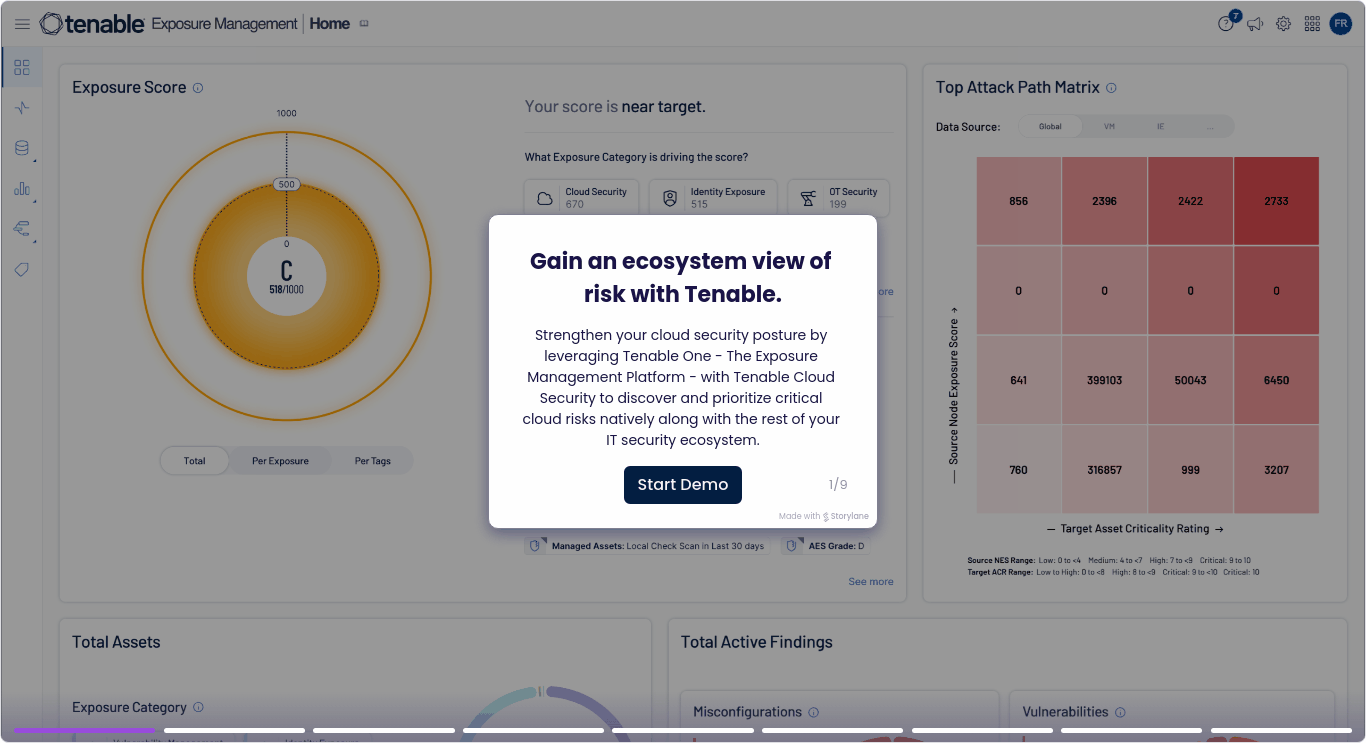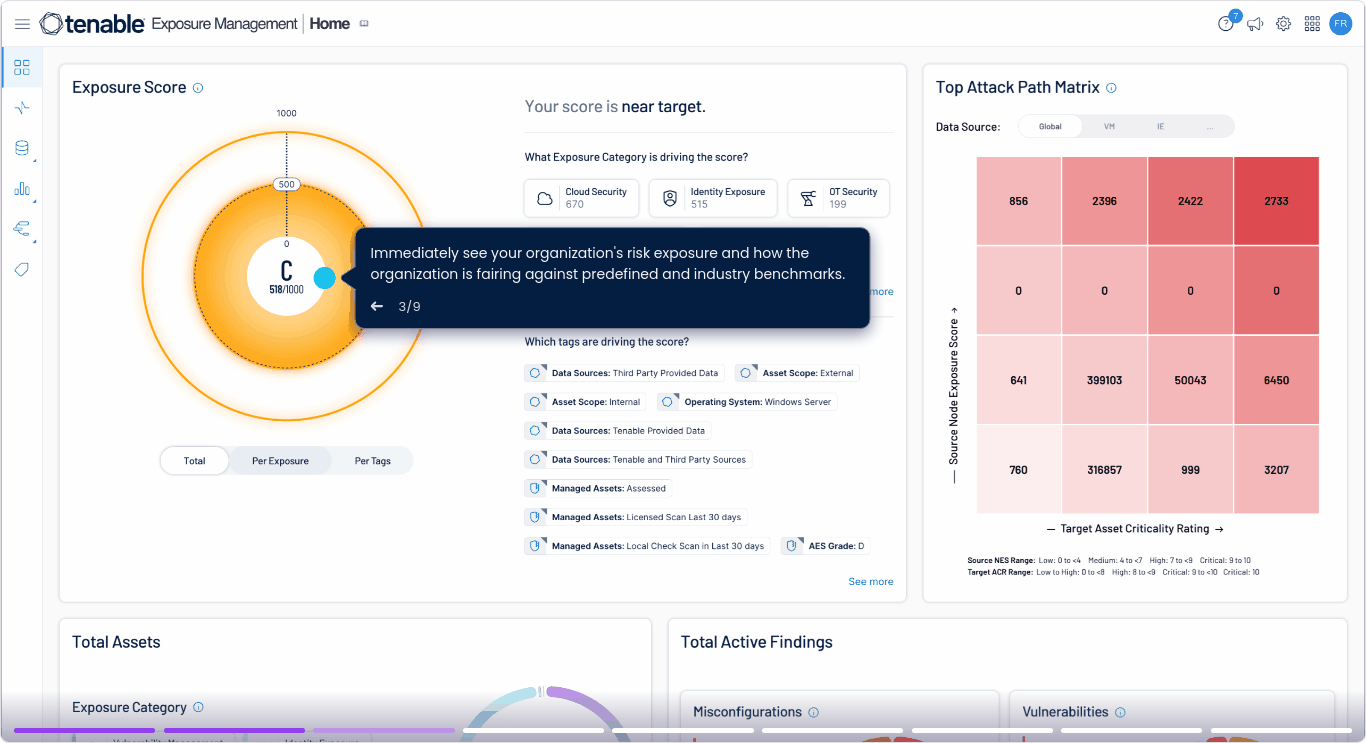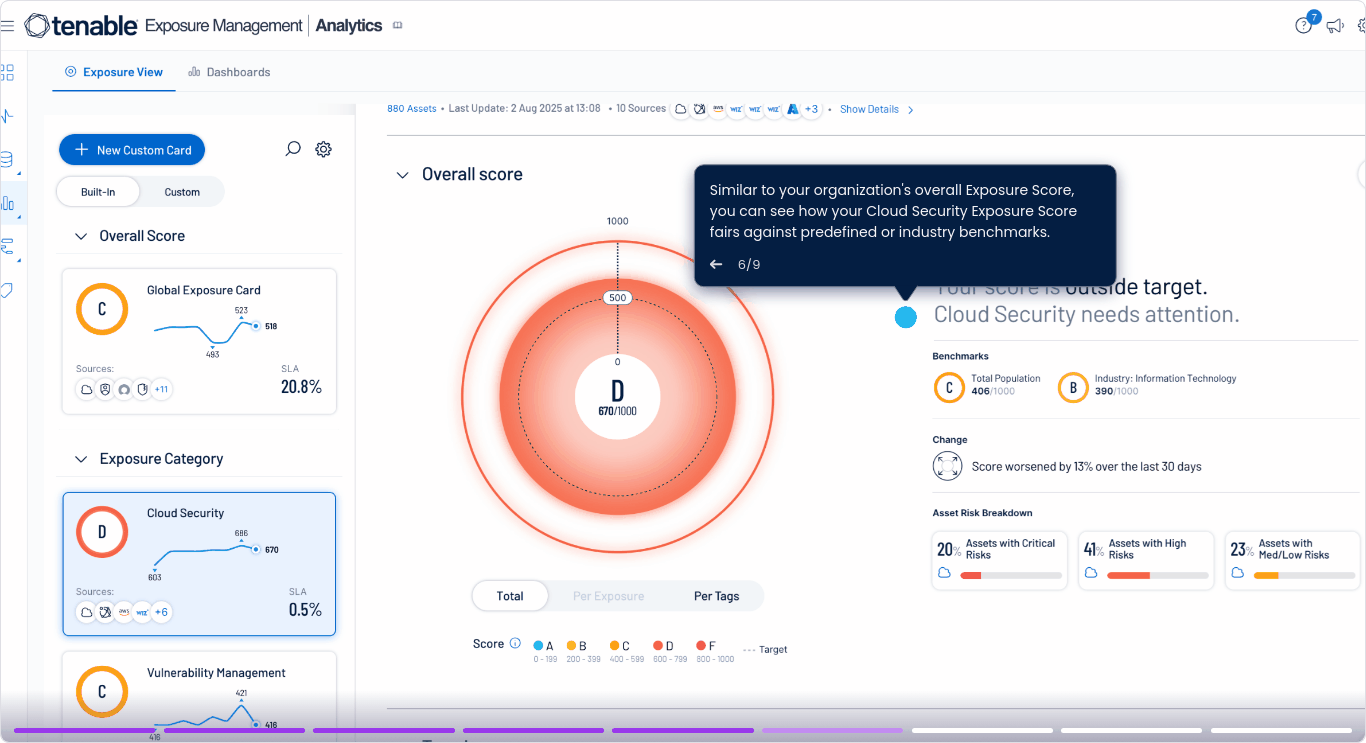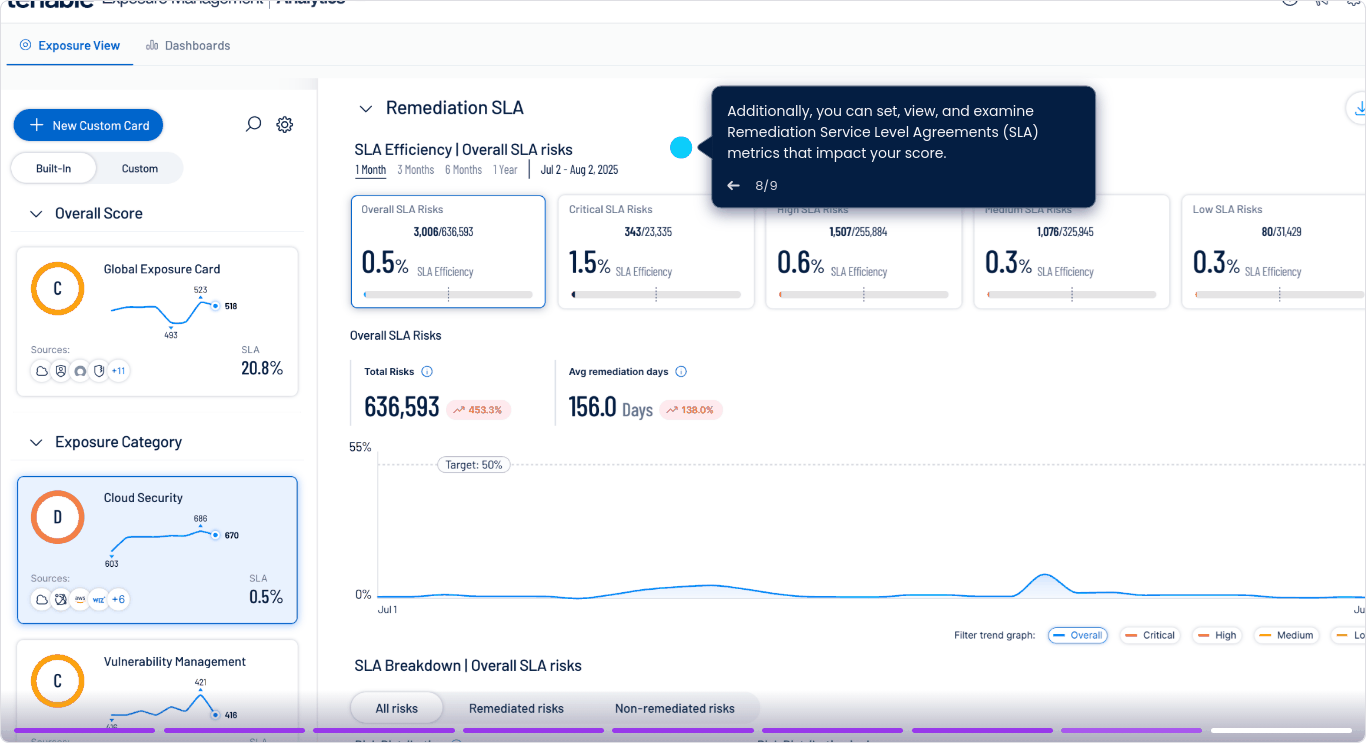
Ecosystem view of cloud security risk
Leverage exposure management to prioritize cloud security risks natively with the rest of your IT security ecosystem. Tenable Cloud Security, natively integrated with Tenable One, gives you unified visibility across cloud and traditional IT environments to correlate risks across your entire infrastructure.
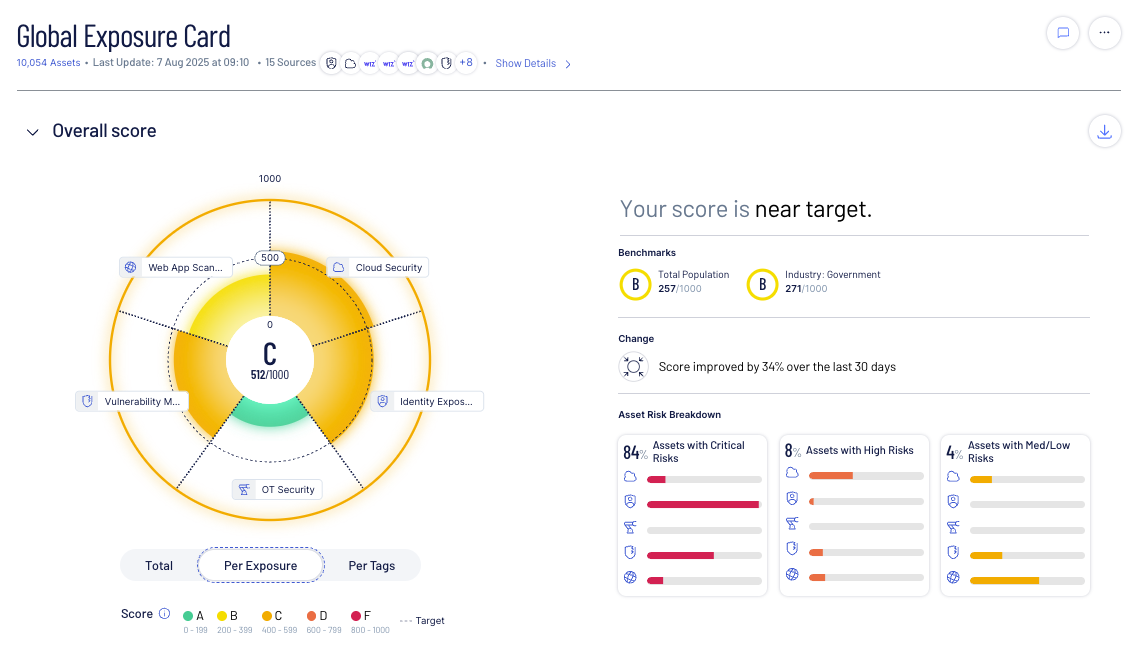
Gain a unified view of risk
Prioritize threats based on exploitability and business impact across your entire attack surface
Unified risk correlation
Shared prioritization
Development to runtime context
Identity-aware and least privilege enforcement
Board-level reporting and strategic alignment
Tenable Cloud Security doesn't treat cloud risk as an isolated domain
The cloud security platform integrates directly into your exposure management strategy so you can understand, prioritize and reduce cyber risk across your full attack surface.
取得整個環境統一的風險關聯分析
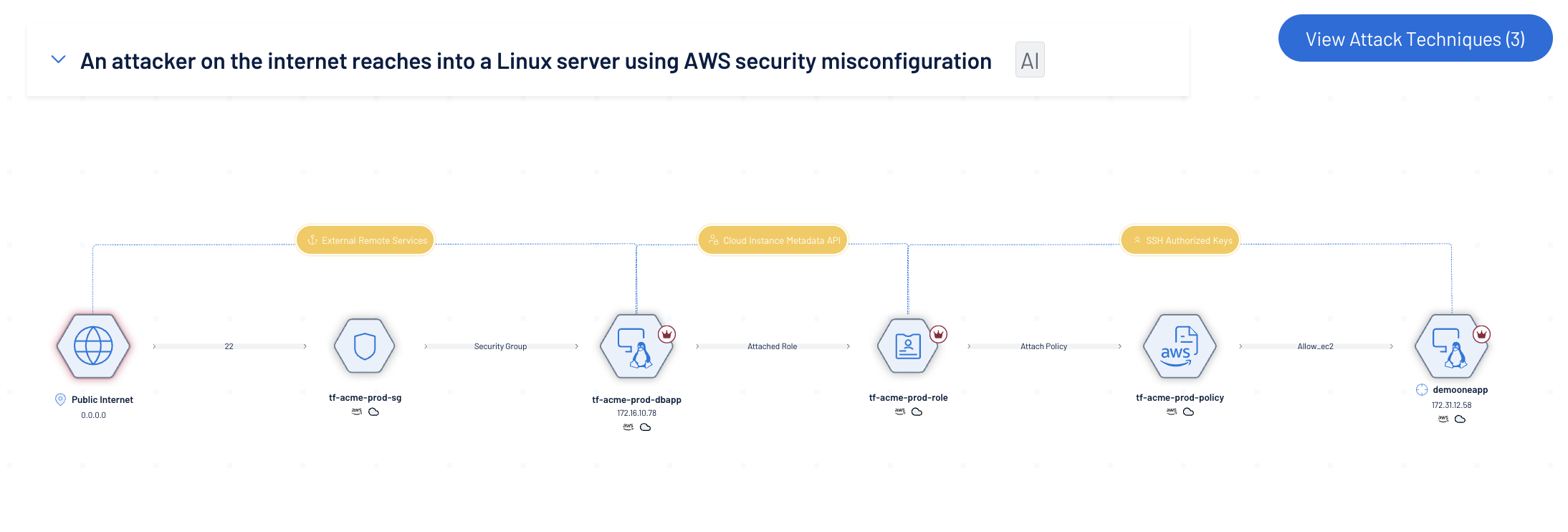
Correlate vulnerabilities, misconfigurations, and identity cloud security risks across cloud to reveal toxic combinations and real attack paths—delivering unified visibility across your hybrid environment.
Prioritize risk based on exploitability and impact
Use a normalized scoring model that blends exploitability, asset criticality, and access paths to prioritize the most critical risks across your ecosystem using a common exposure management model.
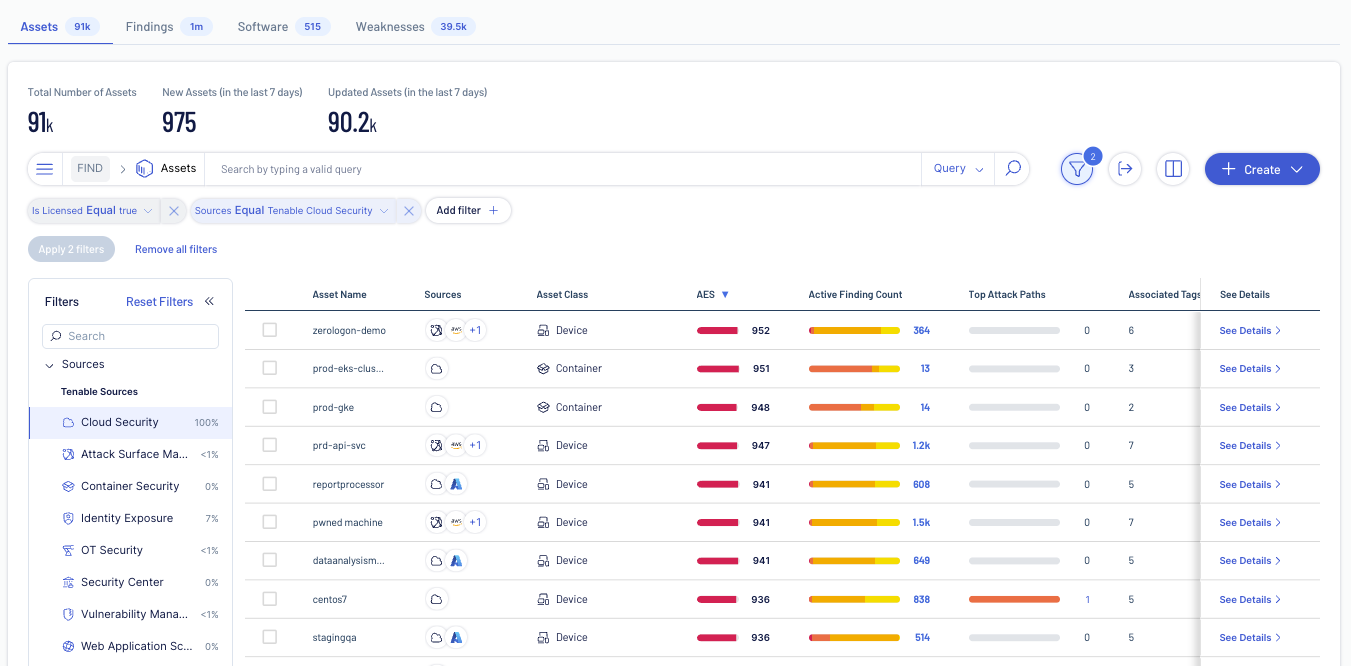
Streamline remediation from development through runtime
Trace risks from Infrastructure as Code to deployed workloads for full lifecycle visibility. Detect issues early and remediate faster with end-to-end context and connect insight across Infrastructure as Code scanning and CI/CD pipeline.
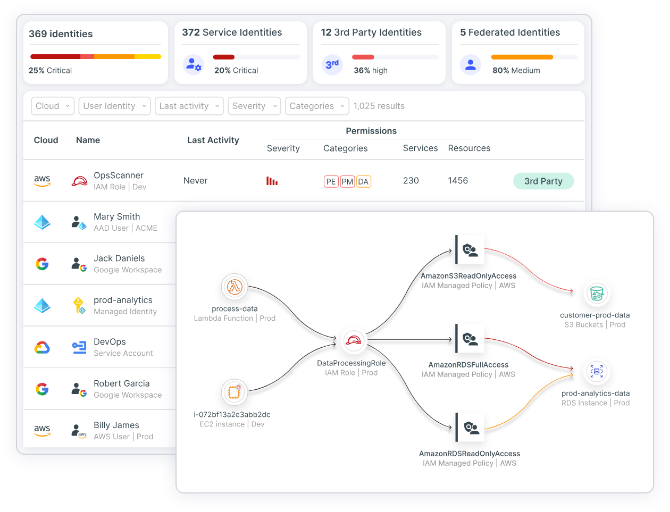
Enforce least privilege with identity-aware access controls
Visualize toxic combinations and enforce least privilege access using integrated Cloud Infrastructure Entitlement Management (CIEM). Eliminate excessive permissions and reduce insider and lateral movement risks.
深入瞭解 Tenable Cloud Security
使用 [Tenable Cloud Security] 的自動化功能,讓我們免除了讓人筋疲力竭的手動流程,並且在幾分鐘內執行過去可能需要 2 或 3 位安全人員好幾個月時間才能完成的工作。
- Tenable Cloud Security