利用涵蓋多重雲端環境的能見度杜絕您的雲端曝險
洞悉 您的雲端資源
利用深入存取與曝險路徑的情境式能見度,發現雲端中的運算、身分和資料資產。
辨識 重大雲端風險
取得背景資訊,以便排定來自雲端錯誤設定、多餘存取權限、弱點和暴露的敏感資料帶來的風險之優先順序。
消除 雲端曝險
快速且精準地消除主要曝險,進而迅速降低雲端風險,即使時間有限。
取得完整的雲端生命週期能見度
統一程式碼、雲端和執行階段的能見度,以辨識和排定來自金鑰、錯誤設定、弱點和身分問題的風險之優先順序。 利用 Tenable Cloud Security 內建的雲端基礎架構和權限管理 (CIEM),您的應用程式安全和安全營運團隊就可以從基礎架構即程式碼 (IaC) 到生產環境之間強制執行最低特權原則並更快速地修補。

完備的資產庫
動態攻擊路徑對應
Predictive Prioritization (預測性優先排序)
動員與修復
進階分析與報告

利用生成式 AI 找出您環境中隱藏的風險,並且強化安全專業能力,進而加速搜尋、深入解析和行動。
取得統一的檢視方式,查看您所有資產和整個攻擊破綻 (包含:未發現的資產、IT、OT、IoT、雲端、身分和應用程式) 的風險。
透過跨網域關係的視覺化來瞭解攻擊者的存取能力,因此您就能封鎖最關鍵的攻擊路徑。
將您的心力專注於最重要的事,也就是:攻擊者最有可能刺探利用的重大曝險。
利用可簡化修復工作的自動化工作流程與建議指引加速應變。
利用與業務目標一致的檢視方式簡化網路曝險的衡量與溝通工作,將決策和投資最佳化。
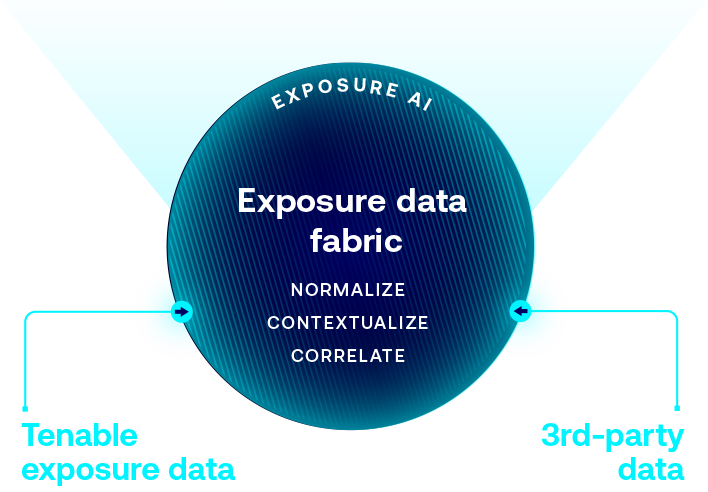
充分運用全球規模最大的資產、曝險和威脅背景資訊存放庫,該存放庫也是 ExposureAI 無與倫比深入解析的後盾。
整理資料,以減少重複性,並改善完整性、一致性和效率。
以更多的深入解析豐富資料,使資料更能據以行動且實用。
判別對核心業務服務和功能的關鍵關係背景資訊,並使之浮出檯面。
將安全性嵌入軟體開發生命週期 (SDLC) 中的每一個階段,確保安全地開發與維護程式碼、IaC、容器和 API
消弭各自為政的 DevOps 和 SecOps 之間的鴻溝,已獲得開發生命週期本身的作業能見度和資安事端應變能力。
在所有動態、暫時性的雲端資產中,找出並修復錯誤設定、身分誤用以及工作負載攻擊程式
Gain complete cloud lifecycle visibility
透過對應從 IaC 到執行階段環境的風險,並掃描像是 Terraform 和 CloudFormation 等 IaC 範本,獲得您軟體開發生命週期中的全方位能見度。
深入瞭解識別並保護 AI 工作負載
利用以下全都整合在統一的雲端安全平台中的功能,包括:人工智慧安全態勢管理 (AI-SPM)、資料安全態勢管理 (DSPM)、最低特權存取和 just-in-time (JIT) 權限,自動搜尋和分類環境中的 AI 資產,例如模型、訓練資料和推理端點。
深入瞭解常見問題
什麼是 Tenable Cloud Security?
-
Tenable Cloud Security 是一套完全整合的雲端基礎架構安全解決方案,結合了功能強大的雲端安全態勢管理 (CSPM) 和雲端安全工作負載保護 (CWP) 功能,以及業界最佳的雲端基礎架構權限管理 (CIEM)、雲端偵測與應變 (CDR) 技術、和高度創新的基礎架構即程式碼 (IaC) 安全性與 Kubernetes 安全態勢管理 (KSPM) 解決方案。雲端原生應用程式保護平台 (CNAPP) 能管理您的多重雲端資產庫、在整個架構中強制執行預防性的安全原則 (解決身分、網路、資料和運算風險)、偵測與應變發生中的威脅、提早執行安全作業、並且透過 IaC、CI/CD 或執行階段環境自動修復風險。這些功能可讓企業對比安全標準進行指標分析,並推動整個企業的合規工作強制執行。
Tenable Cloud Security 如何定價與授權?
-
Tenable Cloud Security 包括所有的 CNAPP 元件,能夠以獨立產品購買或作為 Tenable One 產品的一部分取得。獨立產品的定價方式是根據可計費資源的數量來計算。大量購買折扣則會根據預估的每月使用總量計算。同樣地,在作為 Tenable One 產品一部分的定價方式上,基本定價方式是根據所有可計費資源的數量來計算。然後採用 Tenable One 中的比例來定價雲端資源,並使用現有 Tenable One 授權下訂閱的總資產數量來套用大量折扣。Just-in-time (JIT) 存取會分開授權,並且可以新增至獨立產品或作為 Tenable One 的一部分的產品定價中。針對特供的定價方式資訊與問題,歡迎洽詢 Tenable 業務代表。
我可以在何處取得 Tenable Cloud Security 的技術說明文件和版本資訊?
-
有關 Tenable 產品技術說明文件,請造訪:https://docs.tenable.com。您必須登入您的 Tenable Cloud Security 帳戶,才能查看版本資訊與說明文件。請洽詢 Tenable 業務代表,取得技術說明文件和版本資訊的存取權。
Tenable Cloud Security 和 Tenable One 的差別是什麼?
-
Tenable Cloud Security 可以以獨立產品或作為 Tenable One 曝險管理平台的一部分購買。在與 Tenable One 結合時,Tenable Cloud Security 可提供您整個 IT 環境 (包含傳統網路、內部部署伺服器、操作技術和公用雲端) 的全方位檢視方式。透過購買作為 Tenable One 一部分的 Tenable Cloud Security,企業就能將他們所購買的 Tenable 產品合併在單一合約當中,並取得更多功能,例如曝險觀點 (exposure views)。
Tenable Cloud Security 能夠與哪些雲端及雲端原生工具整合?
-
除了一些雲端供應商服務,例如:AWS Control Tower 和 Entra ID 外,Tenable Cloud Security 也與所有主要的雲端供應商整合,包括:AWS、Azure 和 GCP。將 Tenable Cloud Security 與您的工單、通知和 SIEM 工具整合,以支援工單的建立和推送通知的傳送,然後運用標準通訊工具 (例如:Jira、Slack、Microsoft Teams 和電子郵件整合工具) 在您的企業中擴充工具。
Tenable Cloud Security 支援哪些身分提供者?
-
Tenable Cloud Security 能夠與多種 IdP 整合,包括:Entra ID、Google Workspace、Okta、OneLogin 和 Ping Identity。這些 IdP 整合功能可顯示與您雲端帳戶相關聯的同盟使用者和群組的完整資產庫,並提供權限分析與身分情報。
Tenable Cloud Security 如何保護我的資料?
-
Tenable 能確保您工作負載的安全性,採用可靠的加密及存取控制機制,以保護敏感資料。它能控管多餘的特權,以及許可長時間存在的存取權限。Tenable 能在發生資料外洩事件時,透過減少影響範圍來保護您的敏感資料。如需有關 Tenable Cloud Security 如何確保您獨特的雲端環境之資料保護及隱私的更多資訊,請洽詢您的 Tenable 業務代表。
我可以在不涉及第三方的情況下使用 Tenable Cloud Security 嗎?
-
可以的。 Tenable Cloud Security 使用者可以購買帳戶內的掃描功能,做為其環境的附加元件。該功能支援企業現場掃描工作負載,不受狹隘的資料隱私權標準和法規拘束。帳戶內掃描會在您的雲端帳戶內執行,因此資料不會離開該環境。
我要如何購買 Tenable Cloud Security?
-
如需購買 Tenable Cloud Security,您可以與您當地的認證合作夥伴配合,或洽詢您的 Tenable 業務代表。點擊此處申請 Tenable Cloud Security 產品示範。
相關資源
深入瞭解 Tenable Cloud Security
使用 [Tenable Cloud Security] 的自動化功能,讓我們免除了讓人筋疲力竭的手動流程,並且在幾分鐘內執行過去可能需要 2 或 3 位安全人員好幾個月時間才能完成的工作。
- Tenable Cloud Security