Uncovering the Business Costs of Cyber Risk: Ponemon Study

Study finds organizations are not accurately measuring the business costs of cyber risk, and are unable to quantify the damage cyber attacks could have on their businesses, leaving them without the critical information needed to make decisions about resource allocation, technology investments and threat prioritization.
Unlike other business disciplines (CRM, ERP, HR), cybersecurity lacks the kind of clear business metrics which can help executives frame decision-making in a language the c-suite and board easily understand. When we commissioned Ponemon Research to study the effects of cyber risk on business operations, our goal was to explore how four common KPIs associated with cyber exposure translate to specific types of business risk. We wanted to go beyond assessing pure dollar impact, exploring how cyber risk influences business strategy, products, supply chain, revenue streams, operations, business technology, customer experience and regulatory compliance.
What we discovered -- after surveying 2,410 IT and infosec decision-makers in six countries -- is that traditional KPIs or metrics for evaluating business risks cannot be used to understand cyber risks. Organizations are not accurately measuring the business costs of cyber risk, and are unable to quantify the damage cyber attacks could have on their businesses. Thus, decisions about the allocation of resources, investments in technologies and the prioritization of threats are being made without critical intelligence. Moreover, organizations are unable to correlate the cyber risk KPIs they are using to the mitigation of a data breach or security exploit.
At a time when boards of directors are taking more interest in cybersecurity than ever before, the study Measuring & Managing the Cyber Risks to Business Operations, conducted by Ponemon Institute on behalf of Tenable, reveals a lack of faith among cybersecurity professionals in the accuracy of their metrics. This makes CISOs and/or other security technology executives reluctant to share critical information about the business costs of cyber risks with their boards.
Exploring common KPIs
For the study, we identified four common KPIs used to measure cyber risk:
- time to assess;
- time to remediate;
- effectiveness of prioritizing cyber risk; and
- identification of assets vulnerable to cyber risk -- including Operational Technology (OT) and Internet of Things (IoT) devices.
In addition, we explored three KPIs most often used to measure the financial consequences of a cyber attack:
- loss of revenue;
- loss of productivity; and
- drop in stock price.
The vast majority of respondents (91%) admitted they’ve experienced at least one business-disrupting cyber incident in the past 24 months; 60% have experienced two or more incidents in the same time frame. These attacks have resulted in data breaches and/or, significant disruption and downtime to business operations, plants and operational equipment.
The majority of respondents (58%) say traditional KPIs or metrics for evaluating business risks cannot be used to understand cyber risks. When it comes to quantifying the damage cyber events could have on their businesses, only 41% of respondents (988) say their organizations make any attempt to do so. Further, only 30% of respondents say their organizations are able to correlate information from cyber risk KPIs to taking action on reducing the risk of a data breach or security exploit.
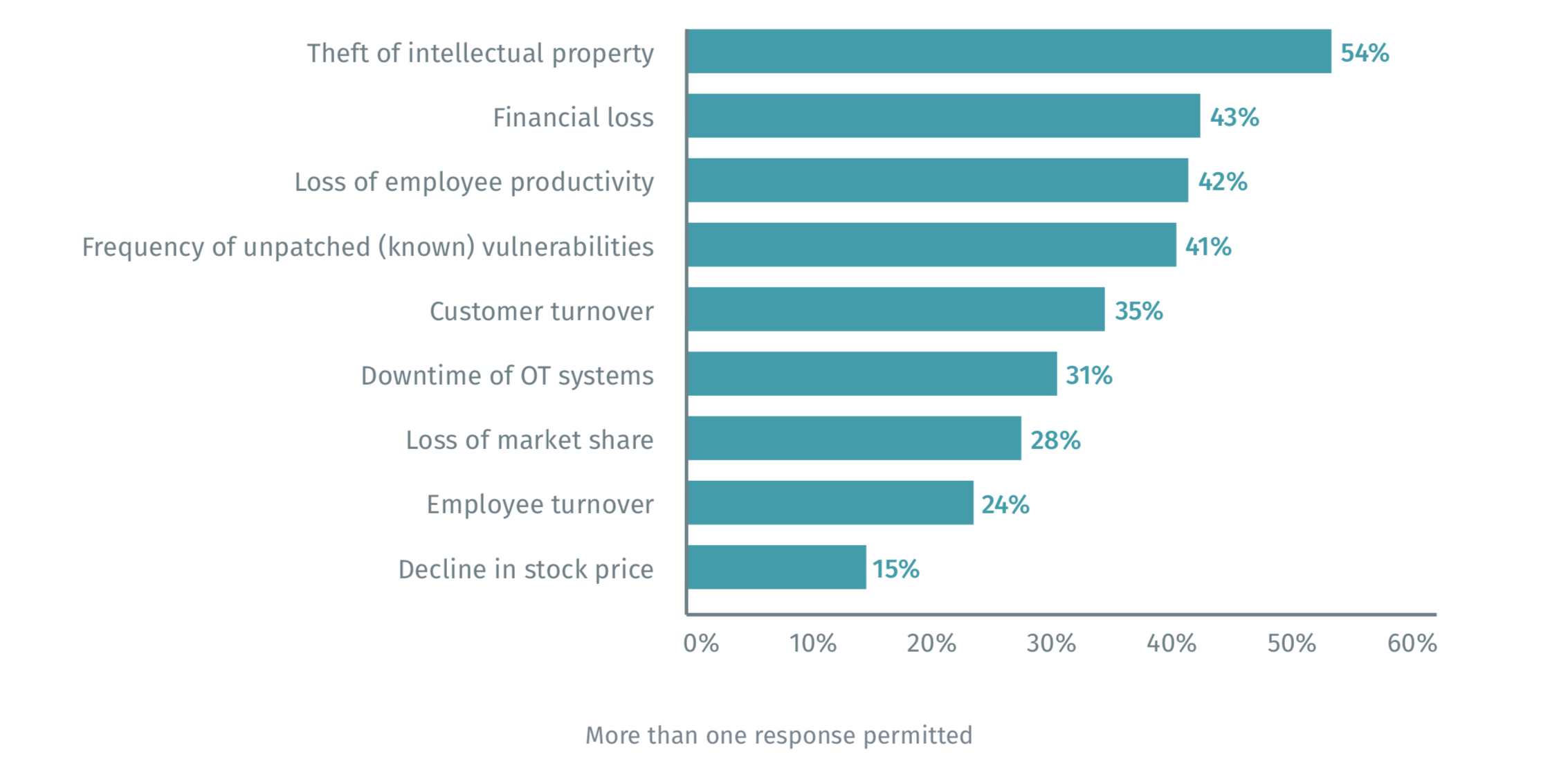
Of the 988 respondents who said their organizations attempt to quantify the damage security incidents could have on their businesses:
- 54% say they quantify what the theft of intellectual property would cost;
- 43% say they calculate the potential financial loss; and
- 42% consider the impact of the loss of employee productivity following a data breach or security exploit.
What factors are used to quantify the potential risk of a cyber attack?
原文:Measuring & Managing the Cyber Risks to Business Operations, Ponemon Institute & Tenable, December 2018.
We asked respondents to rate the accuracy of the information gathered using the above KPIs, measured on a scale of 1 = not accurate to 10 = very accurate. Only 38% of respondents believe their measures are very accurate, while 44% believe their measures are not very accurate.
The report also reveals organizations are not using the KPIs they consider most important to assessing and understanding cyber threats. For example, two thirds of respondents (64%) identified “time to assess” as an important KPI for evaluating cyber risk, yet only 49% of respondents are currently using this metric. We see similar gaps when we look at the three other KPIs discussed in the report (see below).
Gaps in use and importance of KPIs
| KPI | Used by (% respondents) | Considered essential (% respondents) |
|---|---|---|
| Time to assess cyber risk | 49% | 64% |
| Time to remediate cyber risk | 46% | 70% |
| Identifying OT and IoT assets | 34% | 62% |
| Prioritization effectiveness | 38% | 57% |
原文:Measuring & Managing the Cyber Risks to Business Operations, Ponemon Institute & Tenable, December 2018.
Measuring cyber risk: Nobody said it was easy
Respondents identified seven key reasons why their organizations continue to face cybersecurity challenges, including:
- An understaffed IT security function.
- Lack of resources to manage vulnerabilities.
- The proliferation of IoT devices in the workplace.
- The complexity of the IT security infrastructure.
- Lack of controls over third-party access to sensitive and confidential data.
- Dependency on manual processes to respond to vulnerabilities.
- Insufficient visibility into their organization’s attack surface.
While there are no quick-and-easy fixes to any of these issues, we believe focusing on the following five steps will help put your organization on the right path to building a business-first cybersecurity strategy.
- 辨識及對應任何運算環境中的每項資產。
- 瞭解所有資產的 Cyber Exposure 程度,包含弱點、設定錯誤和其他資安狀況指標。
- Understand exposures in context, to prioritize remediation based on asset criticality, threat context and vulnerability severity.
- 排定需優先修復的曝險 (如果有的話),並採用適當的修復技術。
- 測量 Cyber Exposure 程度並進行指標分析,以作出更完善的業務和技術決策。
In addition to the above guidance, the report, Measuring & Managing the Cyber Risks to Business Operations, concludes with a five-step process for measuring and managing cyber risk you can put into action in your own organization today.
About this study
The report Measuring & Managing the Cyber Risks to Business Operations is based on a survey of 2,410 IT and IT security decision-makers in the United States, United Kingdom, Germany, Australia, Mexico and Japan. All respondents have involvement in the evaluation and/or management of investments in cybersecurity solutions within their organizations. The consolidated global findings are presented in this report. Download your free copy here.
- Federal
- Financial Services
- Government
- Internet of Things
- Metrics
- Research Reports
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning

