Can Mr. Robot Attack your Data Center?

In the Mr. Robot Season 2 finale, we finally learn about phase 2 of the hack. Spoiler Alert: The hack is to overwrite firmware and cause a battery room in a data center to explode. The key to this hack’s success is twofold: 1) all the paper records must be in the same building as the data center that is being attacked, and 2) the attacker must have some sort of physical access to the network and have the skills to hack the firmware of the UPS systems in the battery room. I would like to discuss some of the possible defenses that security operations can use to help defend against such an attack.
Know what’s on your network
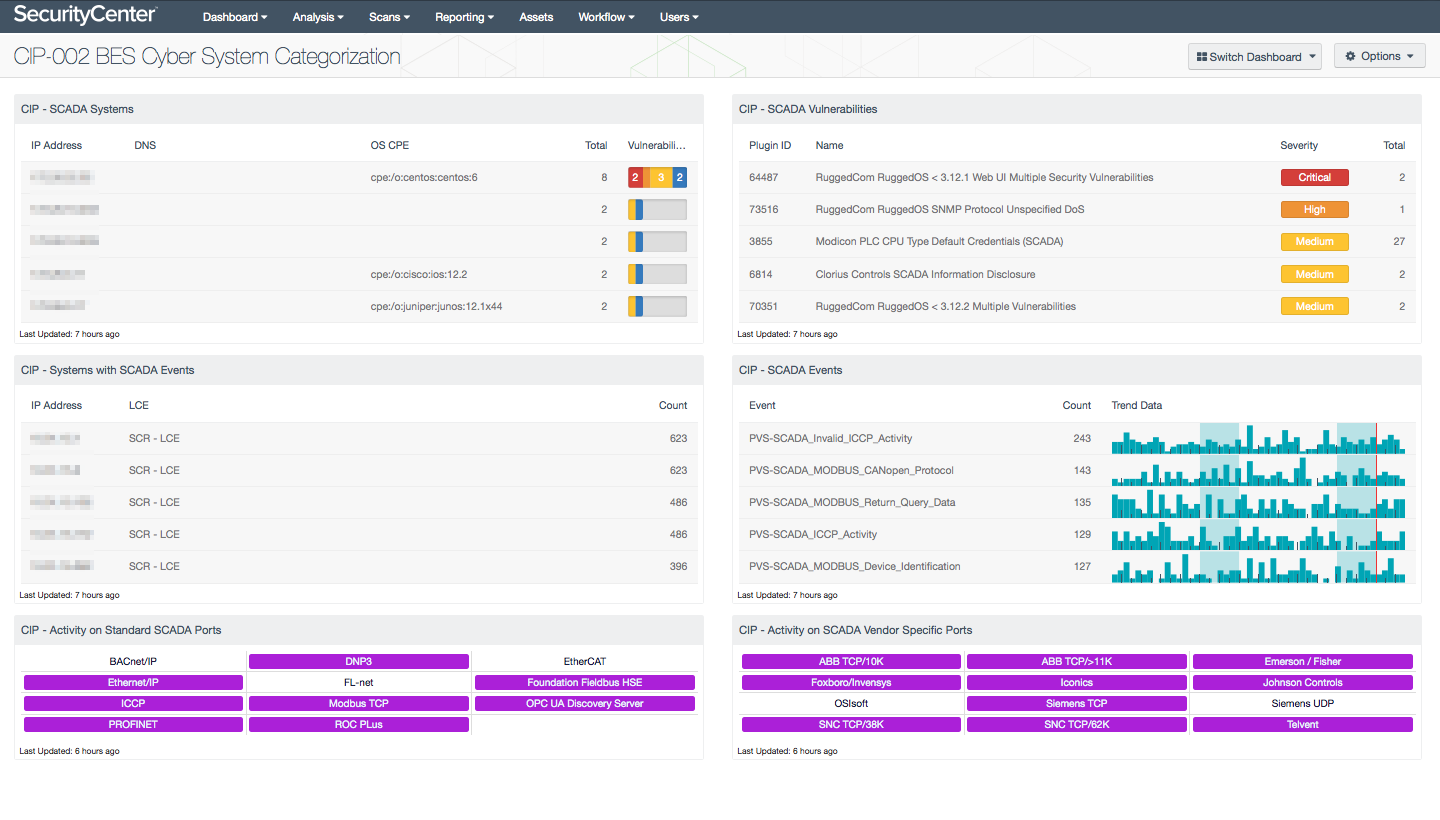
The North American Electric Reliability Corporation (NERC) is committed to protecting the bulk power system against cybersecurity compromises that could lead to misoperation or instability. The NERC Critical Infrastructure Protection (CIP) Standards provide a cybersecurity framework for the identification and protection of Bulk Electric System (BES) Cyber Systems, to support the reliable operation of the North American power grid. CIP contains nine mandatory standards; CIP-002 is BES Cyber System Categorization. The purpose of CIP-002 is "to identify and categorize BES Cyber Systems and their associated BES Cyber Assets for the application of cyber security requirements commensurate with the adverse impact that loss, compromise, or misuse of those BES Cyber Systems could have on the reliable operation of the BES."
Often the Supervisory Control and Data Acquisition (SCADA) systems or Industrial Control Systems (ICS) are closed and proprietary operating systems and are subject to what may appear to be tightly controlled update processes. As James Arien discussed in a talk at DEF CON 18, the full understanding of SCADA is extremely complex and has many safety systems in place. In some cases, hacking a Programmable Logic Controller (PLC) or supporting Operational Technology (OT equipment such as a phasor measurement unit) is possible; however, the full implementation of a hack such as the Mr. Robot hack requires intimate knowledge of the specific SCADA system used, which leads back to insider threats. Other problems that exist are related to inter-organizational politics. As with any business and computing environment, as clearly portrayed in the Mr Robot series, security controls happen at many levels. The most important first step is to know what systems are on the network and who is accessing the systems.
Detecting the hack
As I have discussed in previous Mr. Robot posts, it is critical to understand when new devices connect to the network. For this discussion, I want to focus on network segmentation, and the detection of devices on critical subnets and areas within the network. As data centers are designed, there is often a management network created. These management networks are often different for each type of management. For example the facilities management (aka HVAC, UPS, etc.) and network management (switches, routers, and etc.) would be on separate subnets. In a well-designed and segmented network, there are different Access Control Lists (ACL) placed on network interfaces, thus limiting access where required. SCADA and ICS networks should be treated in this manner and segmented from the rest of the network using the same ACL to restrict access. If the network is properly segmented, alerts can be created to detect when a non-approved device is connected to a restricted managment network.
By deploying the Passive Vulnerability Scanner® (PVS™) and Nessus® in these subnets, the organization can detect new systems actively and passively. The CIP-002 BES Cyber System Categorization dashboard provides security operations with an easier method to identify systems with access. With more customization, the dashboard can also be configured to report on new systems that come online. Detecting and monitoring UPS systems is also critical, and if done so correctly, E-Corp might not be in the danger they are in this season.
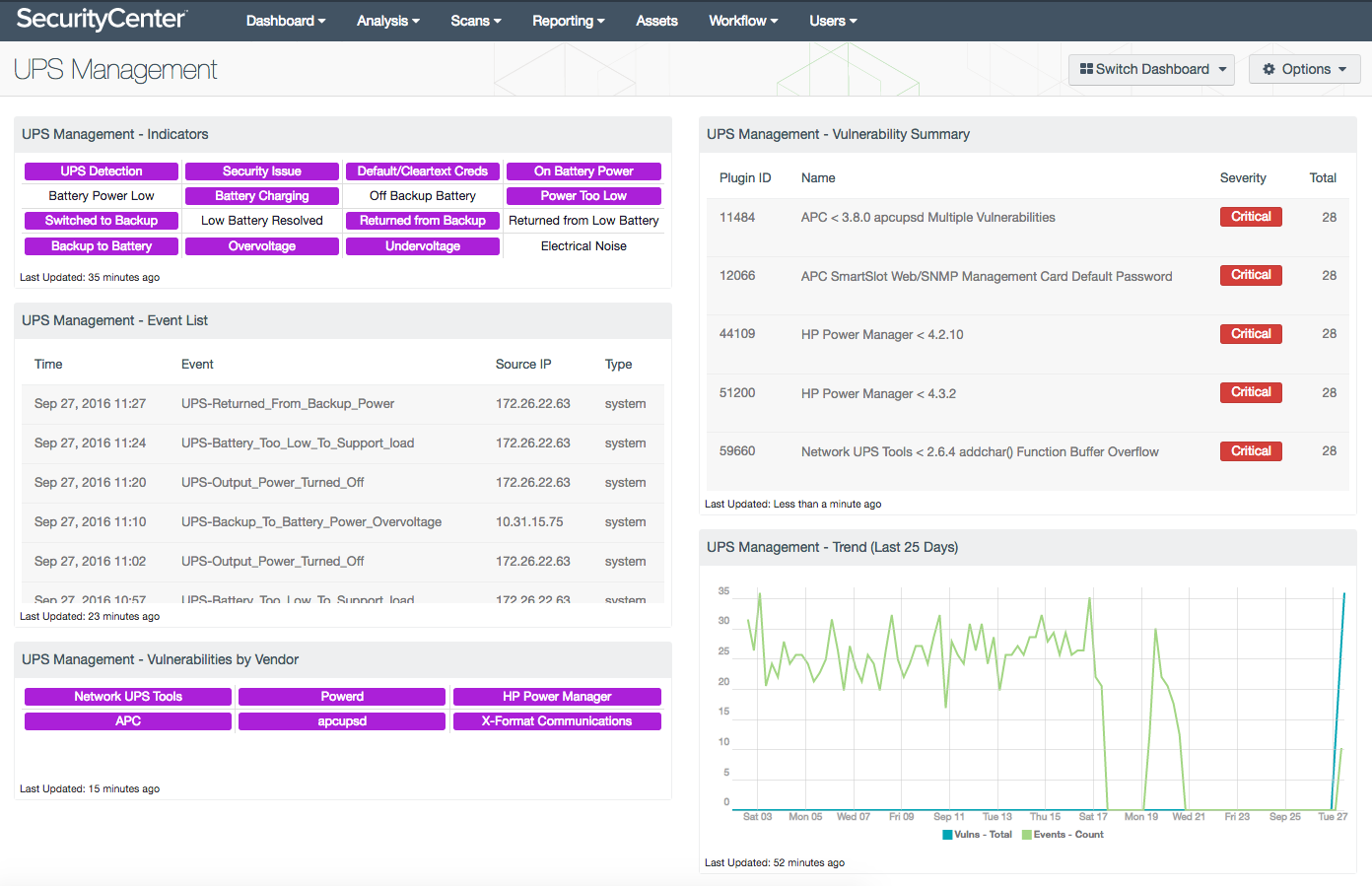
The UPS Management dashboard provides insight into vulnerabilities and events associated with UPS systems. As part of an organization’s critical infrastructure, failures in the security or functionality of UPS systems could lead to exploitation or data loss. Events related to UPS systems are tracked to enable security teams to monitor UPS functionality. Vulnerabilities related to UPS systems and applications are also identified in order to facilitate effective remediation measures. By monitoring UPS systems and applications for events and vulnerabilities, security teams can more effectively ensure the functionality and security of these systems.
The key to this week’s hack is the uploading of new software to UPS equipment. When organizations update firmware on PLCs, OT related equipment, and even UPS systems, these systems can use a protocol called Trivial File Transfer Protocol (TFTP). As implementations of SCADA can vary, the update mechanisms can also use Modbus, EtherNet/IP, SSH, or even some form of http(s) transport. Understanding how firmware updates are securely deployed is key to preventing such an attack and is paramount to good security.
Without appropriate transport and integrity checking of critical processes like firmware updating, attackers can perform and successfully carry out man-in-the-middle attacks during this process. Organizations with PVS and Nessus have the capability to detect the OS version of systems, and alerts can be created if a system’s OS is changed. The Tenable Log Correlation Engine® (LCE®) can also detect when software updates are detected and related events. In many environments, firmware updates are performed from very specific workstations in an organization. Analysts using SecurityCenter Continuous View® can be alerted when PLCs and other OT equipment have firmware updates, and verify these updates are performed from authorized locations in the network.
Reality or Hollywood?
The risk in this hack is not really blowing up the data center; the important question is can a malicious hacker get unauthorized changes and backdoors onto your systems. The answer is a resounding yes! There are many ways this attack can occur, but we as security professionals can prevent this type of attack by knowing what is on the network, and by using proper segmentation, such as the Purdue Model. Continuous monitoring is key to preventing this attack; scanning once a month is not good enough. Scanning once a week is not good enough; you must scan daily, sniff continuously, and correlate logs effortlessly. SecurityCenter Continuous View is the only solution that provides integrated methods to do all three detection methods.
- Dashboards
- SCADA
- SecurityCenter