by Cesar Navas
November 12, 2014
Analysts strive to ensure that security is done right to protect the organization. To protect the environment, there are basic security needs that can apply to any organization that should be fulfilled. When an organization does security right by performing basic security duties, meeting regulatory requirements becomes a natural benefit.
Basic cyber hygiene includes the need to cover basic scenarios, such as knowing what assets are in the environment and asserting what vulnerabilities may lurk within. Without knowing what vulnerabilities are present, analysts cannot ensure that the correct security controls are in place to mitigate or remove the vulnerability. Attackers may use such an opportunity to exploit the vulnerability to steal confidential information. When organizations lack this knowledge or are not aware of other threats such as lack of hardening systems to a common standard, large gaps of security can reside in critical points of infrastructure.
The Center for Internet Security (CIS), Council on CyberSecurity (CCS), and the National Governors Association Governors Homeland Security Advisors Council have sponsored a security awareness initiative called the Cyber Hygiene Campaign. This campaign is a multi-year effort to provide a low-cost program to achieve immediate and effective defenses against cyber attacks. Tenable.sc Continuous View (CV) supports the campaign in several ways by detecting vulnerabilities actively, passively, and through host analysis.
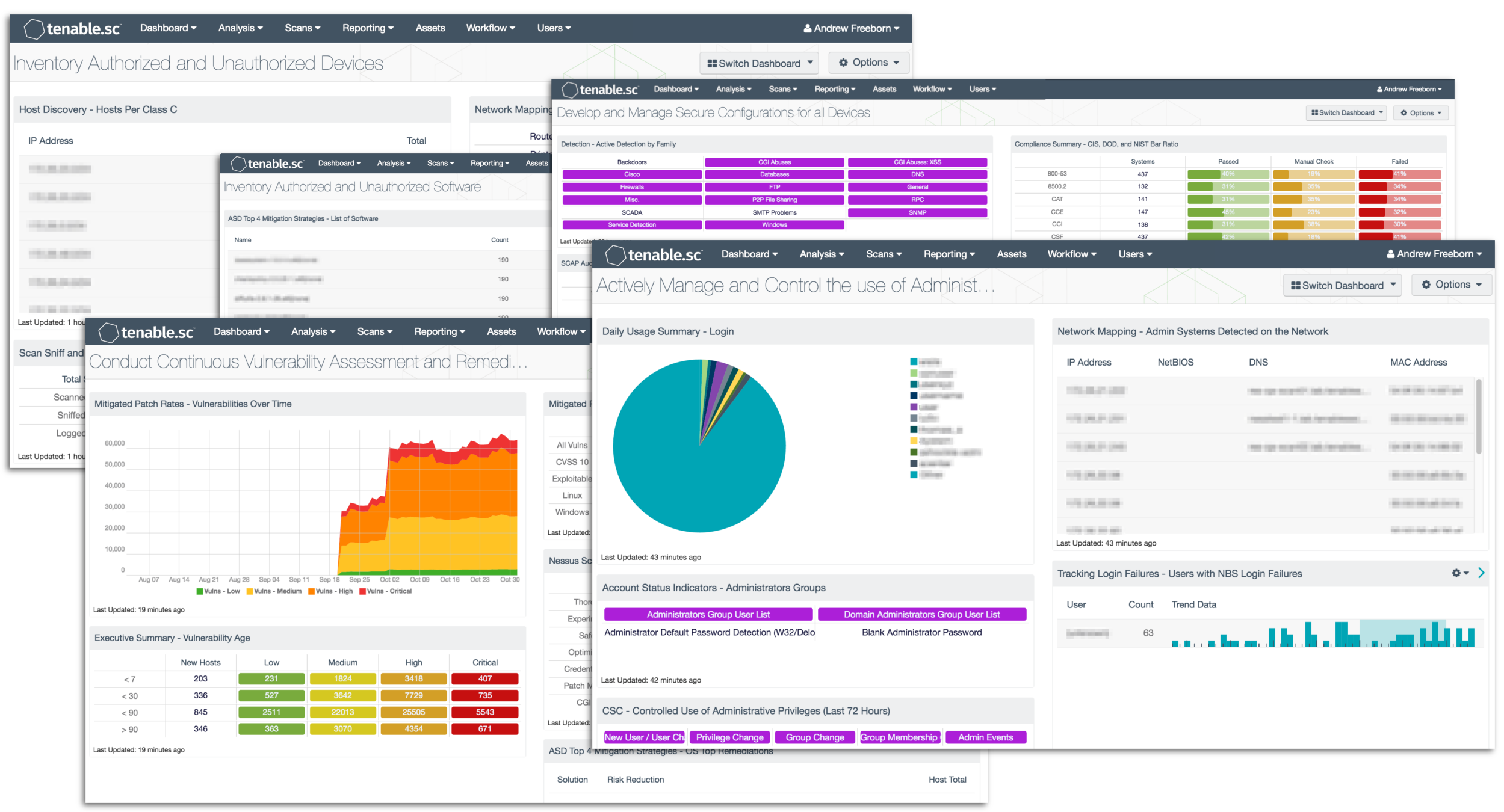
In support of the Cyber Hygiene Campaign, Tenable brought together a group of dashboards described in the “Tenable Solutions for the Cyber Hygiene Campaign” technical paper. These dashboards relate to the five actions identified by the Cyber Hygiene Campaign along with helping an organization fulfill basic security needs such as monitoring. The dashboards below also align in order with the top 5 CIS Critical Security Controls. Tenable.sc CV’s proactive continuous network monitoring identifies the biggest risks across the entire organization. Analysts can quickly ascertain the state of the cyber hygiene of the organization with Tenable.sc CV. Tenable’s unique sensors and analytics enable the organization to assess how well the security program is performing with the following dashboards below.
- Inventory Authorized and Unauthorized Devices: Identifying systems on the network can be a monumental task, as many organizations have different groups responsible for system inventories. This collection of components provides information to analysts and auditors about systems discovered on the network and device inventory. According to the Council on Cybersecurity, the first of the 20 security controls is to maintain an inventory of authorized and unauthorized devices.
- Inventory Authorized and Unauthorized Software: A good vulnerability management program requires that an organization also know the software installed on its systems. This dashboard and its components provide information to analysts about software that is discovered on the network. According to the Council on Cybersecurity, the second of the 20 security controls is to maintain an inventory of authorized and unauthorized software.
- Develop and Manage Secure Configurations for all Devices: Hardening and configuration guidelines can be difficult to create and to maintain. There are several industry standards available to organizations such as NIST 800-53, CIS, and CSC. Tenable.sc Continuous View has the ability to audit system configurations according to the standards. The components in this dashboard use forensic plugins, detections, and compliance checks to provide information about how systems are configured. According to the Council on CyberSecurity, the third of the 20 security controls is to maintain secure configurations for hardware and software on mobile devices, laptops, workstations, and servers.
- Conduct Continuous Vulnerability Assessment and Remediation: Detecting vulnerabilities requires a diligent information security team and the ability to detect vulnerabilities in several ways. Tenable.sc Continuous View has the ability to monitor for vulnerabilities using active, passive, and event-based detection. According to the Council on CyberSecurity, the fourth of the 20 security controls is to maintain continuous vulnerability assessment and remediation program.
- Actively Manage and Control the Use of Administrative Privileges: A common problem found in networks is that too many accounts with administrative privileges exist. Organizations should make an effort to use dual accounts when administrative rights are to be used. This dashboard provides information about which users have administrative control and how this control is used. According to the Council on CyberSecurity, the 12th of the 20 security controls is to control use of administrative privileges.
These dashboards and their components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. These dashboards can be easily located in the Tenable.sc Feed by searching for the terms “Cyber Hygiene”. The dashboard requirements are:
- Tenable.sc 5.4
- Nessus 8.5.1
- NNM 5.9.0
- LCE 6.0.0
Tenable.sc Continuous View (CV) provides continuous network monitoring, vulnerability identification, and security monitoring. Tenable.sc is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audit files. Tenable constantly analyzes information from our unique sensors, delivering continuous visibility and critical context, enabling decisive action that transforms your security program from reactive to proactive. Active scanning examines the web services on the systems, running processes and services, detection of vulnerable software applications, configuration settings, and additional vulnerabilities. With this information, analysts have greater insight to determine if supported and update to date systems and software are operating within the organization. Continually monitoring the network with passive sensors for servers, desktops and applications helps prioritize security efforts to mitigate threats and weaknesses. Organizations continue to operate with more mobile and transient network devices and need to have a system in place that continuously monitors traffic, devices, applications, and communications across environments. Tenable enables powerful, yet non-disruptive, continuous monitoring of the organization to ensure vulnerability data is available to analysts.