Intro to the Tenable.io API
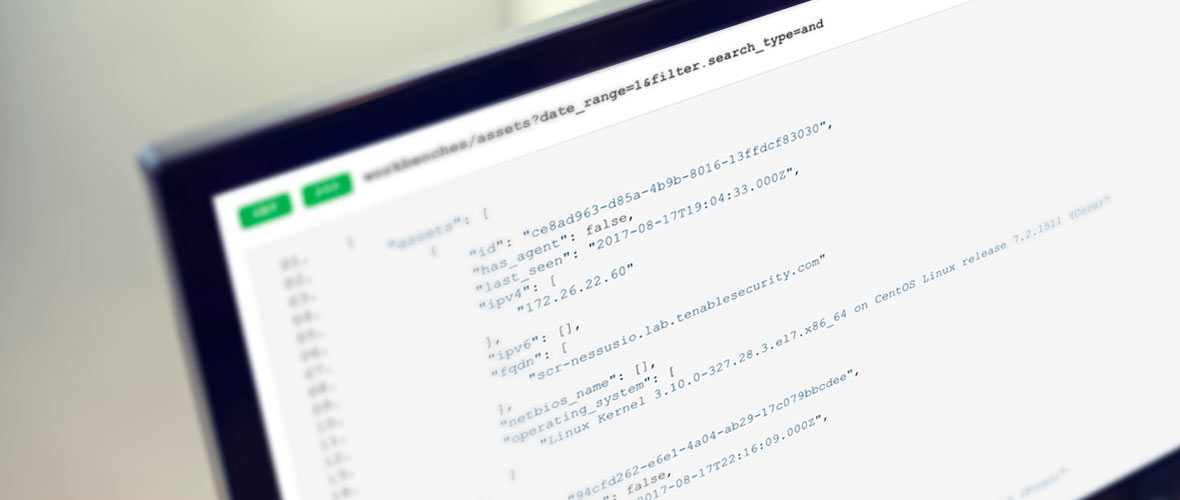
Tenable.io is the world’s first Cyber Exposure platform, giving you complete visibility into your network and helping you to manage and measure your modern attack surface. All the powerful capabilities of Tenable.io Vulnerability Management are available in the Tenable.io API, a robust, well-documented tool for users of all experience levels. Tenable.io users can access the API via the publicly available web interface. Highly technical users can leverage the API using utilities like cURL or Postman to gather data in an automated fashion and get additional details that may not be readily available via the web UI.
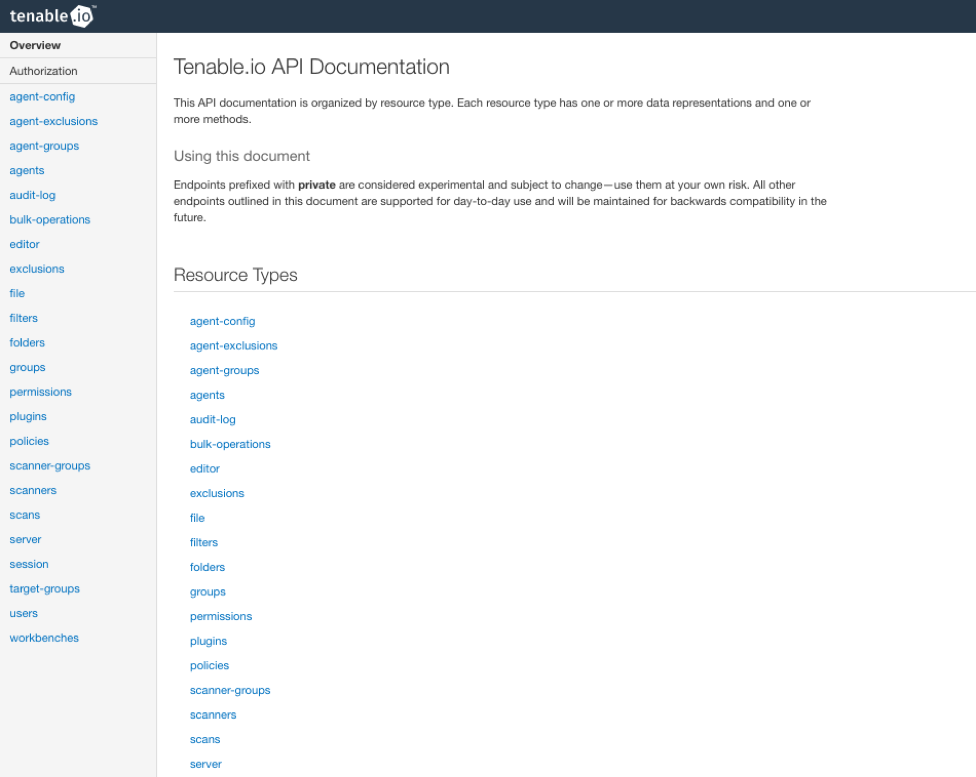
Using the Tenable.io API
Using the Tenable.io API web UI allows you to leverage many of the API’s capabilities without having to be familiar with crafting API queries or using utilities like cURL or Postman.
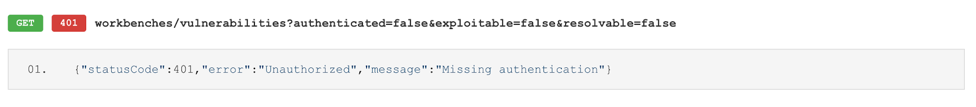
The key to leveraging the API UI that isn’t necessarily obvious is most requests require you to be authenticated. This is most easily accomplished by having two windows or tabs open: one with your authenticated Tenable.io session and one with the Tenable.io API. This lets the Tenable.io API use your authenticated session to perform the queries. If you fail to authenticate before attempting to send API queries, you will usually get an error like the one below. After authenticating, refresh the API page and the error should be resolved.
Suggested queries
The API accepts queries against 19 different data types, with more than a hundred methods and additional filters or parameters. The API can be used to: create and control scans, add users or configure permissions, modify or create scan policies and perform dozens of other tasks. Many of these tasks could be useful to automate through scripting API queries, but a foundational understanding of the Tenable.io API is necessary.
Getting a list of assets in your Tenable.io container
The API UI is a great way to build an understanding of what the various methods, requests and parameters do. As an example, let’s step through how to get a list of all the assets in your Tenable.io container:
- First, make sure you have authenticated to Tenable.io and have the API UI open.
- Next, click workbenches in the left bar, and then click assets.
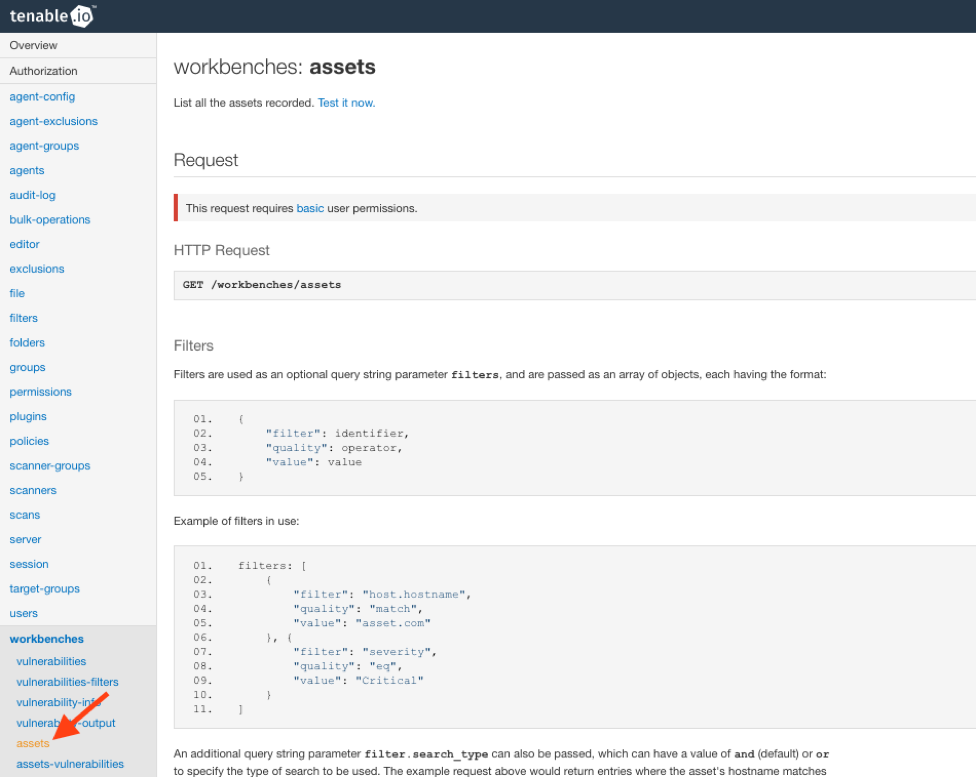
- Now, scroll to the bottom of the webpage, where the Test section is shown.
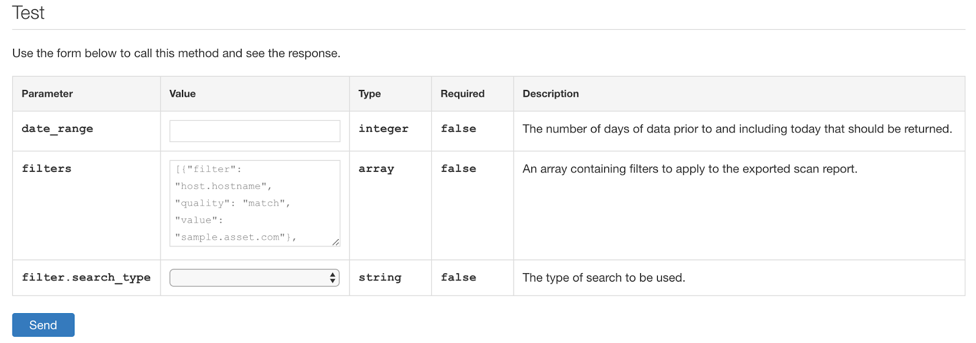
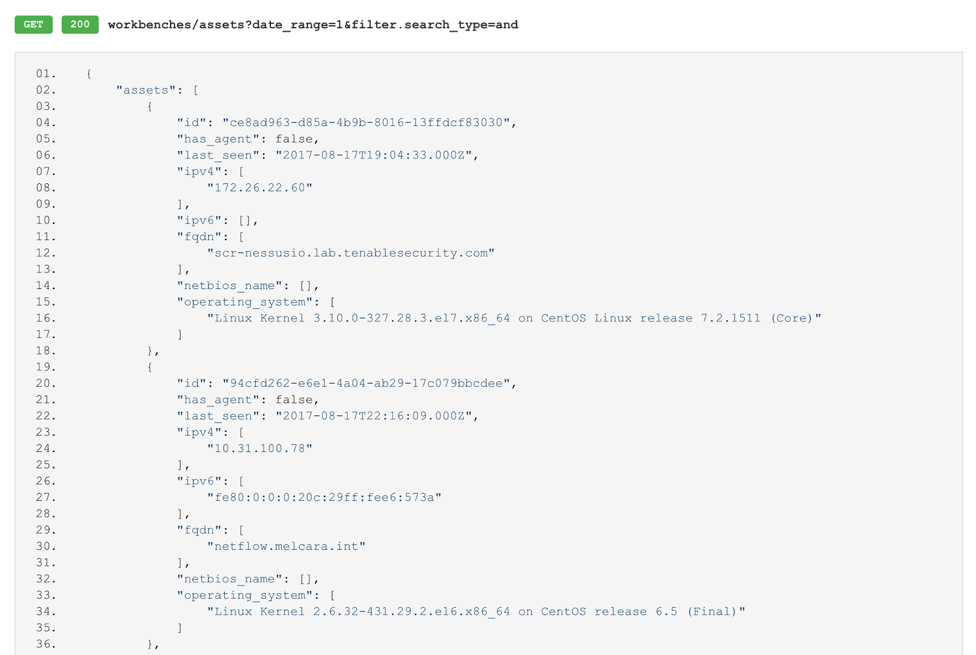
As you can see, there are a few optional parameters for filtering the results of the query. For now, let’s leave those as the defaults and click Send. Once the request completes, you’ll receive a list of your assets and details about them in JSON format.
Getting a list of vulnerabilities
The workbenches > vulnerabilities query works similarly, but has more parameters available for configuration. Setting any of these parameters will filter the results of your query, allowing you to tailor your results based on what you’re looking for.
A quick word on the filters field: you can define an array of filters that’ll be logically connected by either “and” or “or,” as defined in the “filter.search_type” field. An example filter is shown grayed out in the filter field. This example filter isn’t actually applied when the query is run, but any filter you enter will be applied. Additional filter details are given in the Filters section farther up the webpage.
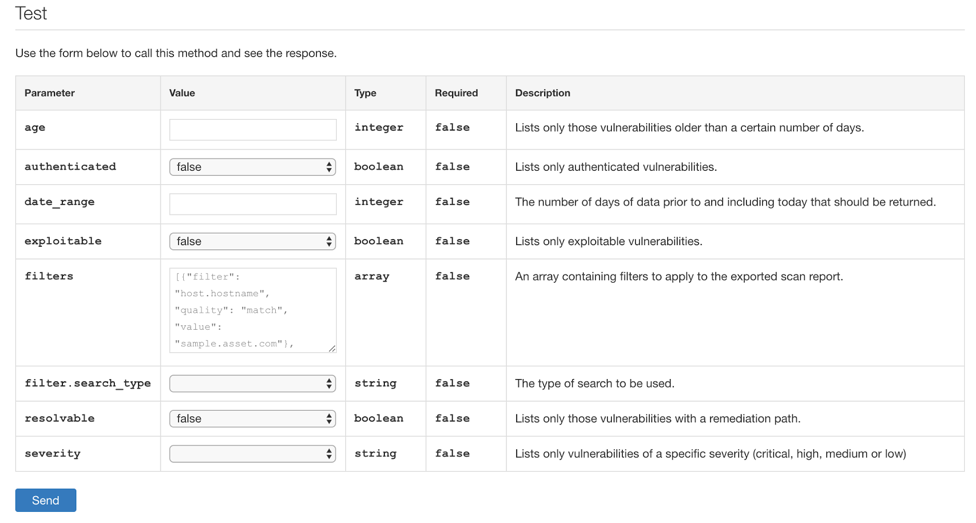
The response to the vulnerabilities query won’t provide details about individual plugins or the vulnerability results. However, from the list, you can grab a plugin ID to use in other queries. Set the plugin ID in the workbenches > vulnerability-info query to get more information about the plugin. Set the plugin ID in the workbenches > vulnerability-output query to get vulnerability results such as the assets where the vulnerability was found.

Using other API utilities
The Tenable.io API UI can help you build a sufficient foundation so that you can then perform more complex requests via other API utilities such as cURL or Postman. As usual, authentication is necessary with these utilities before the requests for data will work. A POST to <https://cloud.tenable.com/session> with your credentials in the body will give you the session token you need to perform data queries. The cURL request for getting your authenticated session token would look similar to this, but with your own credentials (note that because this is a POST request to an https URL, your credentials are not being transmitted in the clear!):
curl -X POST -H "Content-Type: application/json" -H "Cache-Control: no-cache" -d '{"username":"[email protected]", "password":"YourPasswordHere"}' "https://cloud.tenable.com/session"
Once you have the session token, you can perform queries to accomplish any of the tasks available via the API UI. In the API UI, look at the HTTP Request information to get the proper method and URL syntax to run a query. For example, this query would provide you with your list of scans and details about them:
curl -X GET -H "X-Cookie: token=YourSessionTokenHere" -H "Cache-Control: no-cache" "https://cloud.tenable.com/scans"
A request like this one would return your list of target groups:
curl -X GET -H "X-Cookie: token=YourSessionTokenHere" -H "Cache-Control: no-cache" "https://cloud.tenable.com/target-groups"
And this request closes down your session:
curl -X DELETE -H "X-Cookie: token=YourSessionTokenHere" -H "Cache-Control: no-cache" "https://cloud.tenable.com/session"
Any of these cURL requests can be easily modified for use in Postman or scripting in various languages.
The Tenable.io solution
Even if you’re not a customer yet, you can still take a look at the Tenable.io API today right in your browser. The API is publicly available and, as you’ll see, is fully documented. Once you become a Tenable customer, all the capabilities of Tenable.io Vulnerability Management – accurate asset tracking, vulnerability states, workbenches and reports and more – are available in the API, so that customers and partners can use any data they need in an automated fashion. The API is also fully equipped for use via various API utilities or scripting in many languages.
Start your free 60-day trial of Tenable.io Vulnerability Management now!
Start free trial- Tenable Vulnerability Management


