Protecting Your Bluetooth Devices from BlueBorne

A new attack vector, codenamed BlueBorne, can potentially affect all devices with Bluetooth capabilities – ordinary computers, mobile phones, and IoT devices – literally billions of devices in the world today. Hackers can use this attack vector to leverage Bluetooth connections to completely take over targeted devices.
BlueBorne spreads through the air, allowing it to bypass all security measures and potentially infect even “air-gapped” networks. The attack does not require the attacker’s device and the targeted device to be paired; in fact, the targeted device does not even need to be set on discoverable mode. The BlueBorne attack vector requires no user interaction, no connection to the internet, covers multiple OS versions, and does not require any special configuration other than Bluetooth being active on the targeted device. BlueBorne is completely undetected by the user and can be used for a large range of attacks, including remote code execution and man-in-the-middle attacks, ransomware, creating IoT botnets and more.
Tenable Coverage
CVE-2017-8628, CVE-2017-1000250 and CVE-2017-1000251 cover the vulnerabilities that allow the BlueBorne attack vector to succeed in Windows and Linux environments. Tenable has released following plugins to address those CVEs:
| Plugin ID | Plugin Name | CVE |
|---|---|---|
| 103127 | KB4038777: Windows 7 and Windows Server 2008 R2 September 2017 Cumulative Update | CVE-2017-8628 |
| 103128 | KB4038782: Windows 10 Version 1607 and Windows Server 2016 September 2017 Cumulative Update | CVE-2017-8628 |
| 103129 | KB4038783: Windows 10 Version 1511 September 2017 Cumulative Update | CVE-2017-8628 |
| 103130 | KB4038788: Windows 10 Version 1703 September 2017 Cumulative Update | CVE-2017-8628 |
| 103131 | KB4038792: Windows 8.1 and Windows Server 2012 R2 September 2017 Cumulative Update | CVE-2017-8628 |
| 103140 | Windows 2008 September 2017 Multiple Security Updates | CVE-2017-8628 |
| 103144 | CentOS 6 : kernel (CESA-2017:2681) | CVE-2017-1000251 |
| 103145 | CentOS 6 : bluez (CESA-2017:2685) | CVE-2017-1000250 |
| 103196 | CentOS 7 : kernel (CESA-2017:2679) | CVE-2017-1000251 |
| 103198 | Debian DSA-3972-1 : bluez - security update | CVE-2017-1000250 |
| 103202 | Fedora 26 : bluez (2017-fe95a5b88b) | CVE-2017-1000250 |
| 103165 | Oracle Linux 6 : kernel (ELSA-2017-2681) | CVE-2017-1000251 |
| 103164 | Oracle Linux 7 : kernel (ELSA-2017-2679) | CVE-2017-1000251 |
| 103166 | Oracle Linux 6 / 7 : bluez (ELSA-2017-2685) | CVE-2017-1000250 |
| 103169 | RHEL 6 : kernel (RHSA-2017:2681) | CVE-2017-1000251 |
| 103170 | RHEL 6 : kernel (RHSA-2017:2682) | CVE-2017-1000251 |
| 103171 | RHEL 6 : kernel (RHSA-2017:2683) | CVE-2017-1000251 |
| 103208 | RHEL 6 : kernel (RHSA-2017:2707) | CVE-2017-1000251 |
| 103167 | RHEL 7 : kernel (RHSA-2017:2679) | CVE-2017-1000251 |
| 103168 | RHEL 7 : kernel (RHSA-2017:2680) | CVE-2017-1000251 |
| 103207 | RHEL 7 : kernel (RHSA-2017:2706) | CVE-2017-1000251 |
| 103206 | RHEL 7 : kernel-rt (RHSA-2017:2704) | CVE-2017-1000251 |
| 103172 | RHEL 6 / 7 : bluez (RHSA-2017:2685) | CVE-2017-1000250 |
| 103174 | Scientific Linux Security Update : kernel on SL6.x i386/x86_64 | CVE-2017-1000251 |
| 103175 | Scientific Linux Security Update : kernel on SL7.x x86_6 | CVE-2017-1000251 |
| 103173 | Scientific Linux Security Update : bluez on SL6.x, SL7.x i386/x86_64 | CVE-2017-1000250 |
| 103187 | Ubuntu 14.04 LTS / 16.04 LTS / 17.04 : bluez vulnerability (USN-3413-1) | CVE-2017-1000250 |
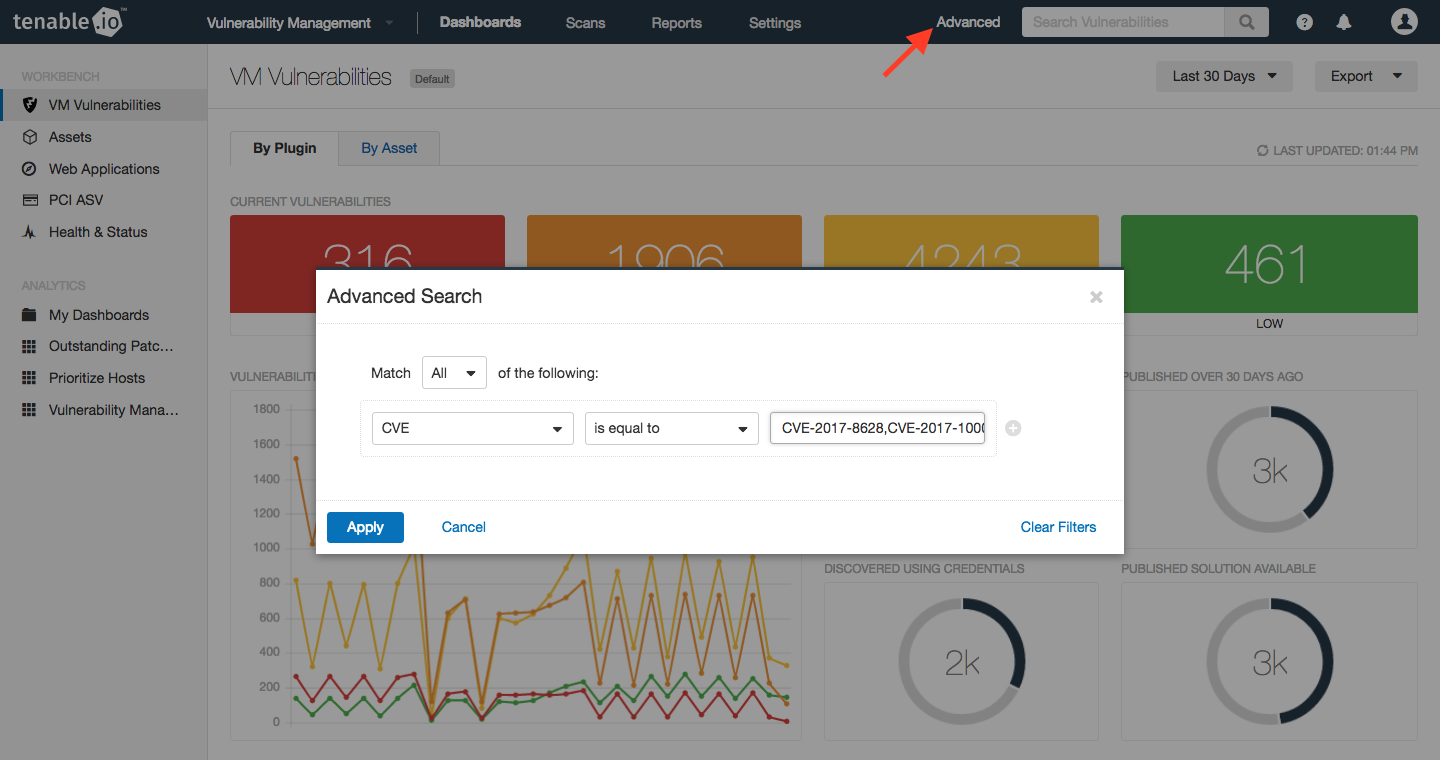
To find your vulnerable systems, in the Tenable.io Vulnerability Workbench, click on “Advanced” and do a search for CVE equal to “CVE-2017-8628,CVE-2017-1000250,CVE-2017-1000251” (note that there are no spaces after the commas):
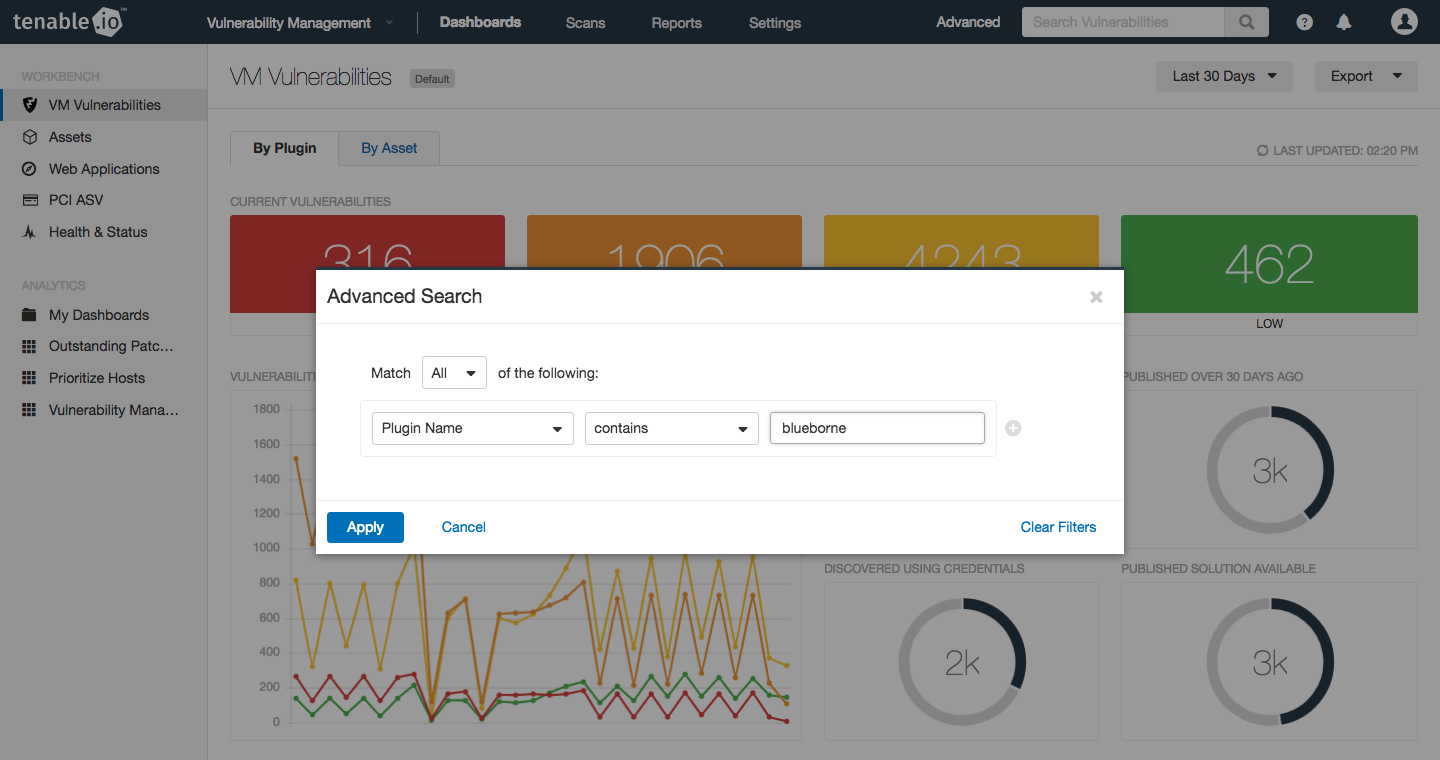
Additional Tenable.io vulnerability detection plugins related to BlueBorne will have “BlueBorne” in their names. To do a search for these vulnerabilities, click on “Advanced” in the Tenable.io vulnerability workbench and do a search for Plugin name contains “blueborne” (the search is not case sensitive):
Also note that Plugin 43830 (WMI Bluetooth Network Adapter Enumeration) can be used for finding Bluetooth network adapters on your Windows systems.
Now What?
If you’ve discovered that you have vulnerabilities that could be exploited by BlueBorne, you should update your systems as soon as possible. Microsoft has already issued security patches to all supported Windows systems, with coordinated notification on Tuesday, September 12. Patches for the various Linux OS distros have also been released. Devices running iOS 10 already have the vulnerability mitigated, but all iPhone, iPad and iPod touch devices with iOS 9.3.5 and lower, and AppleTV devices with version 7.2.2 and lower are vulnerable.
- Internet of Things

