Cisco Issues Patches for 4 Critical Vulnerabilities in Cisco Policy Suite

Cisco’s Policy Suite for Mobile controls billing and access control for customer devices. Root access to this suite is concerning because of the breadth of user device access.
The latest batch of Cisco patches includes fixes for four critical vulnerabilities related to unauthenticated access and default credentials in the Cisco Policy Suite for the Cisco Mobility Services Engine. All four were discovered by internal security testing. In addition, nine high-severity vulnerabilities and 12 medium ones were patched in a variety of other Cisco platforms.
Analysis
Two of the vulnerabilities (CVE-2018-0376 and CVE-2018-0374) give unauthenticated access to the Policy Builder database and interface, respectively, allowing for unauthorized changes to take place. CVE-2018-0377 affects the Open Systems Gateway initiative (OSGi) interface of the Policy Builder Suite and allows the remote attacker to access or change any files that are accessible by the OSGi process. The last critical patch (CVE-2018-0375) involves default credentials in the Cluster Manager of the Suite giving the attacker remote root access.
These Cisco vulnerabilities received a CVSS v3.0 score of 9.8 out of 10, indicating a "critical" degree of severity.
Cisco’s Policy Suite for Mobile controls billing and access control for customer devices. According to Cisco’s configuration documentation, the policy suite controls mobile user configuration and active session tracking. Root access to this suite is concerning because of the breadth of user device access.
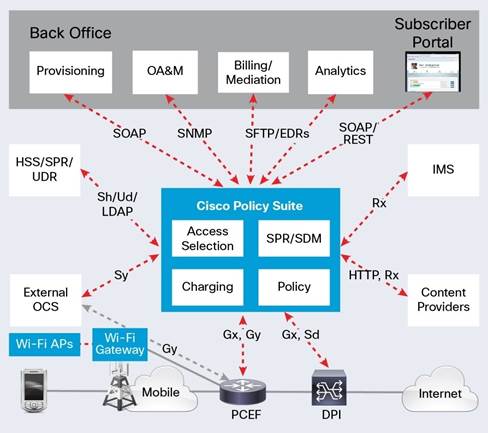
Below is a visualization of the scope of mobile elements that this software interacts with.
Solution
The OSGi interface unauthenticated access vulnerability (CVE-2018-0377) affects Cisco Policy Suite releases prior to Release 18.1.0 and is fixed in Cisco Policy Suite Release 18.1.0.
The Cisco Policy Suite Policy Builder Unauthenticated Access Vulnerability (CVE-2018-0376), Cisco Policy Suite Policy Builder Database Unauthenticated Access Vulnerability (CVE-2018-0374) and Cisco Policy Suite Cluster Manager Default Password Vulnerability (CVE-2018-0375) affect releases prior to 18.2.0 and are fixed in Cisco Policy Suite Release 18.2.0. CVE-2018-0375 contains a workaround script (change_passwd.sh) that can be used to update the existing default password.
Additional Information
Critical Cisco Security Advisories:
- OSGi interface unauthenticated access vulnerability (CVE-2018-0377)
- Cisco Policy Suite Policy Builder Database Unauthenticated Access Vulnerability (CVE-2018-0374)
- Cisco Policy Suite Cluster Manager Default Password Vulnerability (CVE-2018-0375)
- Cisco Policy Suite Policy Builder Unauthenticated Access Vulnerability (CVE-2018-0376)
Learn more about Tenable.io,® the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
- Announcements


