Cybersecurity Snapshot: CISOs Are Happier, but Dev Teams Still Lack Secure Coding Skills

Learn all about the spike in CISO job satisfaction. Plus, NIST mulls major makeover of its Cybersecurity Framework. Also, the struggle to develop secure apps is real. Then check out how Uncle Sam plans to use AI and ML to boost cybersecurity. And much more!
Dive into six things that are top of mind for the week ending Jan. 20.
1 - CISO job satisfaction hits 3-year high
Don’t count CISOs among those who can’t get no satisfaction.
A survey of 520 CISOs found that job satisfaction grew in 2022, with 74% of respondents feeling “somewhat” or “very” satisfied, up from 69% in 2021 and from 45% in 2020.
The “2022 State of the CISO Report” from IANS Research and Artico Search also found that, despite the boost in job satisfaction, 44% are mulling changing jobs “in the near future.”
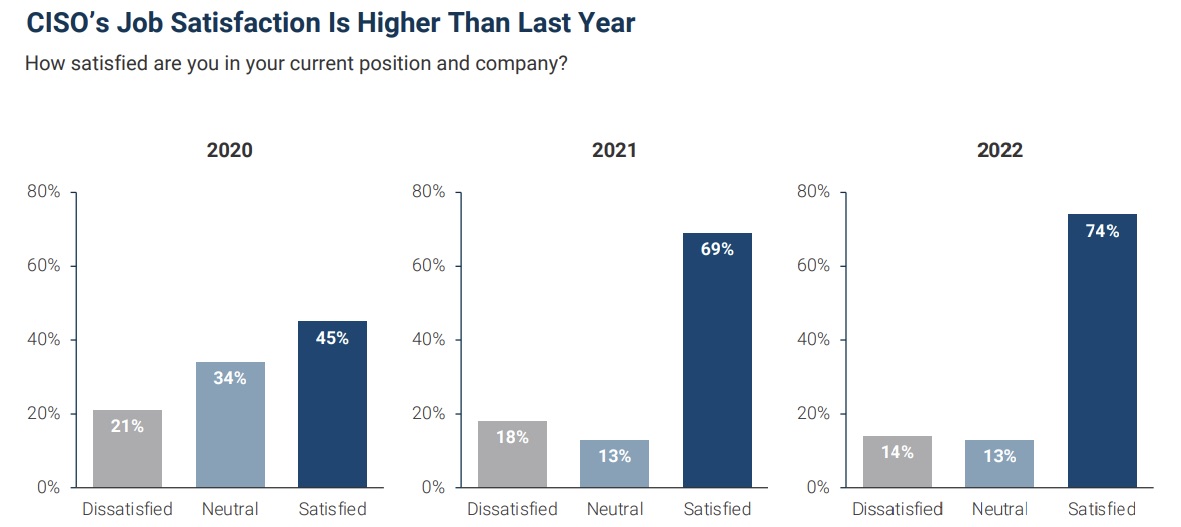
(Source: “2022 State of the CISO Report” from IANS Research and Artico Search, January 2023)
So what are the pillars of CISO job satisfaction?
- Compensation
- Security budget
- Career development
- Executive visibility
- Organizational support
Among these 5 elements, the ones with the lowest satisfaction scores were the ones most closely linked to money: budget and compensation.
“There is still a cohort of CISOs whose businesses haven’t fully woken up to the criticality of security and, consequently, aren’t yet caught up to market-level compensation and budgetary levels, leaving their CISOs less satisfied,” Artico Search Founder Steve Martano said in a blog.
For more information about how to retain CISOs and other top cybersecurity pros:
- “Are CISOs happy?” (CareerExplorer)
- “When to quit your CISO job?” (Identity Management Institute)
- “5 trust-building tips from a risk-minded CISO” (Security Magazine)
- “Tips for developing cybersecurity leadership talent” (TechTarget)
- “When CISOs are doomed to fail” (CSO Online)
2 - Insecure software continues flowing out of many dev pipelines
The continuous release of unsafe software riddled with vulnerabilities, misconfigurations and other security flaws is a critical problem, caused in large part by widespread ignorance among developers about secure coding.
This week we got another reminder about this issue from research firm Enterprise Management Associates (EMA), which just released a report titled "Secure Coding Practices - Growing Success or Zero-Day Epidemic?"
After surveying 129 software developers, EMA found that a majority are struggling to develop secure software, and are thus consistently rolling out unsafe applications that offer plenty of low-hanging fruit for attackers.

Here are key findings from the report:
- Over half of surveyed organizations haven’t fully integrated security into their software development lifecycle (SDLC).
- Almost 70% of organizations' SDLCs are missing critical security processes.
- Only 25% are adopting a “shift-left” strategy to embed security earlier into the development process.
A key recommendation from the report: Organizations should provide security training for their developers, most of whom receive little to no instruction on secure coding while in school.
For more information about secure software development:
- “OWASP Secure Coding Practices-Quick Reference Guide” (OWASP)
- “The ‘S’ Word: How Frontend Developers Can Embrace Security” (The New Stack)
- “A Practical Approach for Shifting Left” (Tenable)
- “Top 4 best practices to secure the SDLC” (TechTarget)
- “Best Practices for Secure Coding” (University of Michigan)
VIDEOS
Secure Software Development Framework: An Industry and Public Sector Approach (RSA Conference)
New Guidelines for Enhancing Software Supply Chain Security Under EO 14028 (RSA Conference)
3 - CISA updates MITRE ATT&CK framework mapping
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has revised its “Best Practices for MITRE ATT&CK Mapping” guide, adding information about new platforms, expanding coverage of Linux and macOS, and redefining data sources and detections.
The guide, first published in mid-2021, now also establishes more parity between the matrices for industrial control systems, mobile and enterprise, and addresses analytical biases and mapping mistakes.
![]()
So whether you’ve been using it already or haven’t gotten around to checking it out, now’s a good time to take a look at CISA’s “Best Practices for MITRE ATT&CK Mapping.” The guide aims to help security analysts map adversary behavior to the framework, which is a knowledge base of attacker tactics and techniques.
Through “clear guidance and examples,” the guide shows network defenders how to use the MITRE ATT&CK framework in “both analysis of raw data and finished reporting more fully,” CISA said in a blog post announcing the guide in June 2021.
For more information:
- MITRE ATT&CK main page
- “What is the MITRE ATT&CK framework?” (TechTarget)
- “The changing role of the MITRE ATT&CK framework” (CSO Online)
- “How the MITRE Engenuity ATT&CK evaluations work” (SC Magazine)
- “MITRE ATT&CK framework: Understanding attack methods” (CSO Online)
VIDEOS
MITRE ATT&CK Framework (MITRE)
What is Threat-Informed Defense? (MITRE)
MITRE ATT&CK: Benefits and Challenges (TechTarget)
4 - Business and cyber leaders still struggle to communicate
What we've got here is failure to communicate.
According to the World Economic Forum’s “Global Cybersecurity Outlook 2023” report, security leaders must do a better job explaining to their business peers the cyberthreats faced by their organizations, because unclear communications hampers efforts to reduce cyber risk.
While business executives are more aware now than a year ago of the importance of addressing cyberthreats, cybersecurity leaders “still struggle” to articulate the impact of cyber risks using “language that their business counterparts fully understand and can act upon,” the report reads.

Specifically, cybersecurity leaders use language that’s too technical and jargony, and dispense too much data and not enough strategic insights, according to the report.
Recommendations for further bridging this communications gap include:
- Adopt a “common language” that represents cybersecurity data using metrics that can be understood by and matter to business leaders, board members and other non-technical parties.
- Implement organizational changes to “embed” discussions about cyber risks across the business and make these conversations more fluid and effective.
- Make business leaders accountable for establishing operational cyber requirements and priorities that strengthen their organizations’ cybersecurity.
Other findings from the report, based on a survey of 151 global business and cyber leaders:
- 43% of respondents deem it likely that a cyberattack will materially affect their own organization within the next two years.
- Respondents ranked business continuity (67%) and reputational damage (65%) as their top two cyber-risk concerns.
- A large majority of cyber leaders (93%) and business leaders (86%) believe it’s either “moderately” or “very” likely that a “catastrophic” cyber incident will occur in the next two years due to global geopolitical instability.
How likely is it that geopolitical instability will lead to a far-reaching, catastrophic cyber event in the next two years?
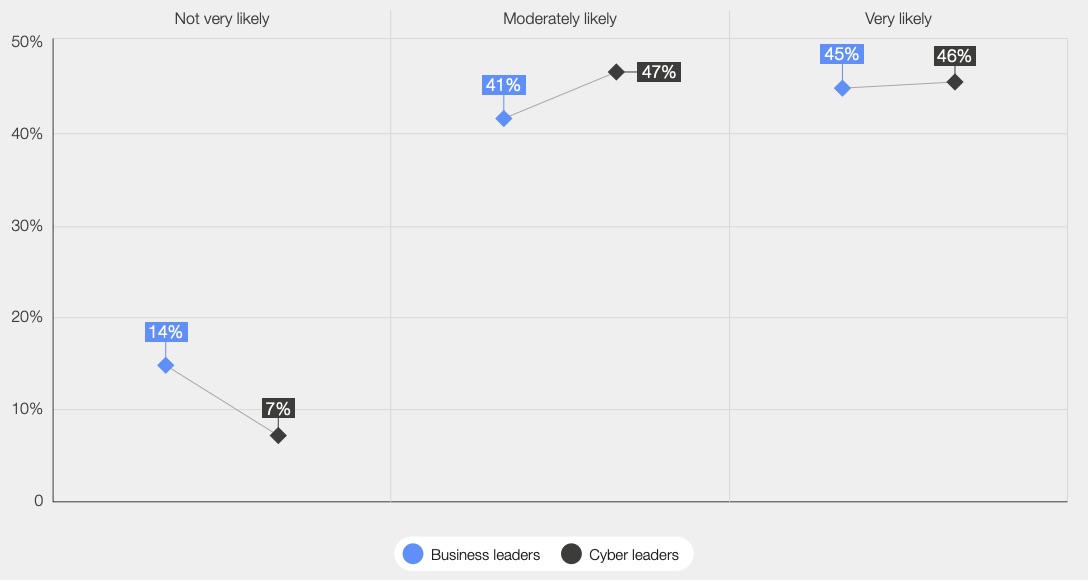
(Source: World Economic Forum’s “Global Cybersecurity Outlook 2023” report, January 2023)
For more information, check out the full report, highlights, commentary, recommendations and press conference from the World Economic Forum, as well as coverage from Modern Diplomacy, ComputerWeekly, Help Net Security and Infosecurity Magazine.
5 - CISA and DHS to tackle new cyberthreats with AI and ML
The U.S. government plans to develop a next-generation cybersecurity platform designed to more quickly and effectively analyze and defuse evolving cyberattacks via the use of artificial intelligence (AI) and machine learning (ML).
The project, called the CISA Advanced Analytics Platform for Machine Learning (CAP-M), will be carried out by CISA and the U.S. Department of Homeland Security (DHS).

A version of the project, then known as CyLab, was first unveiled in 2021. When completed, CAP-M is expected to allow CISA users to better prepare for and respond to threats by:
- Analyzing cyber data using advanced techniques
- Addressing use cases and carrying out experiments that are currently out of reach
The plan includes the creation of a multi-cloud sandbox environment where CISA users will train and work on experiments, as well as conduct research on data analysis methods and tools with AI and ML capabilities.
“Although threats and hazards continue to evolve, CAP-M will provide CISA with the capabilities to continually innovate to prepare for and respond to them,” reads a project description published this month.
Lessons from CAP-M will be shared with other government agencies, academia and the private sector.
For more information:
- “CISA, DHS S&T Directorate to Develop Analytics Ecosystem for Cybersecurity” (ExectiveGov)
- “The US government is building an AI sandbox to tackle cybercrime” (TechRadar)
- “DHS and CISA Get Into the ML Cyber Security Sandbox Game” (Cybersecurity Connect)
- “Homeland Security, CISA builds AI-based cybersecurity analytics sandbox (The Register)
CyLab: Advanced Analytics Environments to Protect Critical Infrastructure (CISA)
6 - NIST mulling bigger changes to its cybersecurity framework
The National Institute of Standards and Technology (NIST), which is in the process of updating its NIST Cybersecurity Framework (CSF), published this week the “CSF 2.0 Concept Paper,” outlining areas where it might make major changes to the framework, based on input it has received.
If your organization, like so many others, uses the CSF to help anchor and inform your cybersecurity processes and strategy, you might want to give this paper a read and send NIST any thoughts, questions and suggestions you may have. You have until March 3rd to submit your feedback.
For more information, check out coverage from CSO Online and NextGov, as well as these NIST resources:
- NIST Cybersecurity Framework 2.0 fact sheet
- “Updating the NIST Cybersecurity Framework – Journey To CSF 2.0”
- “NIST Seeks Input to Update Cybersecurity Framework”
VIDEOS
Journey to the NIST Cybersecurity Framework (CSF) 2.0 | Workshop #1
Treasury Outreach Event on NIST Cybersecurity Framework 2.0
- Cybersecurity Snapshot
- DevOps
- Exposure Management
- NIST
