by Cesar Navas
October 19, 2016
Preventative measures alone will never be completely successful in stopping network attacks, intrusions, and compromise. No matter how small the hole in the network defenses, that hole will eventually be found and exploited. This exploitation could result in persistent attacker presence on the network, compromise of critical systems, and theft of sensitive data. A continuous network monitoring capability is therefore needed to detect suspicious activity that may indicate network defenses have been breached.
The French Network and Information Security Agency (Agence nationale de sécurité des systèmes d’information or ANSSI) developed the "40 Essential Measures for a Healthy Network" to assist organizations in safeguarding the security of information systems within a network. Following these measures, or rules, for a healthy network will provide basic protection for an organization's critical data. ANSSI states that the majority of IT attacks that have involved ANSSI stepping in could have been prevented had the IT measures set out in the guide been applied.
This dashboard aligns with Section VIII of the ANSSI 40 Essential Measures for a Healthy Network guide: Monitor Systems. This section contains two rules:
- Rule 26 advises clearly defining what to monitor, and specifies some basic network events that should generate an alert. In particular, events that should be monitored include large outgoing data transfers, repeated attempts to connect to services or inactive accounts, user connections outside of normal business hours, and attempts to circumvent existing security policies.
- Rule 27 emphasizes that log data must be frequently analyzed. In particular, this rule emphasizes monitoring for suspicious access activity and ensuring that system times be synchronized so that log events can be correlated.
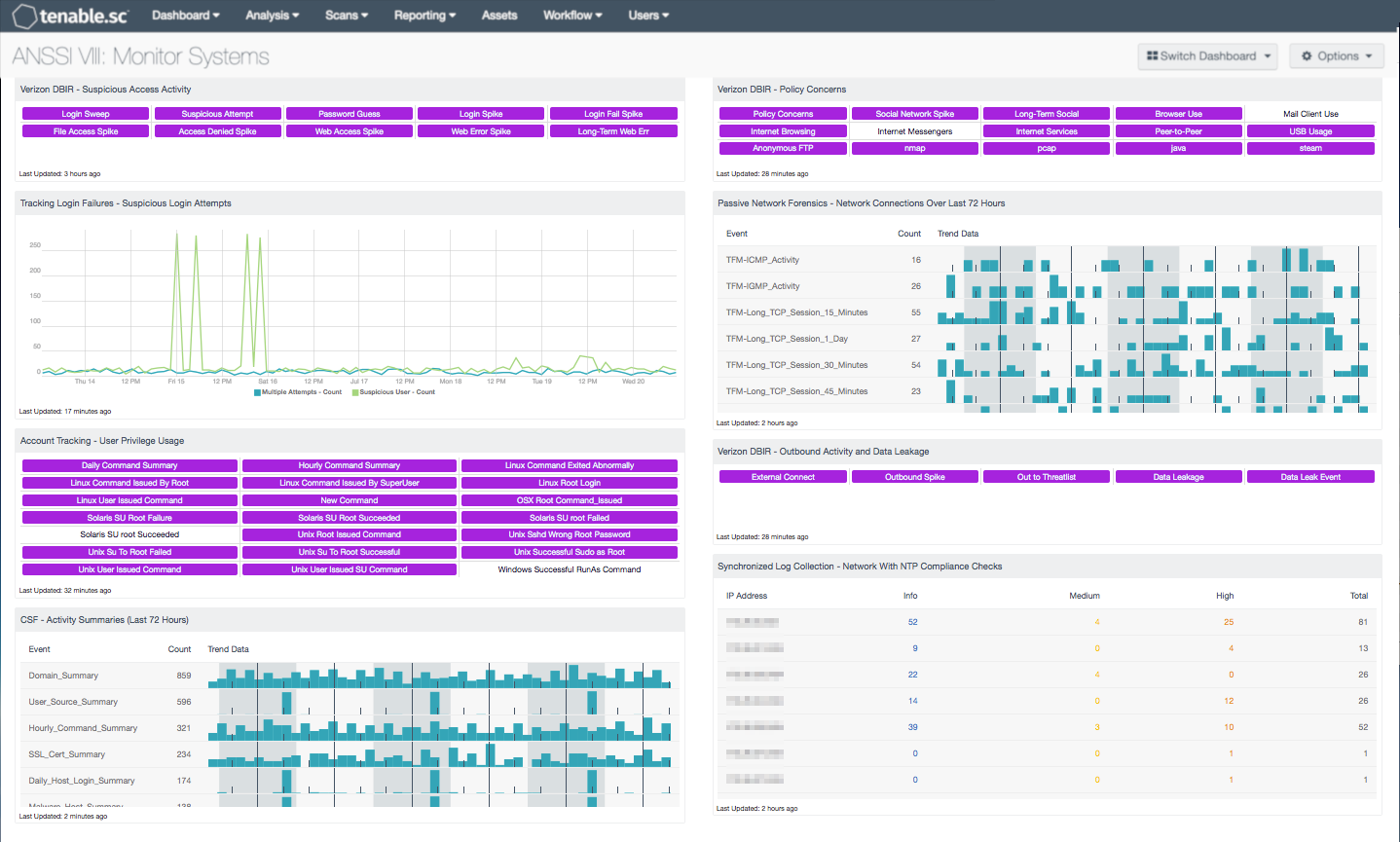
This dashboard assists an organization in continuously monitoring the network and discovering suspicious activity. The Tenable Log Correlation Engine (LCE) collects and correlates events from throughout the network, summarizing activity, detecting suspicious events and abuse, discovering anomalies, and monitoring sessions. Relying primarily on information from the LCE, this dashboard helps an organization determine if systems on the network have been compromised. The organization can then take action as needed to address the network compromise before additional systems are affected.
Components on this dashboard report on suspicious logins, spikes in access activity, elevated privilege usage events, and activity indicating policy concerns. This activity may indicate changes in user behavior or malicious activity on the network that needs to be addressed. Indicators highlighting external connections, outbound connections to known bad IP addresses, and data leakage are shown as well. Summary data such as command summaries and crash summaries is presented, giving insight into recent host activity on the network. Session and NetFlow data is shown, allowing further investigation of long sessions or large data transfers. In addition, Network Time Protocol (NTP) compliance status is presented per subnet, in order to highlight potential concerns with system time synchronization. The information on this dashboard will help the organization monitor the network and recognize any suspicious activity that may need further investigation.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.3.2
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.1
- Tenable Network Monitor
- Tenable NetFlow Monitor
- Compliance data
The dashboard contains the following components:
- Verizon DBIR - Suspicious Access Activity - This matrix assists the organization in monitoring for suspicious access activity such as suspicious login activity and spikes in file and web accesses.
- Tracking Login Failures - Suspicious Login Attempts - This component displays trend lines related to suspicious login attempt activity in the past seven days.
- Account Tracking - User Privilege Usage - This component uses LCE to track events related to limited access and the use of elevated privileges.
- CSF - Activity Summaries (Last 72 Hours) - This table displays all summary events generated by the LCE in the last 72 hours.
- Verizon DBIR - Policy Concerns - The Verizon DBIR notes that certain activities should be restricted on certain hosts. This matrix assists the organization in monitoring potential policy violations on its network, including general policy concerns, social network activity, browser and mail client use, P2P activity, USB usage, and more.
- Passive Network Forensics - Network Connections Over Last 72 Hours - This table presents network connection events from the Tenable Network Monitor (TNM), Tenable NetFlow Monitor (TFM), and passively from the Tenable's Nessus Network Monitor (NNM) that have occurred over the last 72 hours, with trending.
- Verizon DBIR - Outbound Activity and Data Leakage - The Verizon DBIR advocates monitoring outbound connections to prevent data exfiltration. This matrix assists the organization in monitoring its outbound activity, including data leakage.
- Synchronized Log Collection - Network With NTP Compliance Checks - This component reports on audit checks that verify the NTP settings on subnets.
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to find vulnerabilities, and can also make use of audit files to assess compliance. Passive listening provides real-time monitoring to collect information about systems and vulnerabilities. Host data and data from other security devices is monitored and correlated in order to detect abuse, anomalies, and network compromise. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to monitor the network, and recognize and further investigate any suspicious activity.