Verizon’s Data Breach Report – Insights for Cloud Security Professionals

Select highlights from Verizon’s recent Data Breach Investigations Report that may interest cloud security professionals — and suggested actions to take.
For the past 14 years, telecommunications services provider Verizon has published an annual report that analyzes the security incidents and data breaches of the previous year. The Verizon Data Breach Investigations Report (DBIR) presents findings by attack type, industry, vulnerability and more, and provides insights into global changes taking place in the cybersecurity sphere.
For its 2021 report, Verizon analyzed 29,207 real-world security incidents, which the telco provider defines as “a security event that compromises the integrity, confidentiality or availability of an information asset.” Of those incidents, 5,258 were confirmed breaches, which Verizon defines as “an incident that results in the confirmed disclosure — not just potential exposure — of data to an unauthorized party.” The report was created in cooperation with 83 organizations.
We summarize here the key findings that may be of most interest to cloud security professionals. There’s lots of information, so let’s dive right in!
Key findings for cloud security professionals to note
The causes of data breaches
Data breaches, the holy grail of cyberattackers and source of nightmares for security teams, are the “confirmed disclosure of data… to an unauthorized party.” Out of 5,275 data breaches Verizon analyzed, approximately:
- 30% occurred due to social engineering
- 25% were caused by web application attacks
- 20% resulted from system intrusion
- 15% resulted from miscellaneous errors
The remaining 10% of data breaches were caused by privilege misuse, lost and stolen assets, denial of service and more.
The target: Humans
Interestingly, 85% of the breaches involved a human element and 61% involved credentials. In short, we are all vulnerable, and attackers attempt to exploit that vulnerability to progress laterally in an organization’s network. The attempt to gain access to a system so as to leverage the victim’s access was the second top motive for attacks.
Verizon cautions, “if you are a software developer or service provider that has assets that could be repurposed in that manner, please make sure you are paying the proper attention to the operational parts of your organization.”
Cloud asset attacks are gaining popularity
When it comes to attacked assets, Verizon found that “external cloud assets were more common than on premises assets in both incidents and breaches.” What does this mean for cloud security teams? According to Verizon, “cloud assets deserve a seat at the grown-up security table and a piece of your budget pie,” since “in a sample of random organizations, 17% that had a web presence had internet-facing cloud assets.” In other words, malicious actors are trying to take advantage of the natural obfuscation surrounding cloud assets, in which security stakeholders lack the needed visibility and context to understand access and network exposure.
Incident classification patterns and who they affected
The DBIR report analyzed a sizable 29,207 incidents and classified them by type of vulnerability or attack. Here are the main cloud security threats incidents that can impact an organization’s public cloud, as well as a short recommendation for how a cloud security solution might help.
Miscellaneous (human) errors
Miscellaneous errors are, according to Verizon, “incidents where unintentional actions directly compromised a security attribute of an information asset. This does not include lost devices, which is grouped with theft instead.” Such mistakes are common and often happen at scale. These include “misconfiguration of database assets being found by security researchers,” which is considered “a growing problem.”
Verizon identified and analyzed 919 incidents, 896 with confirmed data disclosure. Of these incidents, 79% of the data compromised was personal, 17% was medical, 13% was bank-related and 13% was credentials.
The figure below shows the breakdown for internal actors, which are 99% of the actors who cause these incidents:
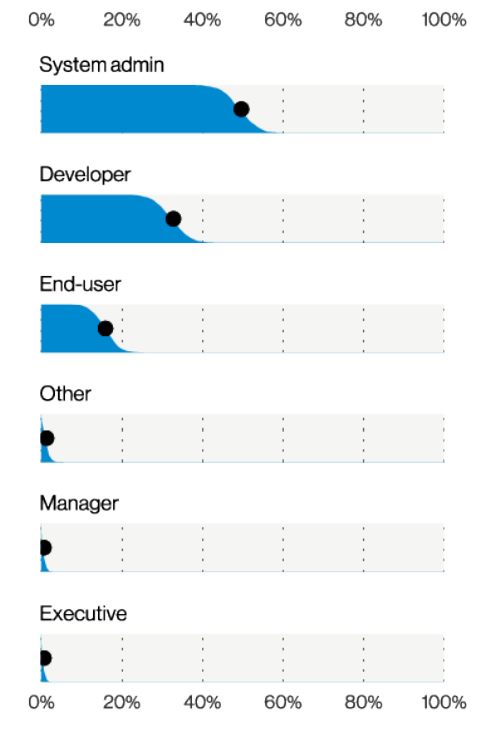
Internal actor varieties in Miscellaneous Errors breaches (n=157), Verizon 2021 Data Breach Investigations Report
The results show that system administrators are the cause of approximately 50% of breaches caused by miscellaneous errors, and developers are the cause of approximately 30%. This is “relatively intuitive since both system administrators and developers typically have privileged access to data on the systems they maintain.” However, as Verizon notes: “the adage of ‘to whom much is given, much is expected’ assuredly applies here. When people in these roles do make mistakes, the scope is often of much greater significance than the foibles of an average end-user.”
When looking at the types of errors most common in miscellaneous errors breaches, misconfigurations (~50%) and misdeliveries (~30%) reign (see below), a distribution that correlates with the internal actors graph above. “Given the pairing of sys admins and developers with the Misconfiguration action varieties, you can imagine that this combination can wreak havoc on the confidentiality of an organization’s data, or that of their customers’ or employees’,” says Verizon.

Top error varieties in Miscellaneous Errors breaches (n=609), Verizon 2021 Data Breach Investigations Report
Another pair of correlating results Verizon “frequently observe(s)” can be seen when looking at who usually discovers breaches and the types of assets breached, as shown here:
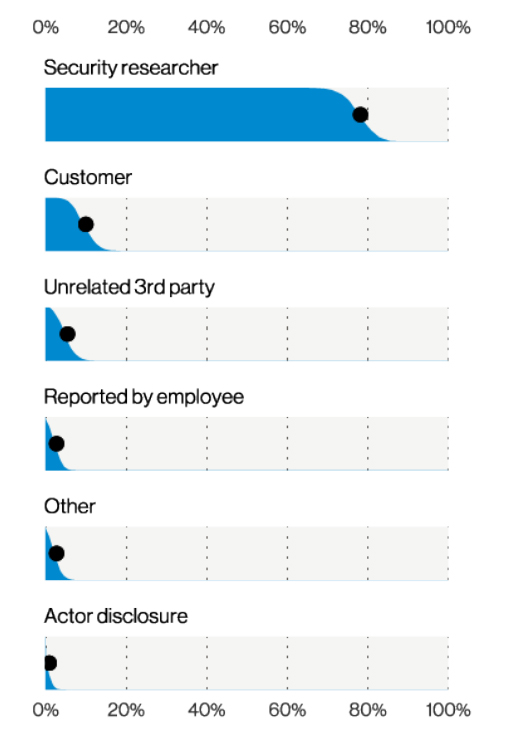
Discover method varieties in Miscellaneous Errors breaches (n=110), Verizon 2021 Data Breach Investigations Report
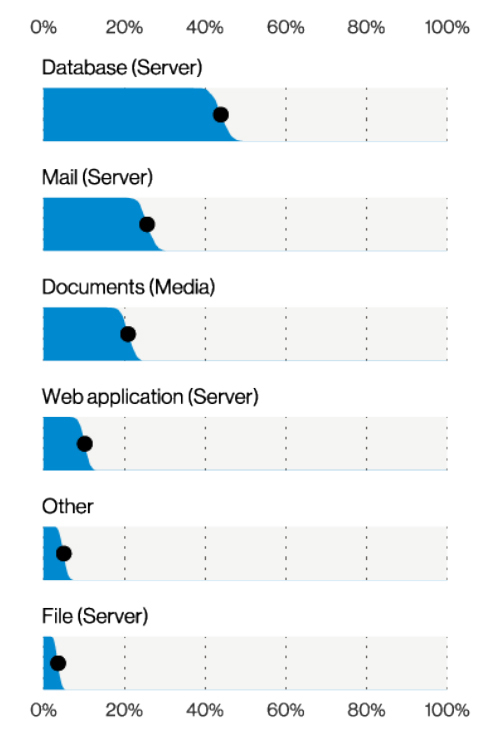
Top asset varieties in Miscellaneous Errors Breaches (n=635), Verizon 2021 Data Breach Investigations Report
According to Verizon, “we frequently observe data stores (such as relational or document databases, or cloud-based file storage) being placed onto the internet with no controls, combined with the security researchers who search for them. These rather undesirable combinations have been on the rise for the past few years.”
How a cloud security solution can help prevent miscellaneous errors
A cloud security solution that helps identify misconfigurations and excessive and otherwise risky user permissions can identify and help mitigate vulnerabilities before a data breach occurs and/or attackers find them. Also, since humans are not immune to making mistakes, such a solution can also automate monitoring of activities to detect anomalies and odd behavioral patterns to identify when an account is at risk of compromise. This kind of actionable intelligence is especially important when it comes to system admins and developers, who typically have extensive permissions to access and change cloud computing components. Some kind of continuous oversight is needed to address the reality of human error.
Privilege misuse
Privileged misuse is “incidents predominantly driven by unapproved or malicious use of legitimate privileges.” Verizon identified 265 such incidents, 222 with confirmed data disclosure. Of the breaches, 99% were caused by internal actors (i.e, employees and not external attackers).
Approximately 70% of privilege misuse instances were caused by privilege abuse. Most of the information stolen was personal. Surprisingly, “the rise in remote workers did not appear to have a noticeable effect on Misuse.”
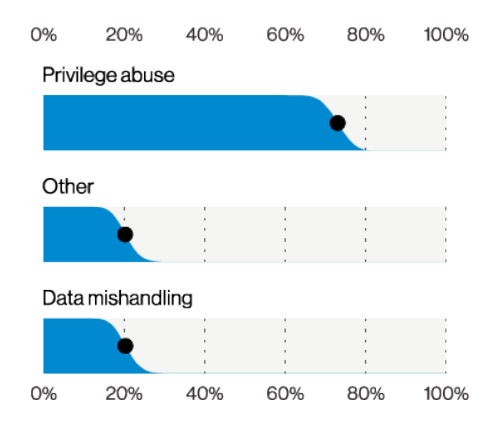
Top misuse varieties in Privilege Misuse breaches (n=175), Verizon 2021 Data Breach Investigations Report
Verizon found out that quite a few cases of privilege misuse took years to identify, since “most organizations have tailored their controls primarily to find people trying to get in from the outside. But “for organizations that have especially sensitive data, such as Healthcare, along with regulatory requirements that make reporting mandatory, it showcases the need for detective controls that can quickly catch this kind of misuse.”
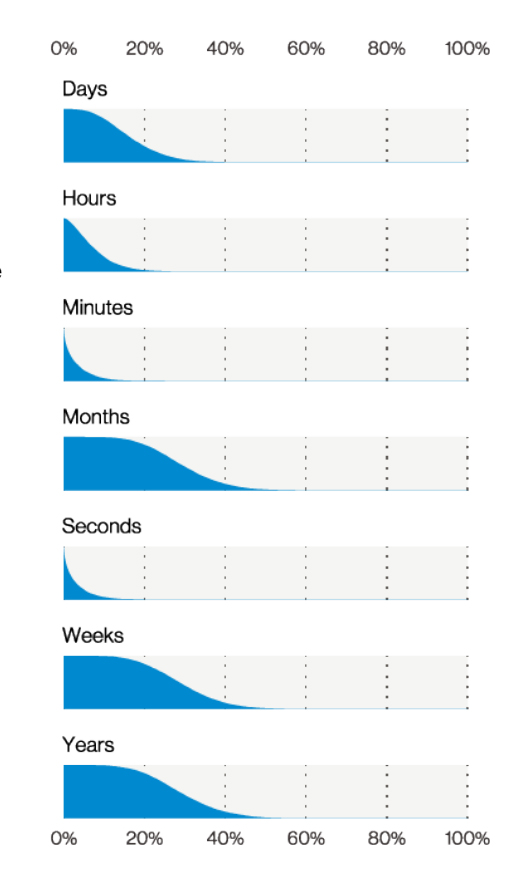
Discovery timeline in Privilege Misuse breaches (n=22), Verizon 2021 Data Breach Investigations Report
How a cloud security solution can help prevent privilege misuse
A cloud security solution can help identify privilege misuse early on: by identifying and removing excessive permissions and toxic permission combinations, and by enforcing the principle of least privilege — that is, limiting permissions to the bare minimum needed to get the job done. As a result, the ability to abuse permissions will be significantly reduced. In addition, continuous risk assessment with contextual visibility can provide the detective controls needed to make security teams aware of such incidents immediately, rather than in weeks or years. A cloud security solution that includes compliance auditing can ensure that the relevant regulatory requirements for preventing privilege misuse are covered and that mandatory reporting is provided.
Social engineering
Social engineering is “psychological compromise of a person, which alters their behavior into taking an action or breaching confidentiality.” This could include manipulation, bribery, phishing and more. Verizon found that out of the 3,841 social engineering incidents analyzed in their study, more than 80% were phishing attacks, “with cloud-based email servers being a target of choice.” The results suggest great cause for concern: 1761 of social engineering attacks were breaches with a confirmed data disclosure and the result was often a loss of credentials. Later in the report, Verizon notes that “this pattern saw those stolen credentials used in both Hacking and Malware attacks.”
It is also interesting to note that “the majority of Social Engineering incidents were discovered externally,” which means employees, systems admins, IT and security teams are not aware of the breaches.
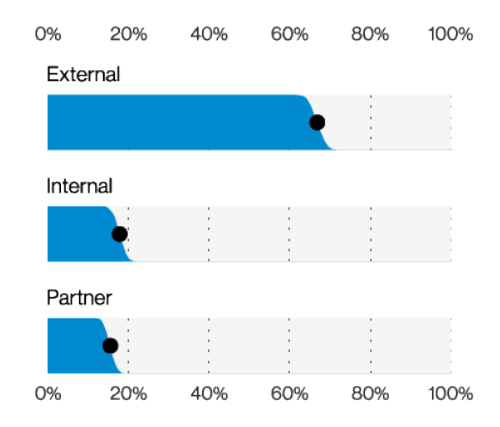
Discovery methods in Social Engineering incidents (n=691), Verizon 2021 Data Breach Investigations Report
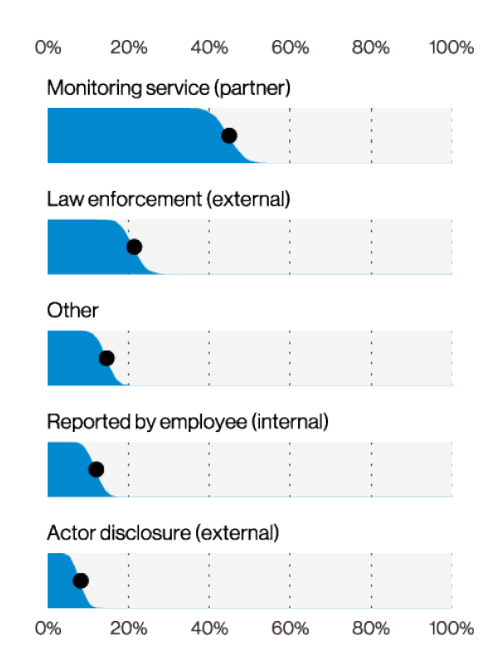
Top discovery methods varieties in Social Engineering incidents (n=234), Verizon 2021 Data Breach Investigations Report
How a cloud security solution can help prevent social engineering
If you’re human, you’re vulnerable to social engineering. A cloud security solution can prevent and contain the fallout caused by social engineering by limiting user permissions and detecting anomalies, both for internal employees and third parties. These anomalies include unusual data access, network access management, permissions management, privilege escalation and reconnaissance. By identifying them in real time or being able to track logs that relate to prior incidents, such a solution can block attackers from progressing laterally in the network and reaching critical assets.
In addition, we subscribe to Verizon’s recommendation for building an internal cybersecurity culture: “The fight against cyber breaches continues to depend on an organization’s ability to train and adapt its members’ behaviors to protect against actions such as credential theft, social engineering, and user error.” A cloud security solution can be used to educate engineering — DevOps and others — about coding risks or errors they are making. By providing contextual visibility and policy recommendations based on least privilege, such solutions can inform engineering teams, helping them understand and correct their risky coding habits and efficiently build least privilege into the infrastructure.
System intrusion
Verizon defines a system intrusion attack as one that “captures the complex attacks that leverage Malware and/or Hacking to achieve their objectives including deploying ransomware.”
Out of 3,710 incidents analyzed, 966 had confirmed data disclosure. The majority of those were malware attacks, usually ransomware. Of the data that was compromised, 33% was credentials.
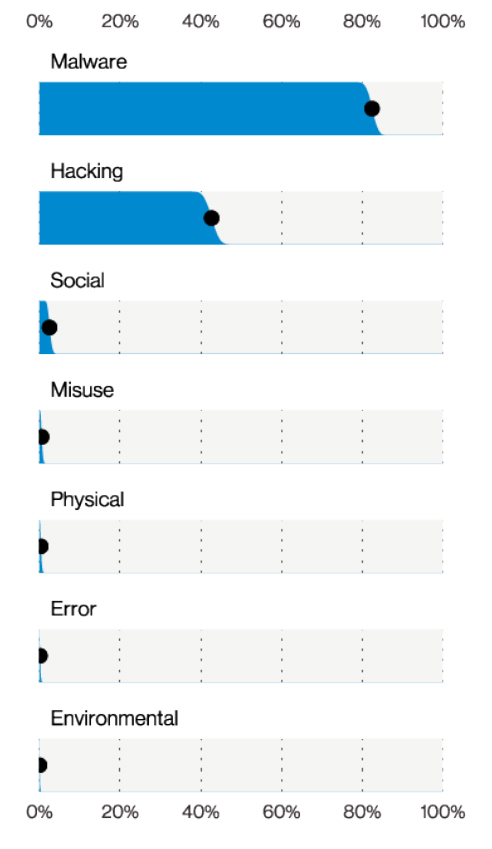
Actions in System Intrusion Breaches (n=966), Verizon 2021 Data Breach Investigations Report
Let’s shine a light on ransomware: Ransomware “has been continuing on an upward trend since 2016 and now accounts for 5% of our total incidents. The novel fact is that 10% of all breaches now involve Ransomware.” This finding aligns with “the decrease in the targeting of Payment data.” Since “attackers are less likely to purely target Payment data and are more likely to broadly target any data that will impact the victim organization’s operations. This will increase the likelihood that the organization will pay up in a Ransomware incident… the monetization through Ransomware seems to have become the preferred method, and the targeting of data will shift to reflect that.”
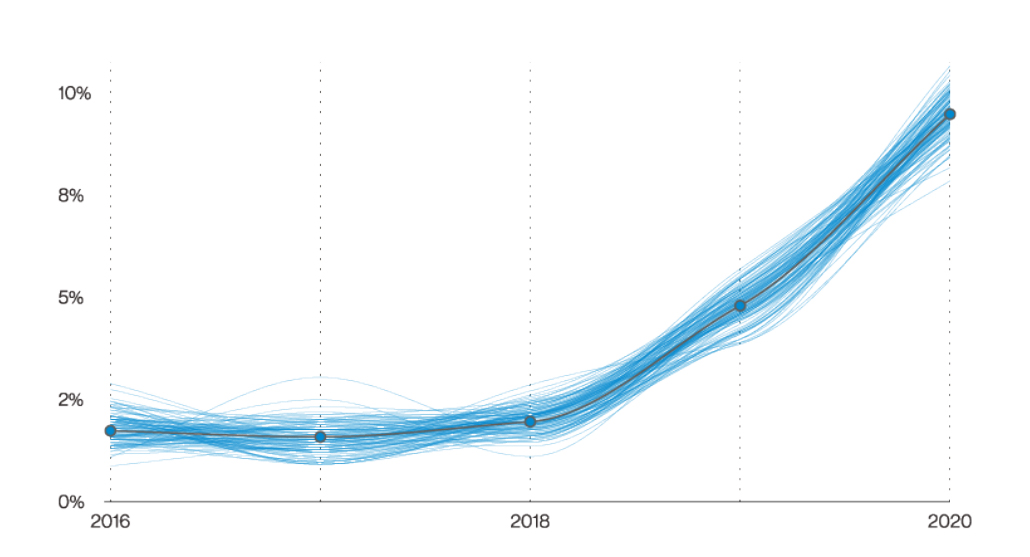
Ransomware in breaches over time, Verizon 2021 Data Breach Investigations Report
How a cloud security solution can help prevent system intrusion
A cloud security solution plays an important role in ensuring configuration security hygiene, helping reduce exposure to ransomware. In addition, by enforcing least privilege access, such a solution can prevent the impact of any existing malware that might fester and be used for stealing credentials.
Basic web application attacks
The last type of incident we will look at is basic web application attacks. Basic web application attacks are “simple web application attacks with a small number of steps/additional actions after the initial web application compromise.” They are “very focused on direct objectives, which range from getting access to email and web application data to repurposing the web app for malware distribution, defacement or future DDoS attacks.”
Verizon identified 4,862 incidents, 1,384 with confirmed data disclosure. Of the data that was compromised, 80% was credentials, 53% was personal and 12% was internal. According to Verizon’s findings, nearly 100% of the attacks were the result of hacking and nearly 100% of them attacked servers, mainly web and email.
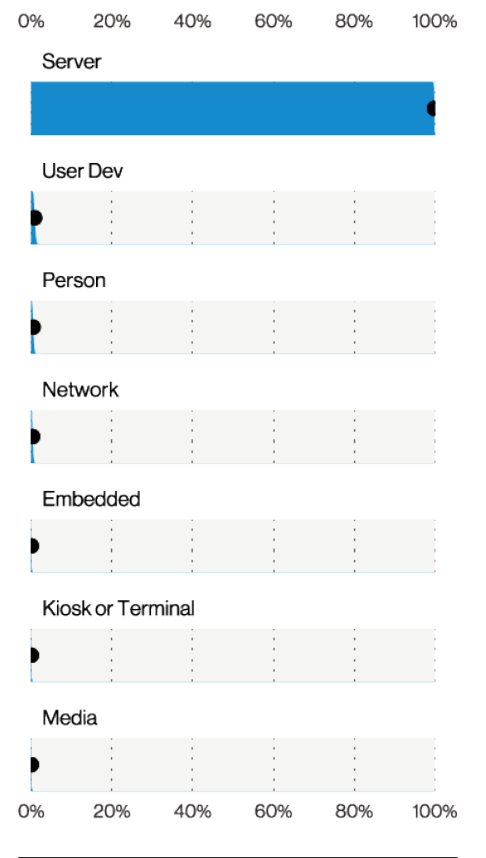
Assets in Basic Web Application Attacks breaches (n=1,369), Verizon 2021 Data Breach Investigations Report
Verizon estimates that “Brute force and credential stuffing attacks are extremely prevalent according to SIEM data analyzed in our dataset. We found that 23% of the organizations monitored had security events related to those types of attacks, with 95% of them getting between 637 and 3.3 billion(!) attempts against them.” Notably, these attacks “do not happen all at the same time, or even with any predictable regularity.”
In addition, in approximately 70% of cases, the attack was used for repurposing the web app for malware distribution.
How a cloud security solution can help prevent basic web application attacks
In 2019, Capital One was breached in one of the largest breaches to hit a financial firm. The attacker was able to access Capital One servers through a misconfigured web application firewall, which eventually gave the attacker access to hundreds of thousands of social security numbers, insurance numbers and bank account numbers.
With web servers as the main target asset in such attacks, it is essential to limit the permissions they have and detect any anomalous behavior pertaining to them. An identity-centric cloud security solution that monitors access risk for both human and service identities can help do this and prevent any obtained data from being repurposed for malware distribution.
Industries: What to look out for
In addition to incidents and breaches, Verizon provides insights into the attacks that are unique per industry. You can use this information to increase your awareness towards which security controls and measures you should prioritize in your annual planning as well as your day to day. Here are a few of the industries the Verizon report covers:
Financial and insurance
In the financial sector, Verizon found 721 attacks, at least 467 of which had confirmed data disclosure. Of these breaches, 81% were caused by miscellaneous errors, basic web application attacks and social engineering. Of the data that was compromised, 32% was credentials.
To deal with these threats, the top recommended CIS guidance is to enforce these following Implementation Group 1 (IG1) protective controls:
- Security awareness and skills training
- Secure configuration of enterprise assets and software
- Access control management
Healthcare
A change has occurred in the healthcare sector, per Verizon’s information: “Since 2019, the Healthcare sector has seen a shift from breaches caused by Internal actors to primarily External actors. This brings this vertical in line with the long-term trend seen by the other industries.”
Most of these attacks were caused by miscellaneous errors, basic web application attacks and system intrusion. Out of 655 attacks, 472 had confirmed data disclosure and it seems like ransomware was a “favored tactic.”
The top recommended CIS IG1 protective controls for addressing these threats are, again:
- Security awareness and skills training
- Secure configuration of enterprise assets and software
- Access control management
Information
In 2021, Verizon analyzed 2,935 incidents, 381 with confirmed data disclosure, that the information industry suffered from. Of these breaches, 83% were caused by miscellaneous errors, basic web application attacks and system intrusion. In addition, “misconfigurations accounted for over 70% of all errors in this industry.” Approximately 10% of these errors were due to misdeliveries, another ~10% due to programming errors, and yet another ~10% due to publishing errors.
According to Verizon “With this combination, it shouldn’t be a surprise that System Engineers [or are they called DevOps 24/7 Super Engineers?] had a strong showing in terms of the Internal actors responsible for those breaches. While the overall percentage of Error breaches hasn’t increased over the last few years, it remains a persistent issue facing organizations in this sector.”
The top recommended CIS IG1 protective controls are:
- Security awareness and skills training
- Secure configuration of enterprise assets and software
- Access control management
Mining, quarrying, oil & gas, utilities
Social engineering attacks were prominent in these critical infrastructure industries. Out of 546 incidents, 355 were with confirmed data disclosure. “Social Engineering accounts for 86% of the breaches in this vertical, followed by System Intrusions and Basic Web Application Attacks.The next most common type of attack is Ransomware, which accounts for 44% of non-Social Engineering attacks in this industry.” The most common type of data compromised was credentials.
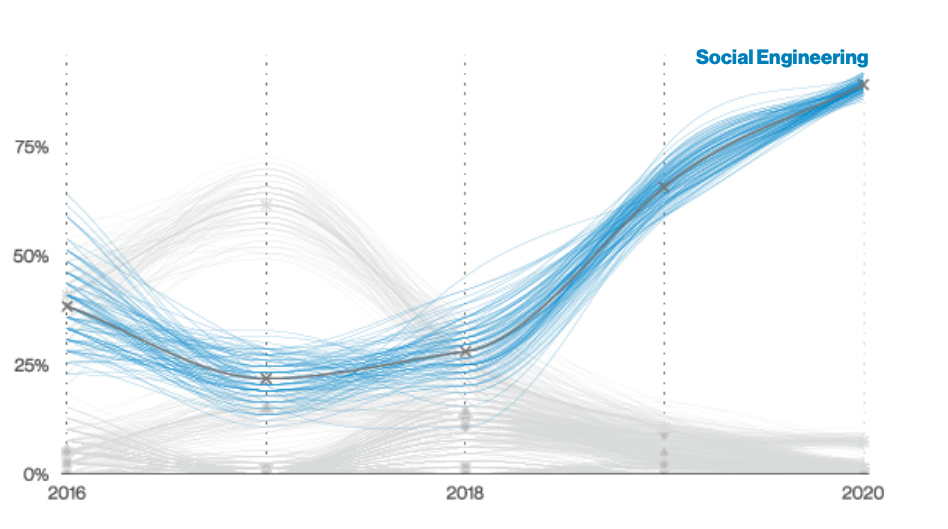
Pattern in mining and utilities incidents over time, Verizon 2021 Data Breach Investigations Report
The recommended CIS IG1 protective controls are:
- Security awareness and skills training
- Access control management
- Account management
Public administration
The public administration sector was also victim to a large percentage of social engineering attacks — 69% to be exact. Approximately 15% were caused by miscellaneous errors — usually misconfigurations and misdeliveries, and approximately 10% were due to system intrusion. Of the data that was compromised, 80% was credentials.
The top recommended CIS IG1 protective controls are:
- Security awareness and skills training
- Access control management
- Account management
Conclusion
A comprehensive cloud security solution reduces the risk from the Verizon-reported threat vectors featured here by reducing access to sensitive data. It does so by enabling — among other things — contextual visibility, risk assessment, prioritization and remediation, and anomaly detection and compliance. The most effective solution for addressing these kinds of threat vectors is one with an identity-centric approach in that it reveals and eliminates toxic scenarios of identity, network and resource configuration that put the data at risk.
Armed with such capabilities, security teams can proactively reduce their cloud’s attack surface, detect threats and reduce the blast radius from lateral movement in the event of a breach. At its core, such a solution enables the enforcement of least privilege principles and zero trust strategies across one’s cloud environment.
With successful operationalization, a solution can automate risk reduction at scale and in multi-cloud environments, and make security collaboration easier across the organizations — including with engineering teams.
As the Verizon report shows, risk will always be out there and, try as they might, security teams cannot seal off their environment from every possible risk. Humans are vulnerable because we are, well, human. The right technology can step in to lend a hand.
* All quotations and images are sourced from Verizon 2021 Data Breach Investigations Report.
- Cloud

