Enforce least privilege with Just-in-Time access
You now have the ability to grant privileged access only when needed and set time limits for access. Provide speedy access approvals — while minimizing your cloud attack surface and preventing standing privileges.
Balance access and risk
Minimize the risk of attackers exploiting excessive privileges by granting access only when there's a clear business justification and only for a short period of time.

Limit exposures with
just-in-time access
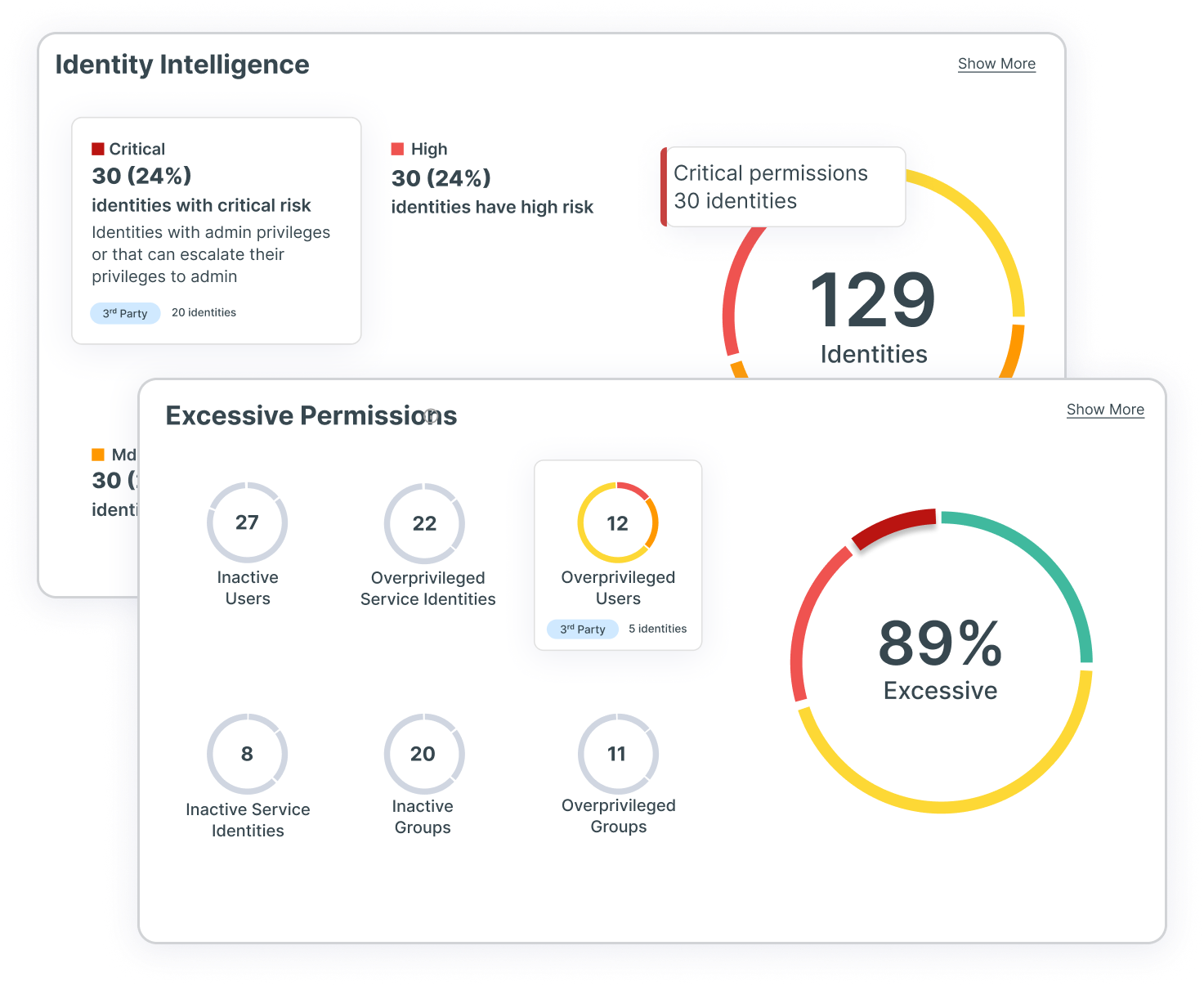
Gain identity–driven insights for full–stack risk assessment
With leading CIEM capabilities providing full multi-cloud visibility into identities and permissions, your security team can ensure users have only the right access to the right resources at the right time — and for the right reasons. Benefit from full-stack analysis that evaluates cloud provider permission models across identity, network, compute and data resources to surface precise findings in context. With Tenable Cloud Security, your teams gain insight into identity-related risk, including excessive permissions, network exposure and hidden dangers.
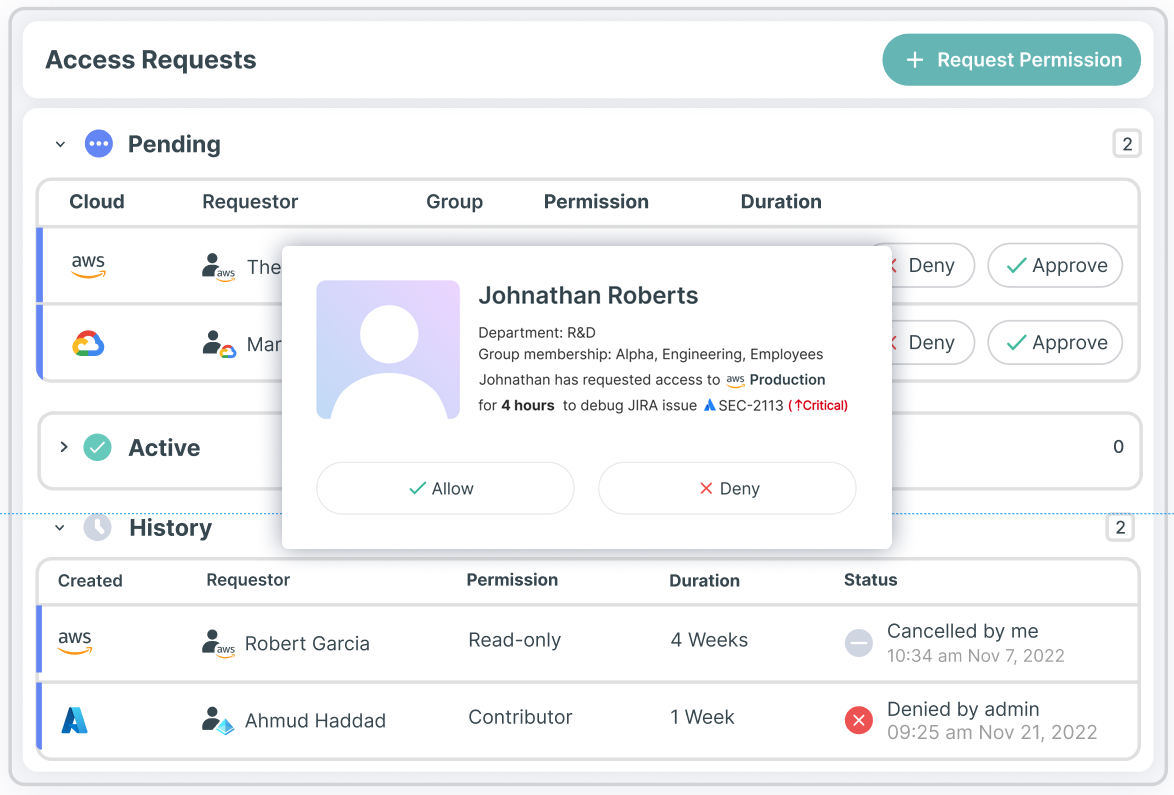
Work faster and more securely with JIT self–service workflows
Drive self-service workflows with Tenable Cloud Security’s JIT portal and empower your engineering teams to easily request and gain authorized access to required resources. Improve your multi-cloud security posture with continuous compliance monitoring. Maintain an audit trail and investigate access-related activity, including:
- Who had access
- What they accessed
- When they accessed
- Which actions they performed
- Who recived elevated permissions (and when they did so)
- The business justification
- The approver
Leverage JIT security for continuous audit and access governance
使用內建報告,您的團隊可以與利害關係人就內部合規性、外部稽核和日常安全活動進行溝通,包括提升權限期間的使用者活動、過去的請求和底層授權流程。
- Demonstrate your ability to meet key data privacy mandates including PCI-DSS, GDPR, HIPAA and more
- Produce extensive reports for internal compliance, external audit and daily security activities
- Reduce response and investigation time in the event of a security incident
Get Just-in-Time access with Tenable Cloud Security
深入瞭解 Tenable Cloud Security
使用 [Tenable Cloud Security] 的自動化功能,讓我們免除了讓人筋疲力竭的手動流程,並且在幾分鐘內執行過去可能需要 2 或 3 位安全人員好幾個月時間才能完成的工作。
- Tenable Cloud Security