Get complete cloud risk visibility and SDLC security
Misconfigurations and identity sprawl across your expanding cloud attack surface increase your risk and bury your security teams in alerts. Eliminate the alert noise and stop problems before they reach production. Shift left by scanning infrastructure as code (IaC) templates like Terraform, CloudFormation and ARM. Powered by Tenable One, you can connect code to runtime context to find and fix security issues before deployment, reduce rework and deliver secure cloud infrastructure faster.
Secure your entire development-to-production workflows
Get comprehensive cloud security across DevOps, SecOps and detection and response
Continuous SDLC-to-production traceability
Remediation acceleration through owner attribution
Drift-aware policy enforcement
Context-rich identity & entitlement mapping
Unified exposure graph across cloud and IT
Cloud security that spans your full lifecycle
Tenable Cloud Security connects build-time checks with runtime protection so you can catch misconfigurations early and minimize ongoing risk.
Get continuous SDLC-to-production traceability
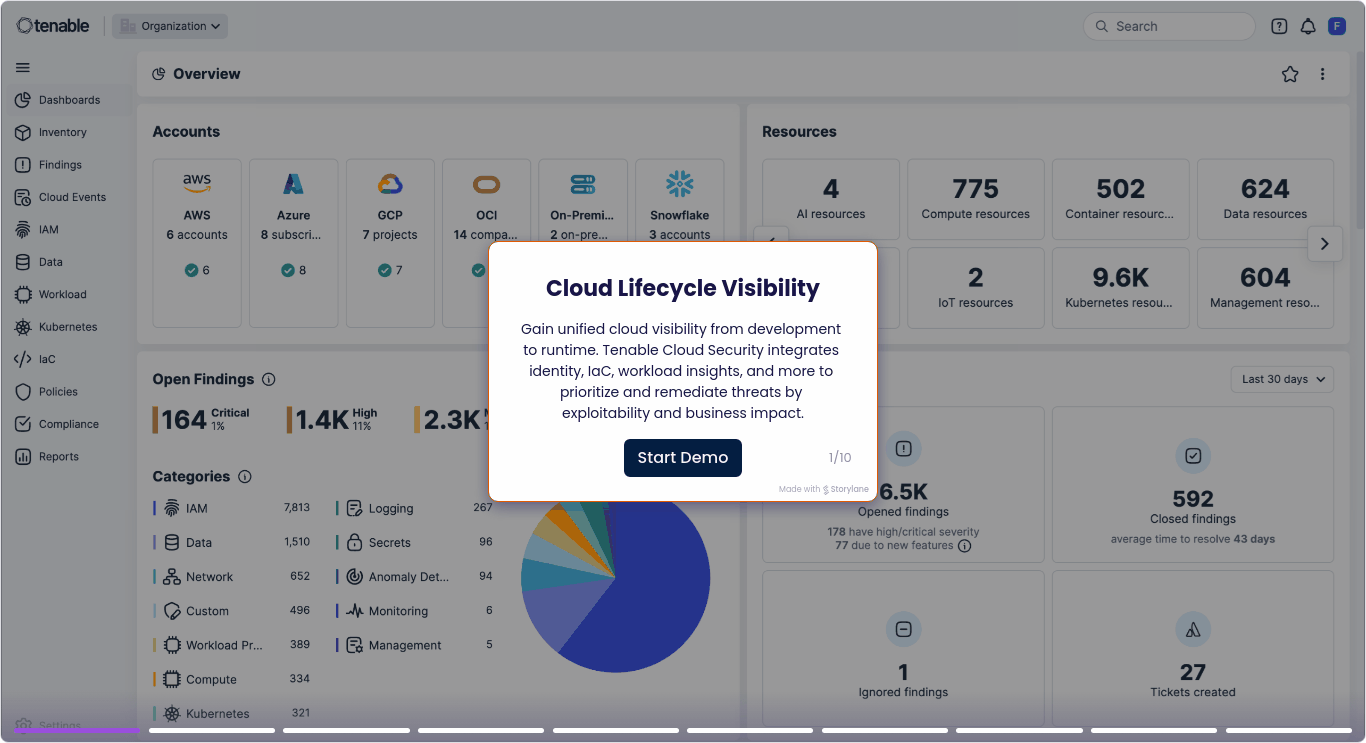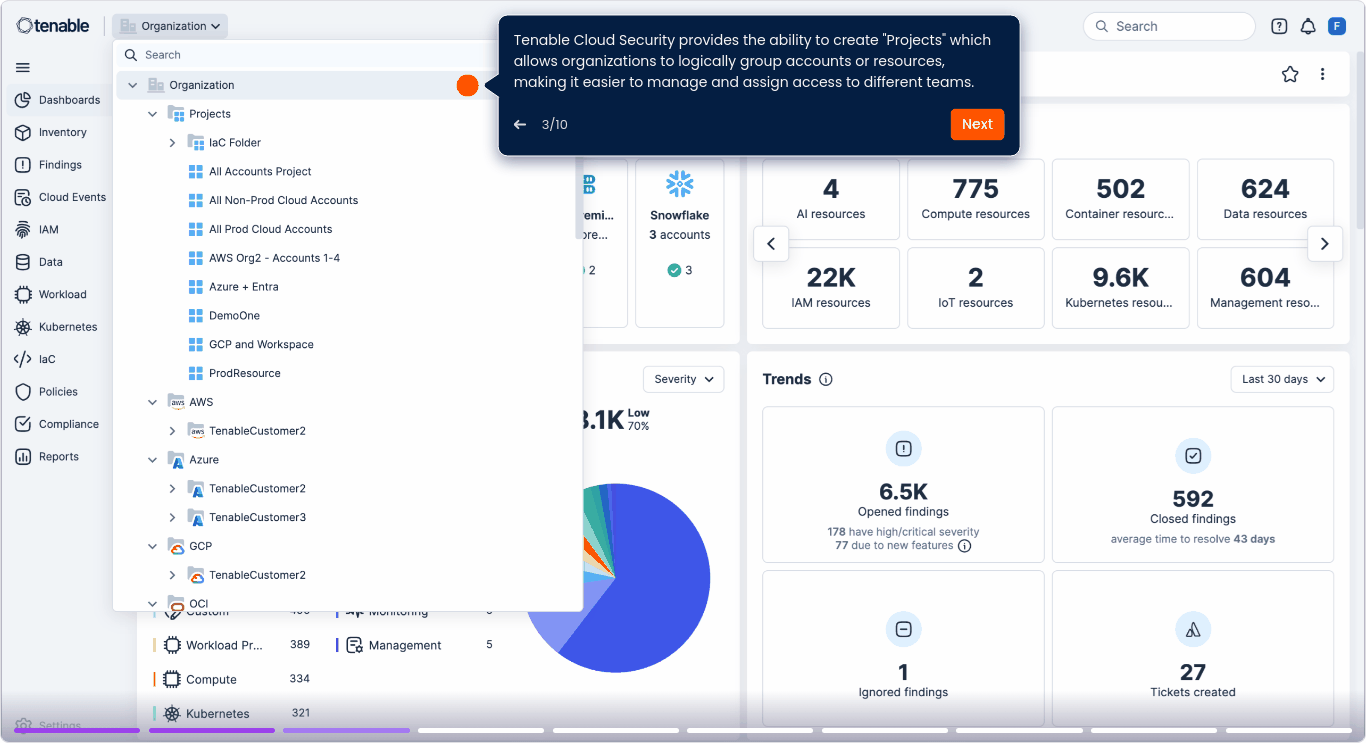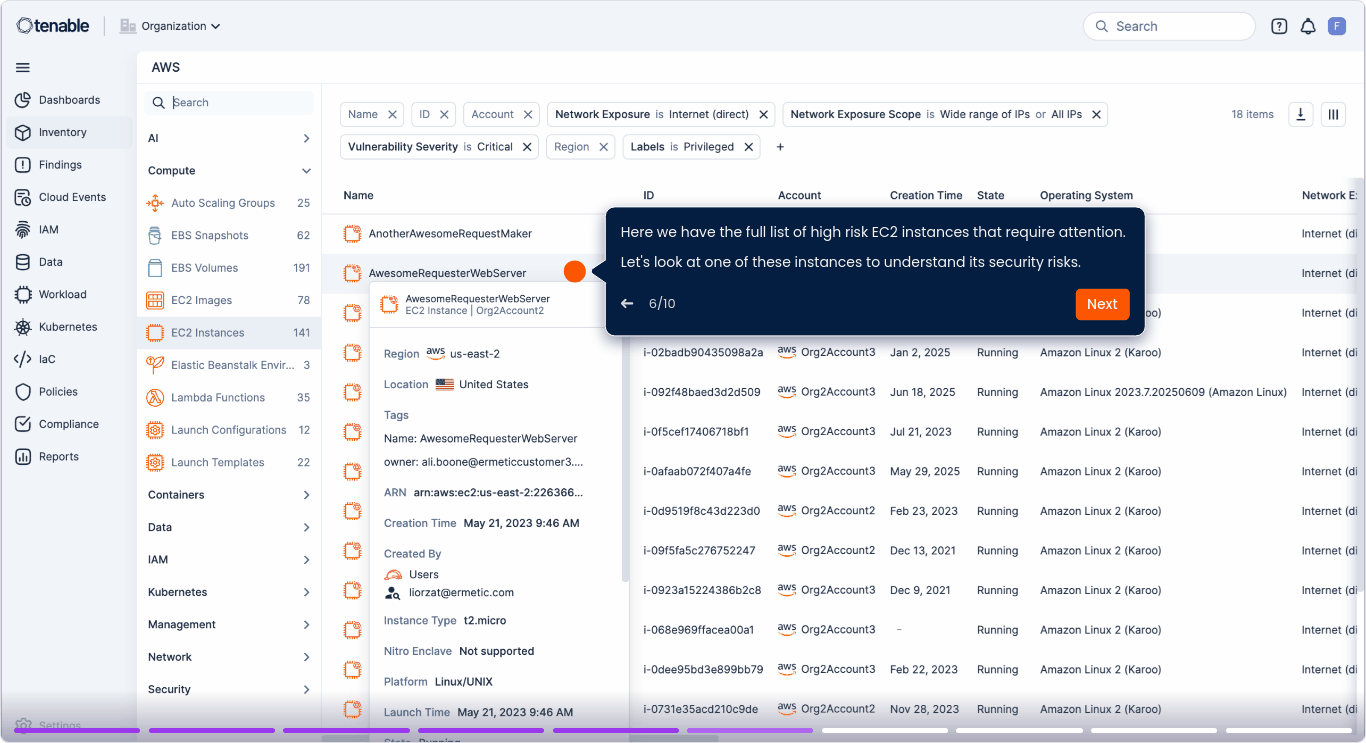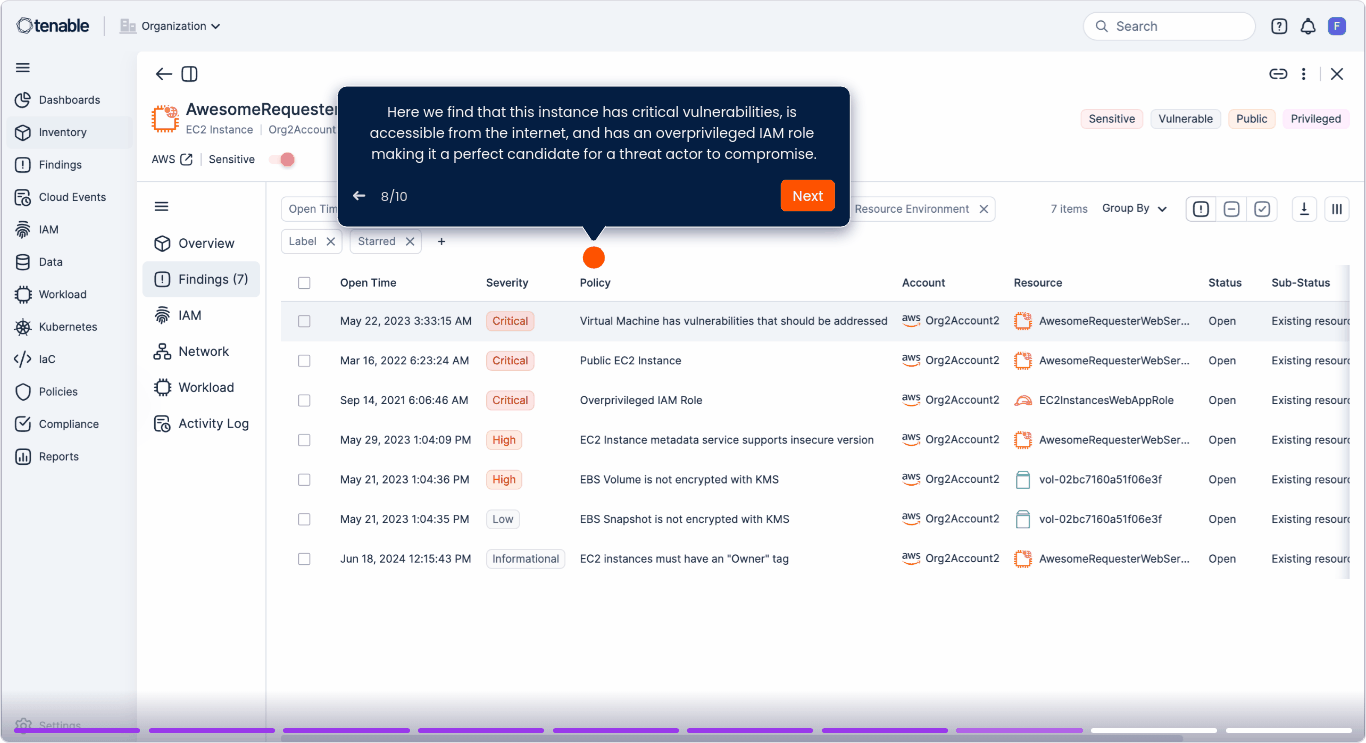
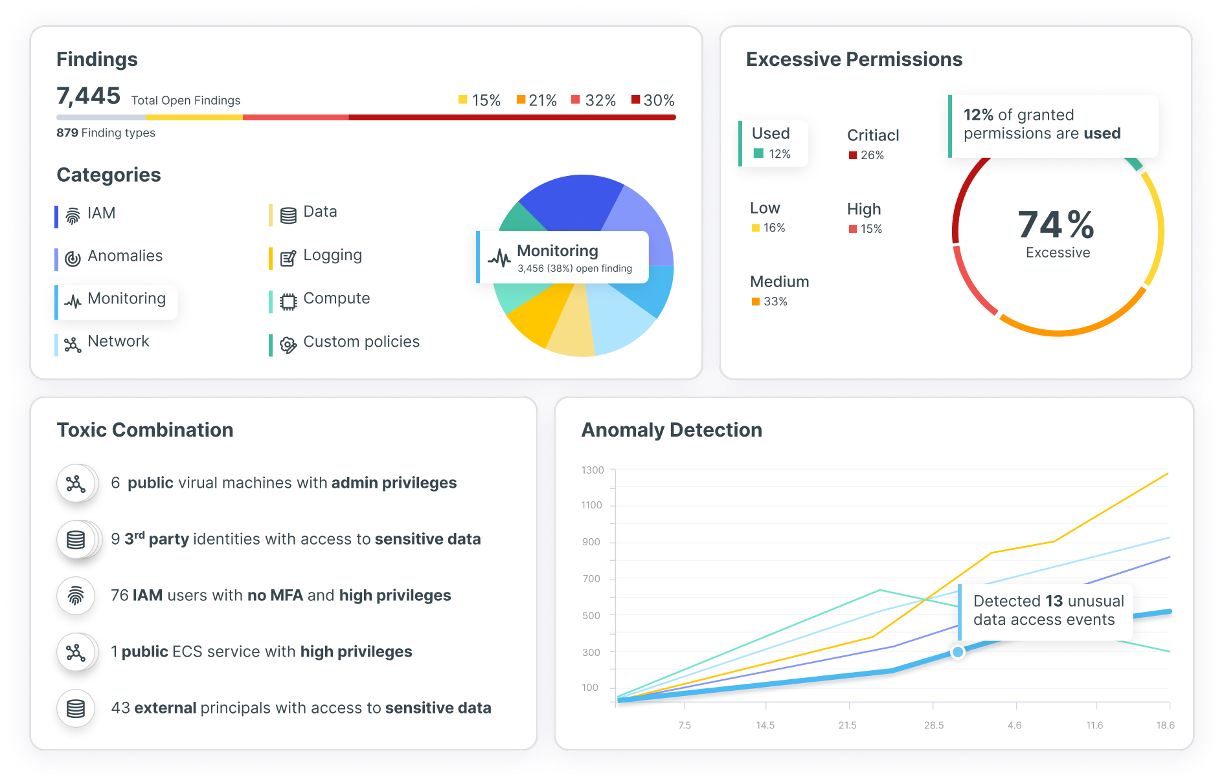
Correlate vulnerabilities, misconfigurations and identity risks to reveal toxic combinations and attack paths across code, build, deployment, configuration, and runtime.
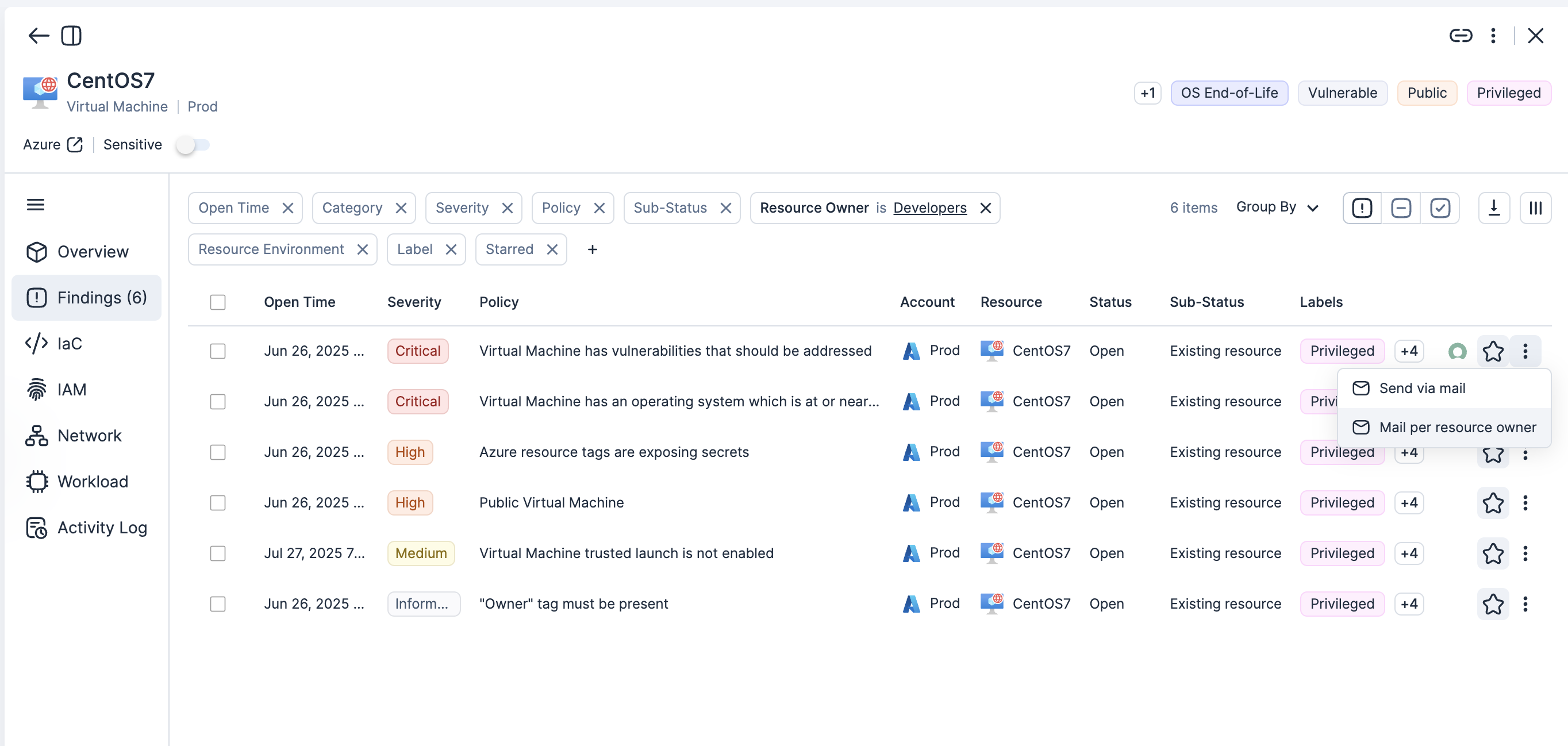
Accelerate remediation through owner attribution
Map every issue to its responsible team, service or repository with actionable fix guidance.
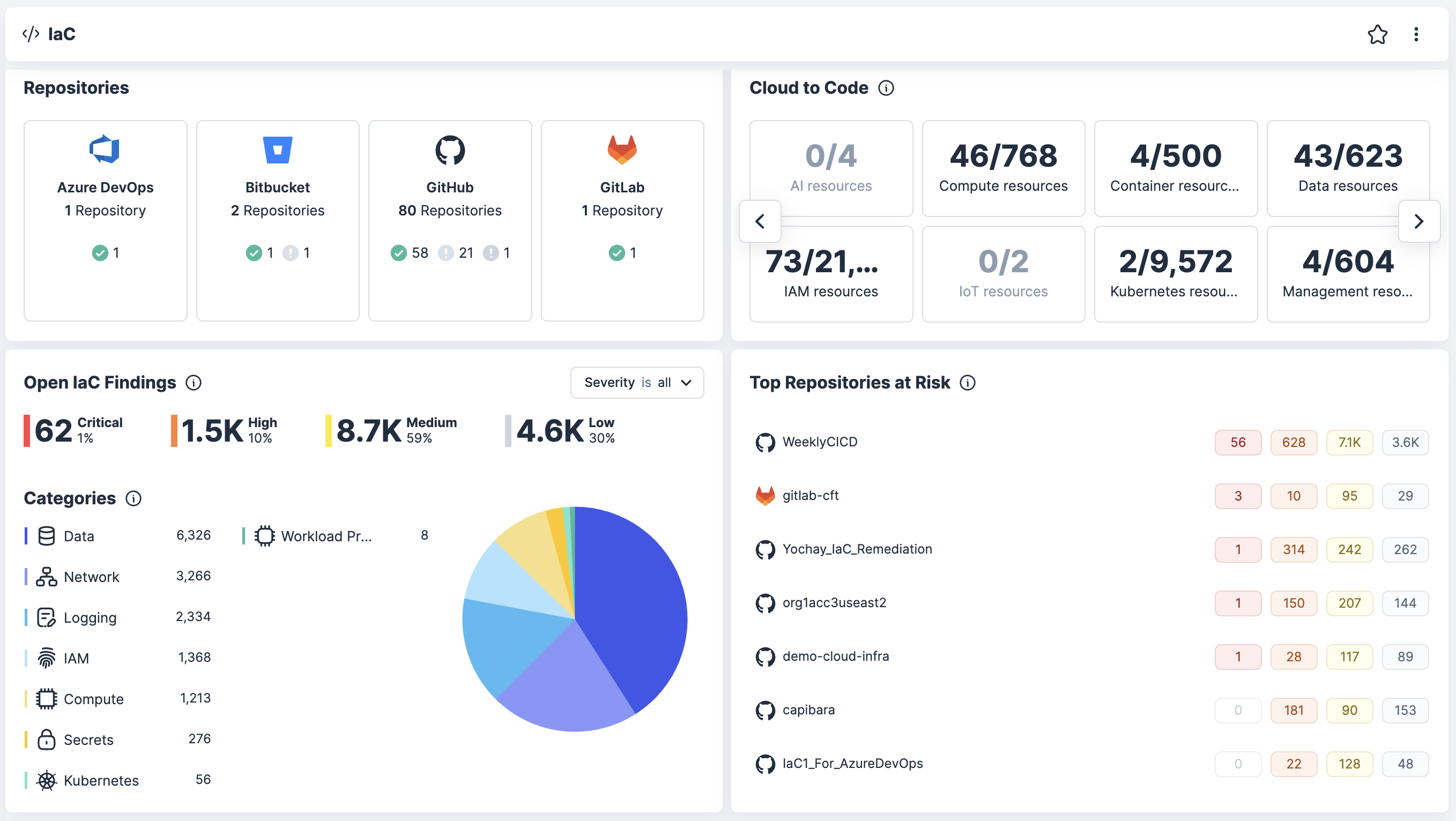
Apply drift-aware policy enforcement
Continuously enforce security guardrails from CI/CD to runtime to detect and prevent configuration drift, support SAST and maintain compliance.
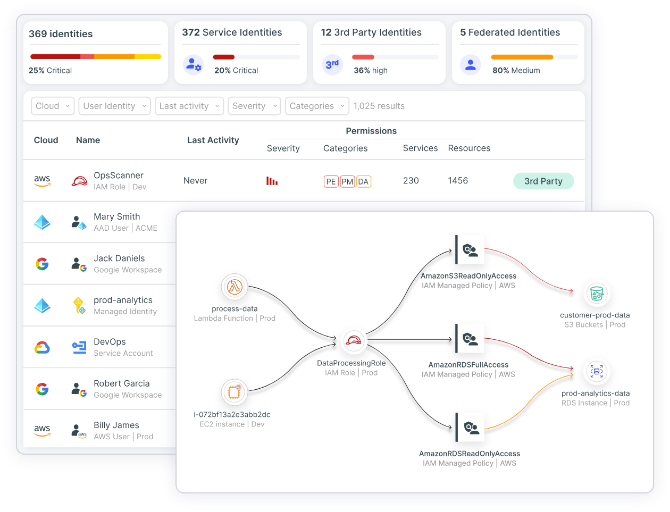
Use context-rich identity and entitlement mapping
Map access across users, roles, service principals and federated identities in real time.
Unify exposure graphs across cloud and IT
Correlate cloud-native and IT risks in a single exposure graph. Eliminate silos and prioritize threats based on exploitability and business impact.
深入瞭解 Tenable Cloud Security
使用 [Tenable Cloud Security] 的自動化功能,讓我們免除了讓人筋疲力竭的手動流程,並且在幾分鐘內執行過去可能需要 2 或 3 位安全人員好幾個月時間才能完成的工作。
- Tenable Cloud Security