WannaCry? Three Actions You Can Take Right Now to Prevent Ransomware

By now everyone has heard about the ransomware called Wanna, WannaCry or WCry spreading across the globe and locking down the data of some of the world’s largest companies. The malware appears to exploit an SMB flaw that Microsoft provided a patch for in March 2017. You may have heard that the worm has been successfully stopped and you have nothing to worry about, but the vulnerability still exists on millions of systems and can be used again. Now is not the time for complacency; it is time for action. Tenable has several ways to help you know where your business is exposed so you can make informed decisions about what to do first to detect WannaCry and protect your business.
Take action now
If you are a Tenable SecurityCenter® customer, here are three things you can do now before the next variant of WCry appears and before it encrypts the files on your machines.
1. Hunt for infected machines: Check for DNS queries and Scan for Malware.
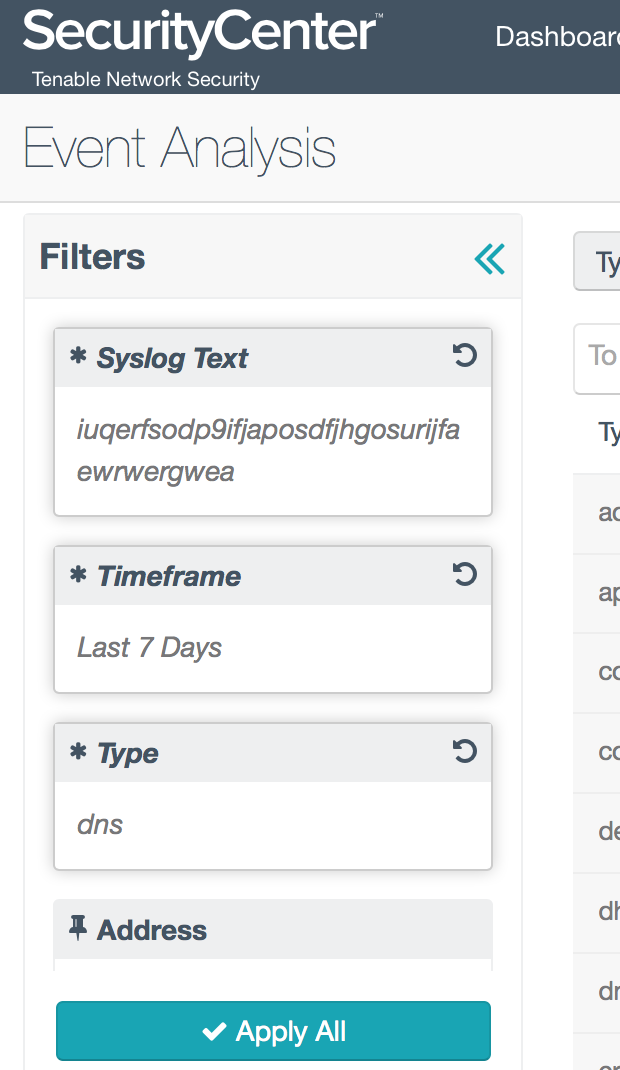
The first version of WCry that spread across the globe performs a DNS lookup when it initializes; luckily, the Passive Vulnerability Scanner® (PVS™) can record DNS queries on your network. You can apply the following filters in Event Analysis view to hunt for hosts that send queries to this domain:
Type: dns
Syslog Text: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea
Timeframe: Last 7 Days
Note: Passive Vulnerability Scanner (PVS) is now Nessus Network Monitor. To learn more about this application and its latest capabilities, visit the Nessus Network Monitor web page.
After you apply the filter, change the view tools to Source IP Summary. If you have any host that sends queries to this domain, it has most likely been compromised. You should disconnect that machine from the network and take appropriate action.
Note: There are reports of some organizations attempting to block this domain at their firewalls, assuming this is a CnC domain. Don’t do that! The domain has been sinkholed and is actually a kill switch for the malware. If the malware can successfully reach that domain, it terminates - so don’t block access.
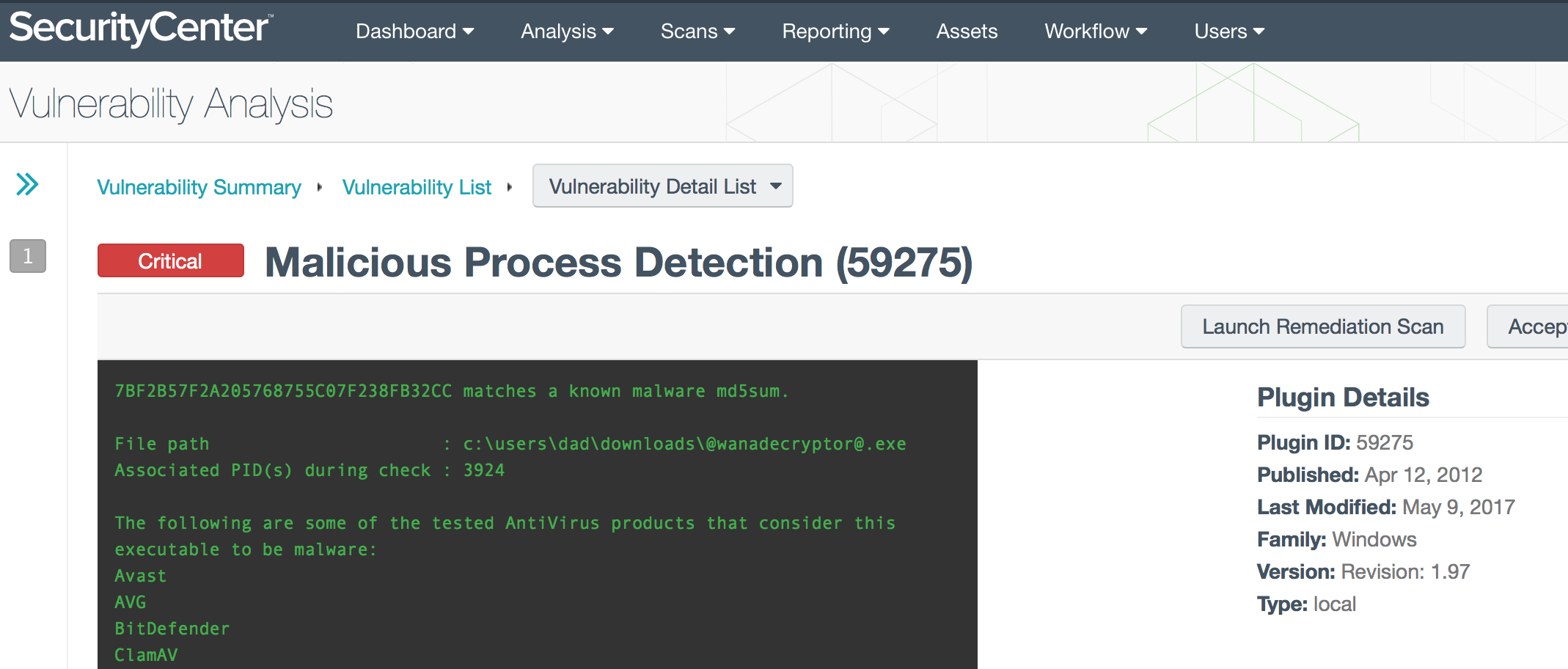
If you already have credentialed scans or Nessus Agents in place, detection is even easier; just use the Malware Scan Policy; machines infected with WCry will be reported under plugin 59275.
2. Hunt for infected machines by lateral movement.
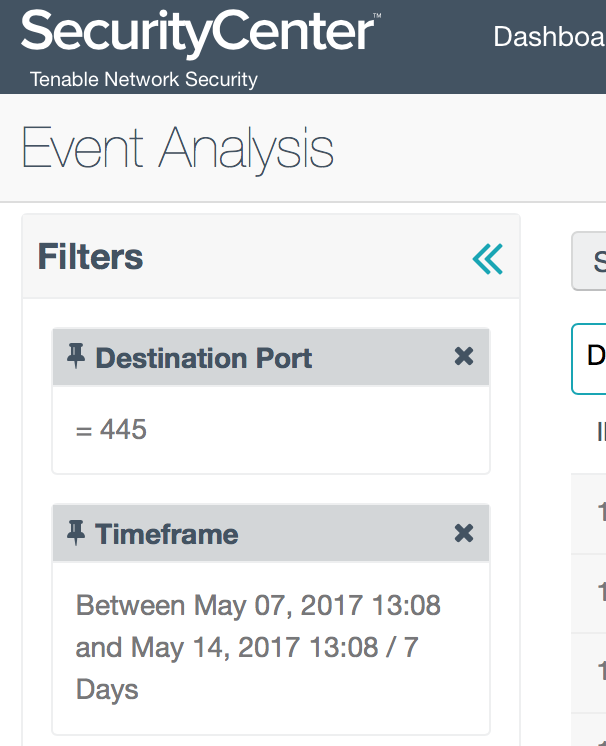
The WannaCry ransomware spread so quickly because once it infects one machine, it scans for any other machine with port 445 open, and then infects that target. With SecurityCenter, you can search for any hosts that are scanning for port 445, by applying this filter:
Destination Port = 445
Timeframe = Last 7 Days
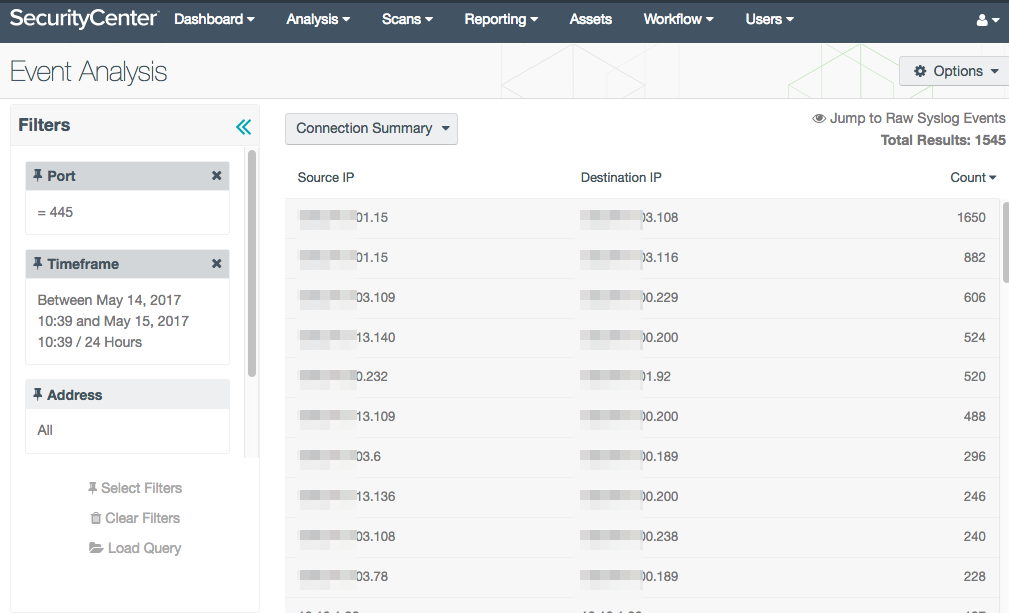
Using the Connection Summary tool you can identify hosts that are connecting to other hosts using port 445. For example, in the image below, one host has 1650 events using port 445 with another host. You may need to investigate a situation when the same host is talking to several other hosts. You can enhance these results by using Assets or subnets as additional filters.
3. Once your systems are clean, patch and scan.
If your environment is now clean, the best way to prevent a WCry infection is to apply patches and disable SMBv1. Tenable has several plugins that can detect if a machine is vulnerable to MS17-010:
|
Plugin ID |
Plugin |
Description |
|
96982 |
Server Message Block (SMB) Protocol Version 1 Enabled (uncredentialed check) |
The system has been found to be vulnerable to SMBv1 attacks using uncredentialed checks. The Shadow Brokers group reportedly has an exploit that affects SMB, and the current WannaCry ransomware is using this exploit. |
|
97086 |
Server Message Block (SMB) Protocol Version 1 Enabled |
This plugin is similar to 96982, but the vulnerability is detected using credentials. The system has been confirmed vulnerable to SMBv1 attacks used by WannaCry and vulnerabilities described by Shadow Brokers. Credentialed checks are more accurate and provide mode details. |
|
97737 |
MS17-010: Security Update for Microsoft Windows SMB Server (4013389) (ETERNALBLUE) (ETERNALCHAMPION) (ETERNALROMANCE) (ETERNALSYNERGY) |
Credentialed plugin to detect MS017-010 (detects the patch is missing) |
|
97833 |
MS17-010: Security Update for Microsoft Windows SMB Server (4013389) (ETERNALBLUE) (ETERNALCHAMPION) (ETERNALROMANCE) (ETERNALSYNERGY) (uncredentialed check) |
Remote plugin to detect the MS017-010 vulnerability |
|
700099 |
Ransomware Traffic Detected (WannaCry) |
This plugin uses passive techniques to determine if the remote system may be affected by ransomware that encrypts most or all of the files on a user’s computer. This attack is related to the WannaCry ransomware. |
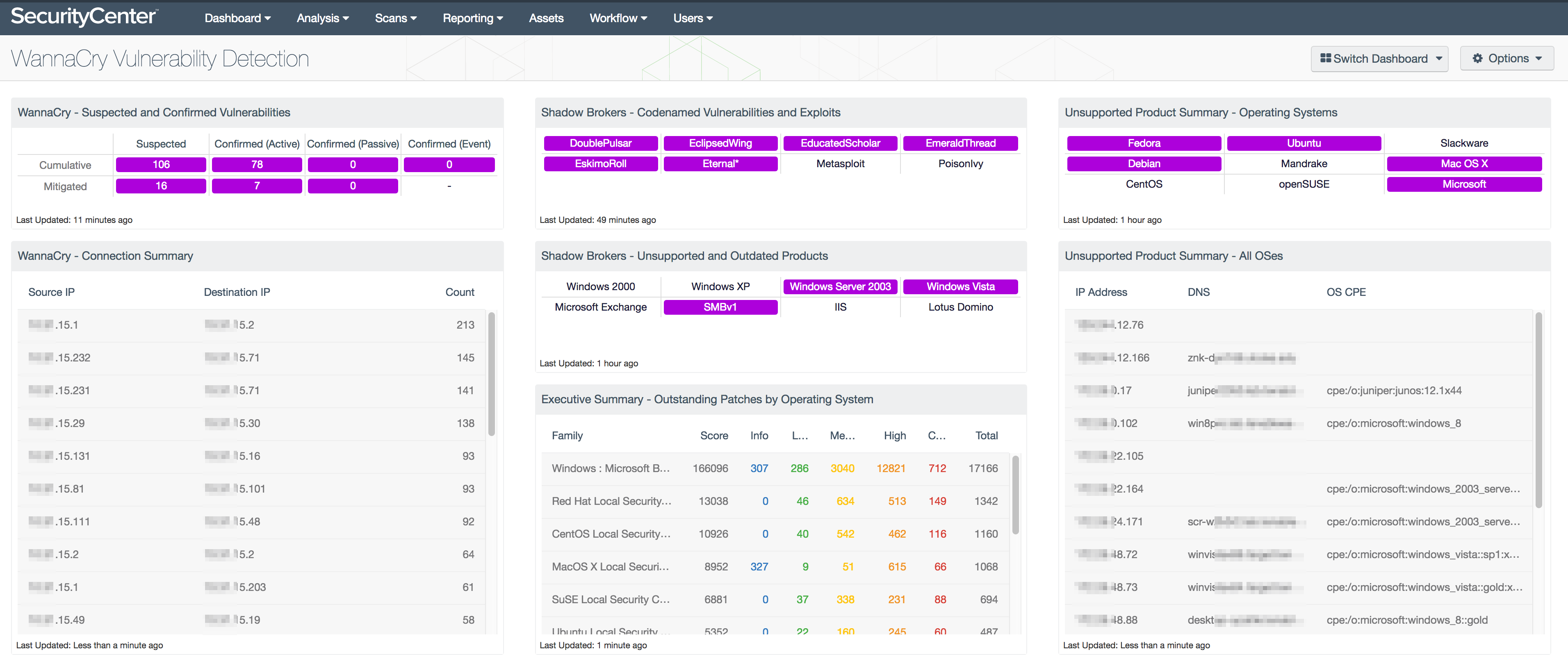
We have developed a SecurityCenter dashboard tailored to identify hosts that may be susceptible to the WannaCry ransomware exploitation. The WannaCry Vulnerability Detection dashboard is available through the SecurityCenter Feed to provide insight into the vulnerability of your network and the progress made toward upgrading outdated hosts.
The dashboard takes all the methods of detection described in this blog and places them into an easy to use and understand location. The matrix in the upper left hand corner uses CVEs and DNS events to identify possible at-risk hosts, vs. confirmed vulnerable hosts. The dashboard also uses many of the same components used in the Shadow Brokers Vulnerability Detection dashboard, and provides an overview of patching across all operating systems, to help you understand the current progress in patch deployments.
We also suggest patching other vulnerabilities disclosed by the Shadow Brokers group with the SecurityCenter Shadow Brokers Vulnerability Detection dashboard.
Tenable.io solutions
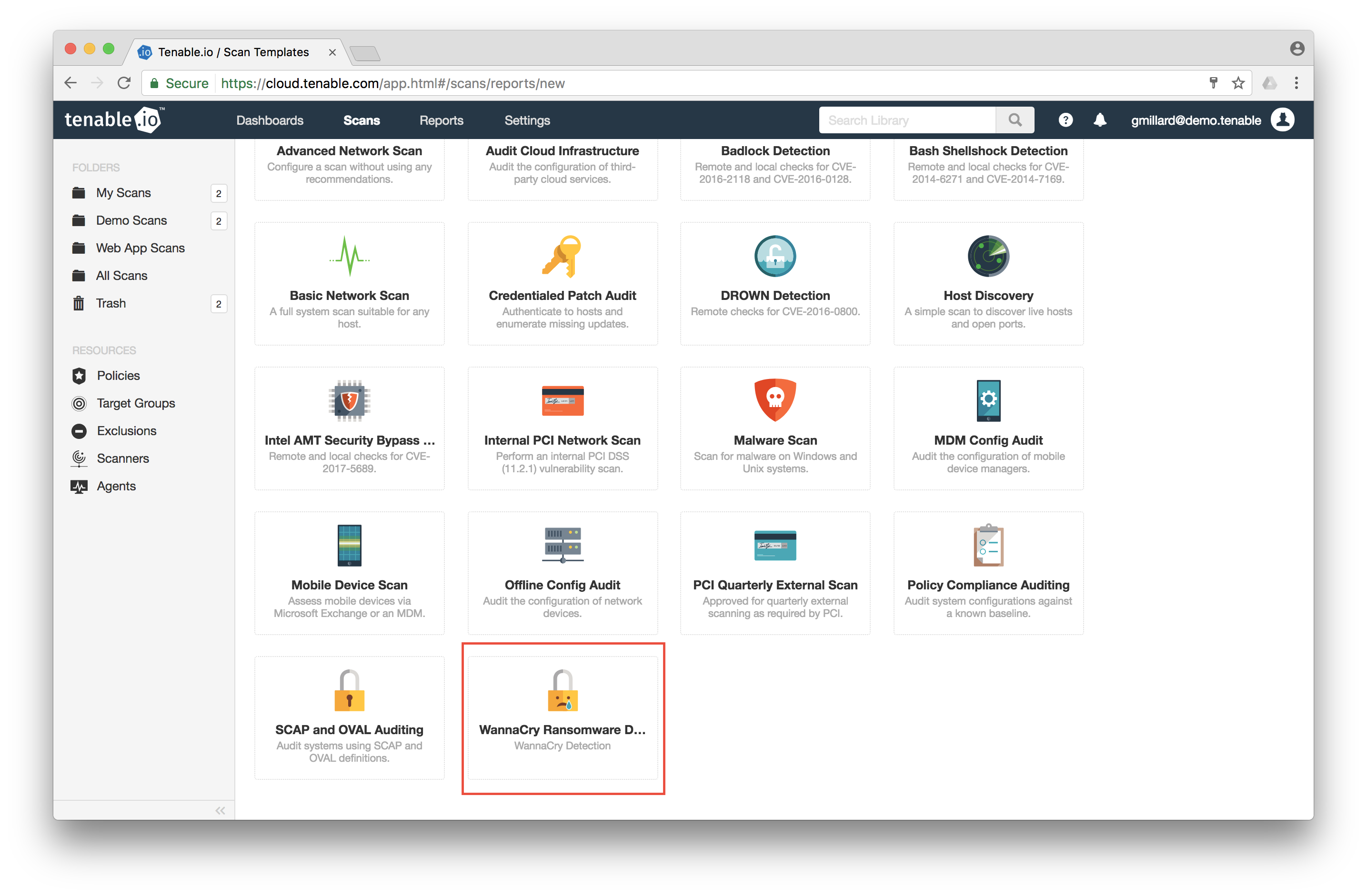
Tenable has also released an easy to use scan template for Tenable.io customers to quickly identify vulnerabilities targeted by the WannaCry malware or any derivatives that are sure to follow. The template scans for MS17-010 (CVE-2017-0144) both with and without credentials:
Take a look at this video which walks you through a few simple steps to detect potentially vulnerable hosts. To scan internal hosts, download a Nessus scanner and link it to your Tenable.io account.
If you aren’t a Tenable.io customer, you can sign up for a free 60 day evaluation.
An ounce of prevention
Most ransomware attacks are caused by exploits of known vulnerabilities that remain unpatched on systems. This is especially true for systems running outdated and unsupported operating systems. By patching all your assets regularly and creating regular backups of your data, you can help prevent ransomware attacks.
For more information
- How to Accidentally Stop a Global Cyber Attack (about the WannaCry malware)
- Customer Guidance for WannaCrypt Attacks (Microsoft TechNet notice)
- Back to Basics with the 2017 Verizon DBIR (see the section about ransomware, Don’t pay, remember to backup)
- What the Latest Shadow Brokers Dump Means for Your Business (Tenable blog about the April 2017 Shadow Brokers dump)
We have the following ransomware-focused educational webinars available for you to attend in the coming weeks:
- May 24 - Europe - English Language - 10 AM BST
- May 26 - Europe - German Language - 11 AM CEST
- June 8 - Americas - English Language - 2 PM ET/11 AM PT
Many thanks to Gavin Millard, Anthony Bettini, Cris Thomas, Cody Dumont and the entire Tenable research team for their contributions to this blog.
Updated May 23, 2017.
- Malware
- Plugins
- Threat Management
- Vulnerability Scanning