spikes in network activity detected in the last 72 hours. Each indicator is based on one or more Log Correlation Engine (LCE) events. The indicator is highlighted red if the event occurred in the last 72 hours. Any warnings should be further investigated. More information can be obtained on these events (such as details, time, and IP address) by clicking on the specific indicator and viewing the raw syslog.
- Firewall Spike – A large number of firewall events, compared to previous event rates, were detected
- Intrusion Spike – A large number of intrusion events, compared to previous event rates, were detected
- Virus Spike – A large number of virus events, compared to previous event rates, were detected
- Scanning Spike – A large number of scanning events (port scans, port sweeps, and probes), compared to previous event rates, were detected
- Botnet Spike – A large number of threatlist events (traffic to or from known malicious IP addresses), compared to previous event rates, were detected
- Process Spike – A large number of process events (such as process starts, stops, and crashes), compared to previous event rates, were detected
- Auth Spike - A large number of login events, compared to previous event rates, were detected
- Auth Fail Spike - A large number of login failure events, compared to previous event rates, were detected
- File Access Spike – A large number of remote file access events (such as FTP and SMB transfers, and e-mail attachments), compared to previous event rates, were detected
- Access Denied Spike – A large number of access denied events (attempts to retrieve objects, files, network shares and other resources that are denied), compared to previous event rates, were detected
- Web Access Spike – A large number of web access events (successful connections to web resources), compared to previous event rates, were detected
- Web Error Spike – A large number of web error events (web access events that are denied because the file does not exist, the server responded with an error, or a firewall or web application firewall blocked the access), compared to previous event rates, were detected
- DNS Spike – A large number of DNS events, compared to previous event rates, were detected
- Network Spike – A large number of network events, compared to previous event rates, were detected
- NetFlow Spike – A large number of NetFlow events (detected by the Tenable NetFlow Monitor (TFM)), compared to previous event rates, were detected
- Connect Spike – A large number of connection events (such as allowed connections through firewalls and established VPN sessions), compared to previous event rates, were detected
- Compliance Summary - FTI Security Guidelines (2 components) - These matrices provide a sense of how the network complies with the security guidelines in IRS Publication 1075. Sections from the Computer System Security chapter of the Publication are listed. For each section, the equivalent NIST 800-53 controls are displayed, along with the number of network systems that were audited against these controls, and ratio bars for the percentage of these compliance checks that either passed (green bar), failed (red bar), or require manual verification (orange bar). Since the Publication specifically mentions the equivalent NIST 800-53 controls, the displayed information will give a good sense of how the network complies with the security guidelines in IRS Publication 1075.