Cybersecurity Snapshot: Cyber Engineers and Architects Saw Salaries Spike in 2022

Find out how much of a pay bump cybersecurity architects and engineers got. Plus, a powerful AI cybersecurity tech is nearing prime time. Also check out the long-awaited security algorithms for IoT devices. Then dive into SaaS governance best practices. And much more!
Dive into six things that are top of mind for the week ending Feb. 24.
1 - Study: Salaries go up for cyber architects and engineers
Employers are showing cybersecurity architects and cybersecurity engineers the money.
Salaries rose overall for U.S. technology employees in 2022, and the pay growth was even higher for cybersecurity architects and engineers, whose compensation benefitted from their highly specialized skills and the criticality of their jobs.
That’s according to Dice.com’s annual “Tech Salary Report,” released this week. Here are some key takeaways from the report, now in its 18th year.
- Cybersecurity architects and cybersecurity engineers ranked fifth among average tech salaries by occupation with $145,512
- That average salary for cybersecurity architects and engineers grew 7.7% compared with 2021, which ranks sixth on the list of fastest-growing tech salaries by occupation
- Among certifications, CompTIA Security+ was the most popular cybersecurity one, ranking third on the list of technical certifications with 16% of respondents having it
- The average tech salary across all roles grew 2.3% in 2022 to $111,348, and, despite tech industry layoffs, tech unemployment stood at only 1.5% as of last month
Average Tech Salary by Occupation
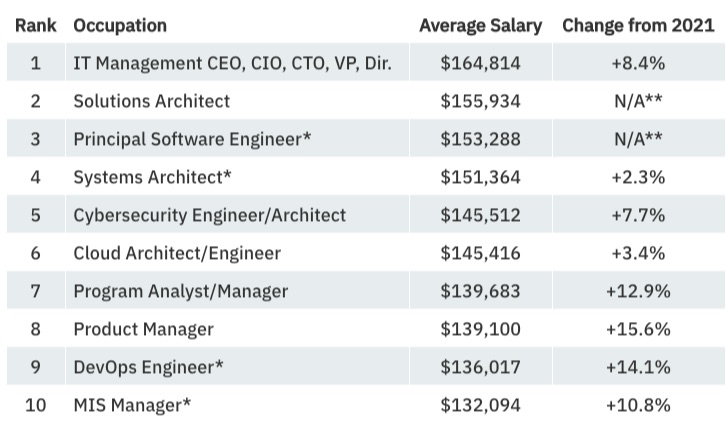
(Source: “Dice Tech Salary Report: 2023 Edition”, February 2023)
However, salaries didn’t trend higher for cybersecurity pros across the board, according to Dice, which is a tech-focused careers website. For example, cybersecurity analysts saw their average salary shrink 5.7% in 2022 to $96,379.
For more details, read the full “Dice Tech Salary Report,” which is based on a poll of 7,098 U.S. respondents, and check out these Dice.com articles and videos that drill down on specific areas of the study:
- “Dice Tech Salary Report: 4 Key Takeaways”
- “Which Tech Hubs Have the Highest Layoff Anxiety?”
- “How Is the Tech HR Landscape Changing?”
- “Are Software Engineers at Tech Giants Still Earning High Salaries?”
The 2023 Dice Tech Salary Report
Dice Tech Salary Report: Guide to Increase Your Salary in 2023
2 - A peek at how AI will help cyber teams with complex attacks
Can artificial intelligence help cybersecurity teams make better decisions to prevent and disrupt complex, multi-stage cyberattacks in real time? Apparently AI technology is getting there, according to the results of a study conducted by the U.S. government.
In their paper “Deep Reinforcement Learning for Cyber System Defense under Dynamic Adversarial Uncertainties,” researchers from the U.S. Pacific Northwest National Laboratory (PNNL) tested the efficacy of AI deep reinforcement learning (DRL) algorithms to proactively and autonomously defend systems facing evolving and uncertain attacker behaviors.

After putting the technology to the test in a custom simulation environment, the researchers concluded that “application of DRL methods for cyber system defense are promising, especially under dynamic adversarial uncertainties and limited system state information.”
While the technology still needs to be further refined, “evaluating multiple DRL algorithms trained under diverse adversarial settings is an important step toward practical autonomous cyber defense solutions,” the researchers wrote.
To get more details, read the research paper and the lab’s announcement of its findings, as well as coverage from Dark Reading and AI Magazine.
For more information about the use of DRL for cybersecurity:
- “Optimizing cybersecurity incident response decisions using deep reinforcement learning” (International Journal of Electrical and Computer Engineering)
- “Reinforcement learning models are prone to membership inference attacks” (TechTalks)
- “What’s hot in AI: Deep reinforcement learning” (VentureBeat)
- “Deep Reinforcement Learning for Cybersecurity Threat Detection and Protection: A Review” (Semantic Scholar)
VIDEOS
Adversarial Policy Training against Deep Reinforcement Learning (USENIX Security ‘21)
Adversarial Policies: Attacking Deep Reinforcement Learning (Computer Vision Seminar)
3 - NIST picks lightweight algorithms to protect IoT devices
With the security of internet of things (IoT) devices a chronic concern among cyber teams, a years-long effort from the U.S. government to help in this area is nearing completion.
The U.S. National Institute of Standards and Technology (NIST) recently announced its selection of lightweight cryptography algorithms designed to protect the data that IoT devices and other small electronics generate and transmit.

The chosen “lightweight” algorithms, which are known collectively as Ascon and will be published later this year, are designed for tiny devices and sensors with limited electronic resources, such as implanted medical devices, machine controllers and construction stress sensors.
The process for evaluating and selecting potential algorithms took NIST several years. In addition to security, other selection criteria included performance and flexibility with regards to speed, size and energy use.
For more information:
- “NIST Selects ‘Lightweight Cryptography’ Algorithms to Protect Small Devices” (NIST)
- “NIST Selects Lightweight Crypto Algorithms for IoT Data” (Network Computing)
- “IoT trends to keep an eye on in 2023 and beyond” (TechTarget)
- “NIST chooses encryption algorithms for lightweight IoT devices” (Help Net Security)
VIDEOS
Common IoT Cyber Attacks Explained (RealTime Cyber)
The Future of IoT Security (TechTarget)
4 - Reduce cyber risk with supply chain mapping
The U.K. National Cyber Security Centre (NCSC) just released guidance on the practice of supply chain mapping, which is the process of methodically and consistently collecting information about your suppliers to reduce cyber risk.

With a comprehensive understanding of their supplier network, organizations can better assess the cyber risks involved and take proactive steps to mitigate them.
Here’s how to get started creating a supply chain map:
- Use existing data stores, such as procurement systems, to list all known suppliers, prioritizing the most critical to your organization
- Decide what information to capture about your supply chain
- Determine how to do the supply chain information securely and how to manage access to it
- Decide whether or not to collect information about your suppliers’ subcontractors
To get all the details, check out the NCSC’s announcement of its supply chain mapping guide and the guide itself.
For more information about supply chain cybersecurity:
- “What is supply chain security?” (TechTarget)
- “Best practices for boosting supply chain security” (ComputerWeekly)
- “When Securing Your Software Supply Chain, Don't Forget the Cloud” (ITPro Today)
- “Software Supply Chain Security Guidance” (National Institute of Standards and Technology)
VIDEOS
Cyber Supply Chain: Risk Management for State, Local, Tribal, and Territorial Governments (CISA)
Securing and Enhancing the ICT Supply Chain (CISA)
5 - Report: Top cyber risks for U.S. in 2023
Geopolitical unrest. Skills shortage. Economic headwinds. Vulnerable infrastructure. These are some of the top cybersecurity risks threatening the U.S. this year, according to the Bipartisan Policy Center, a Washington, D.C. think tank that promotes bipartisan ideas to improve Americans’ health, security and opportunities.
In its report “Top Risks in Cybersecurity 2023”, the group details eight cyber risks that public- and private-sector organizations in the U.S. should monitor closely and prepare for.

Here’s a quick look at four of the risks:
- Evolving geopolitical environment, such as the Russia-Ukraine war, which lowers inhibitions for cyberattacks, including against critical infrastructure
- Accelerating cyber arms race between attackers and defenders
- Global economic headwinds, which hurts revenue and consequently slows down organizations’ investments in technology, making them more vulnerable
- Overlapping, conflicting and subjective regulations at the national, state and local levels, which makes it complex and costly for organizations to comply
In addition to members of the Bipartisan Policy Center, report contributors included current and former CISOs, CSOs, attorneys general and government officials.
For more information about current global cyber risks:
- “Cyber arms race, economic headwinds among top macro cybersecurity risks for 2023” (CSO Online)
- “World Economic Forum Names Cybercrime and Cyber Insecurity Among Top 10 Global Risks for 2023” (Tenable)
- “Allianz Risk Barometer 2023 - Rank 1: Cyber incidents” (Allianz)
- “2023 Global Future of Cyber Survey” (Deloitte)
- “Six Predictions from Tenable for 2023” (Tenable)
6 - Revisiting CSA’s top SaaS governance best practices
The Cloud Security Alliance is refreshing our memory on its governance best practices to secure your software-as-a-service (SaaS) environments with an article titled “10 SaaS Governance Best Practices to Protect Your Data.” It distills the essence of its much more detailed “SaaS Governance Best Practices for Cloud Customers” white paper, which is definitely worth a read if you’re tasked with ensuring your SaaS applications are secure and compliant.

In the meantime, here are the 10 best practices at a quick glance:
- Define information security policies that you apply while evaluating, adopting, using and terminating SaaS products
- Clarify your security roles and responsibilities as a customer and those of the cloud service provider
- Inventory your SaaS data assets, identifying their users, ownership and acceptable use
- Establish access control to your SaaS applications with identity and access management controls
- Ensure your data is encrypted as it’s transmitted to or from the SaaS provider, whether you’re managing the encryption keys or relying on the vendor to do so
- Implement operations security, including malware protection, data backup, event logging and monitoring, and vulnerability management.
- Ensure network security controls are in place both on your end and on the cloud provider’s end
- Identify the SaaS products’ components and develop risk management policies for them
- Craft an incident management response plan
- Ensure your SaaS applications are in compliance with data regulations that apply to your organization
For more information about SaaS security, check out these articles:
- “SaaS and Third-Party Risk: Is Your Organization Asking the Hard Questions?” (DarkReading)
- “Cloud Security: 3 Things InfoSec Leaders Need to Know About the Shared Responsibility Model” (Tenable)
- “Best practices for negotiating a SaaS SLA” (TechTarget)
- “A 10-point plan to vet SaaS provider security” (CSO Magazine)
- “Cloud Security Basics: Protecting Your Web Applications” (Tenable)
- Cloud
- Cybersecurity Snapshot
- Executive Management
- NIST


