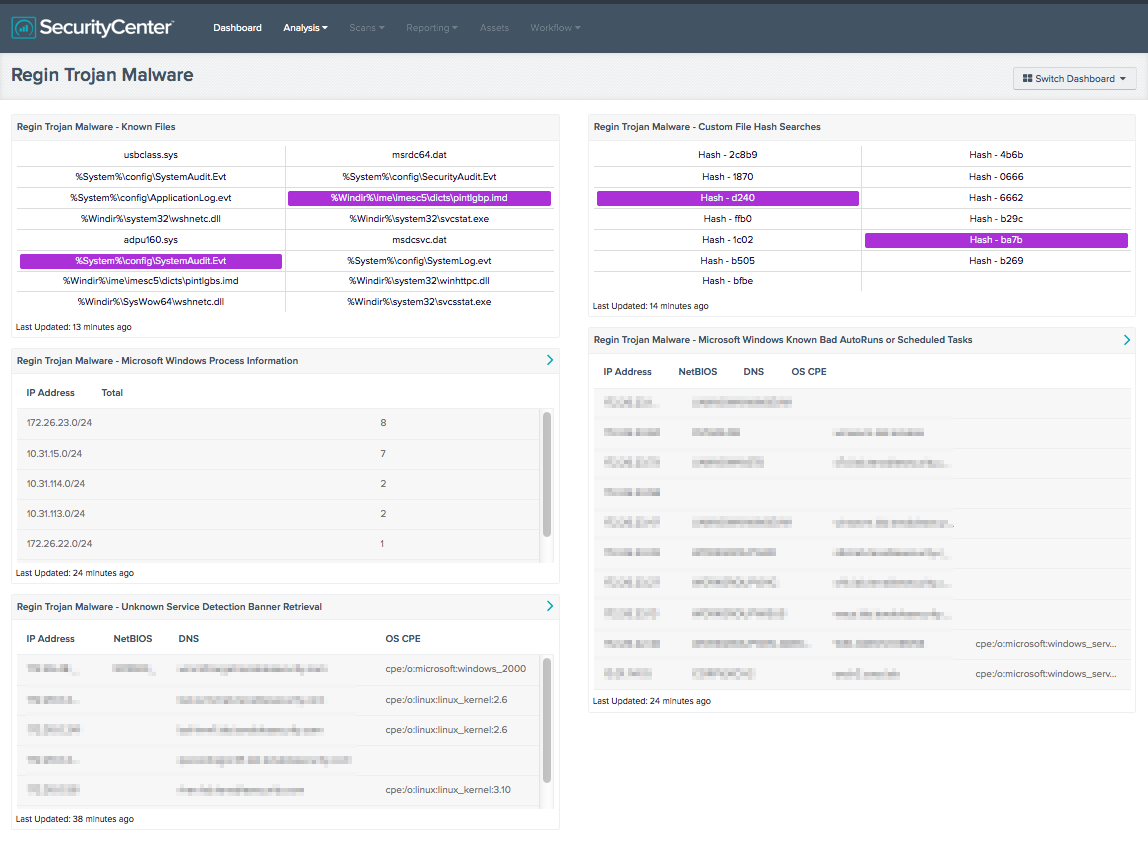
Regin Malware: Its Targets and How You Can Detect It

On the 24th of November 2014, a major anti-malware vendor released a report concerning a long running piece of backdoor Trojan malware, now called “Regin.” We at Tenable Network Security were aware of this report on the Sunday before the release, and looked forward to reading the technical analysis. The report went into great detail and we were able to leverage it to discuss multiple indicators of compromise (posted in our Discussion Forums) which will help you see if your systems are compromised. We have also created a new dashboard for our SecurityCenter Continuous View™ customers to detect and monitor for Regin indicators.
Attack targets
Fortunately, most people reading this blog will not have to check for infection. This piece of malware, while highly advanced, is not wide spread. In all probability, Regin is a state-sponsored piece of “espionageware,” a class of malware that is being sponsored by states to spy on other states, not to drain your personal bank book, to harvest bitcoins, or in any other way adversely impact individual computer and Internet users. While some of its functions (such as acting as a proxy for other Regin infected hosts) may impact machines that they are hosted on as an unintended consequence, Regin is not targeted at the end user.
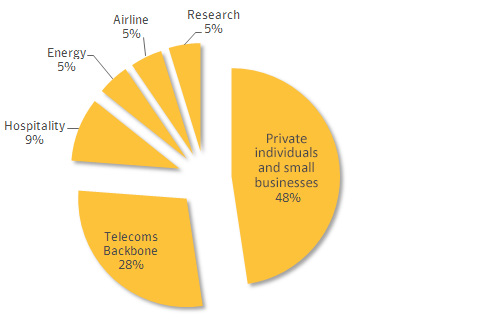
But according to the reports, infection is distributed across unexpected sectors. While Regin isn’t designed to perform malicious actions against individual users, those users and small businesses make up the bulk (48%) of the infected parties. Telecom backbones are the second largest sector, making up 28% of the infected systems.
Some people have compared Regin to Stuxnet for its complexity. Regin does display a high level of sophistication and multiple layers of activities, combined with encryption both in the files and the communications channels. What we can say for certain is that writing this malware took time and energy not normally associated with malware authorship. While there are indications that Regin has been active for the last six years, it’s worth noting that it wasn’t discovered until an update was made in 2013.
There have been many write-ups dissecting the original paper, which is a good read in itself. While the technical aspects are interesting, I think it’s better to look at this from a different perspective. Unless you’re in one of the targeted countries, there’s little chance for infection from the currently identified threats. With that said, the targeted nations are:
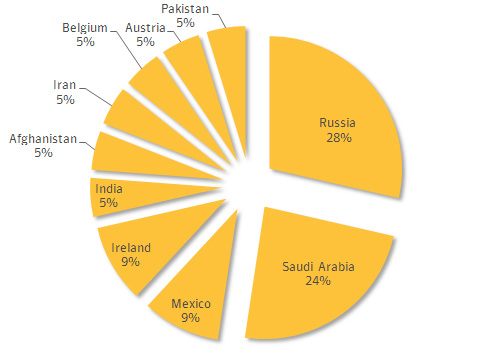
While this data is from confirmed reports, we cannot discount other variants being active in non-detected nations. Now that the details and samples are out, other nations/actors can redesign to meet their needs and have future variants targeting other nations, possibly even the originating organization.
Regin’s Achilles' heel
While Regin is complex and goes to great means to hide its presence and covertly communicate, its key weakness is communications. In order to update, and to report the captured keylogs back to their source of control, Regin performs bi-directional communications. This weakness is common in botnets and espionageware. We at Tenable Network Security have been advocating the need to monitor abnormal network activity for some time. While detecting network abnormal traffic isn’t the same as preventing the malware, it often leads to detection of compromised hosts and allows organizations to monitor or close those communications points.
Tenable tools
Tenable developers have created a special dashboard in SecurityCenter Continuous View™ to detect and monitor for the Regin indicators.
The Regin Malware Dashboard and its components are available in the SecurityCenter Feed, an app store of dashboards, reports, and assets. The dashboard can be easily located in the SecurityCenter Feed by selecting category Threat Detection & Vulnerability Assessments, and then selecting tags malware & processes.
- Anti-malware
- Dashboards
- Malware
- SecurityCenter