Discover, prioritize, and remediate vulnerabilities, misconfigurations, identity,
and
data risks, across
multi-cloud environments.
-
Cloud-Native Vulnerability Mgmt. Get prioritized visibility into every cloud resource
from development to runtime. -
强制实施最小特权。 Leverage the intuitive UI to attain the least privilege without disrupting productivity.
-
Automate Compliance. Eliminate audit fire drills. Verify and automatically
report on compliance frameworks.
申請 Tenable Cloud Security 示範
領先群倫的統一雲端安全正在等著您!
We'll show you exactly how Tenable Cloud Security helps you deliver
multi-cloud asset discovery, prioritized risk assessments and
automated compliance/audit
reports.
Join 40,000+ organizations automating their cloud security with the leading independent provider


滿足企業特有需求的雲端安全之路
Get full visibility across AWS, Azure, GCP, and Oracle Cloud Infrastructure (OCI) with 100% agentless scanning. 持续探索您的云环境,涵盖基础设施、工作负载、身份和数据,以强大的可视化功能呈现您所有的云资产。Obtain a unified view that simplifies your team’s understanding of even the most complex issues.
Try for free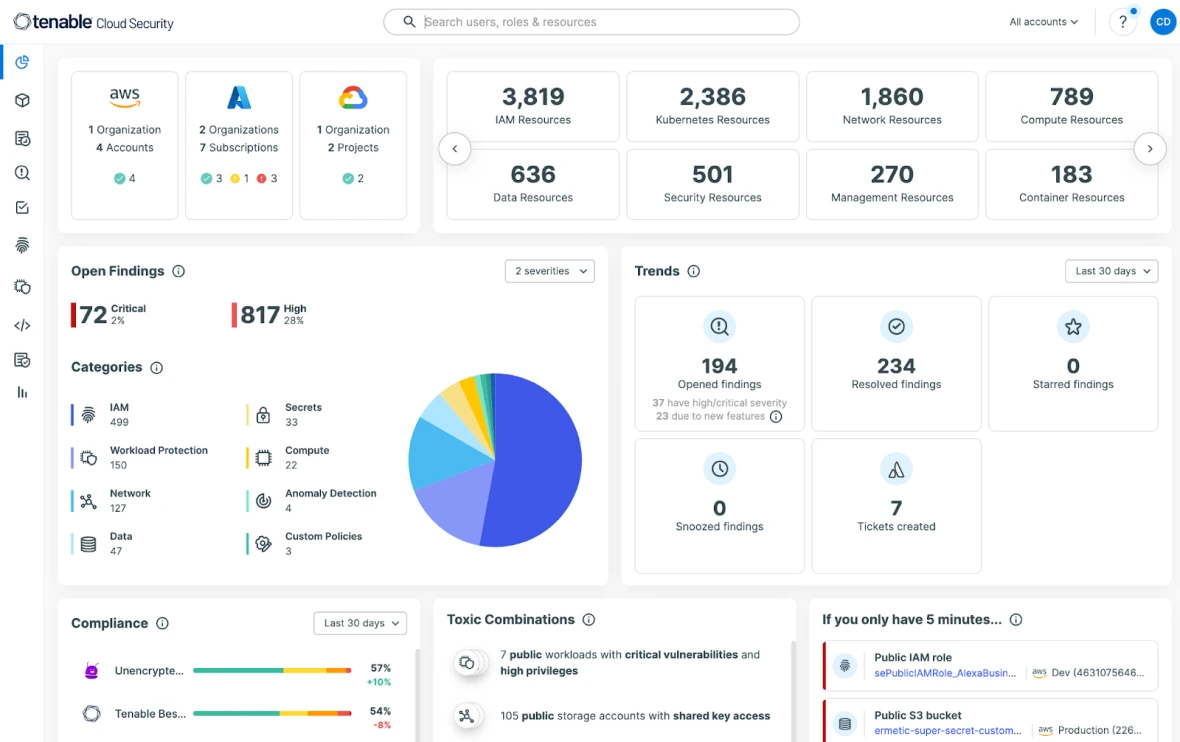
透過持續檢討和評估雲端環境的設定和組態來監控風險。By mapping discovered risks against security standards and policies, you can attain and maintain compliance and easily address audits across multi-cloud environments. Take advantage of pre-built reporting for 20+ compliance frameworks including SOC-2, GDPR, PCI DSS, HIPAA, NYDFS, and others.
Try for free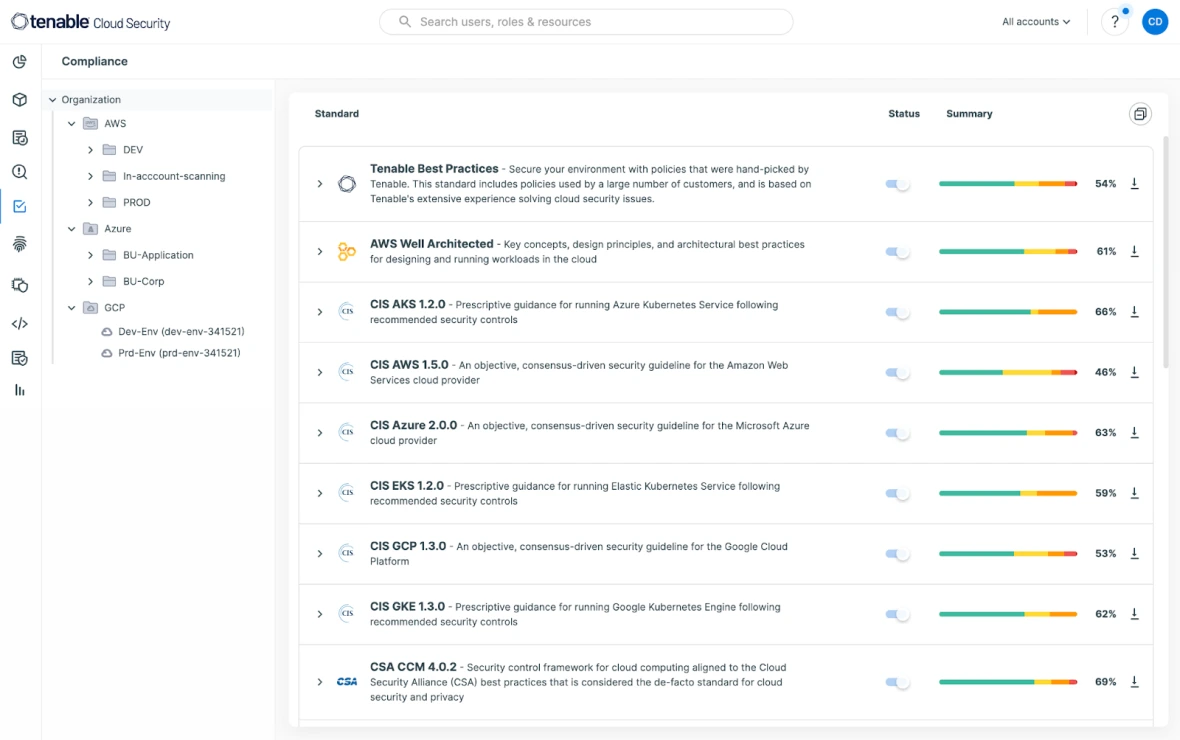
Tenable is a cloud security solution that allows you to focus on the risks that matter most. Tenable Cloud Security gives users deeply prioritized findings that empower Security and DevSecOps teams to automate threat detection and remediation efforts at scale. Mitigate and remediate risky privileges and faulty configurations using auto-generated and customizable policies by seamlessly integrating across ticketing, CI/CD pipelines, IaC, and other workflows.
Try for free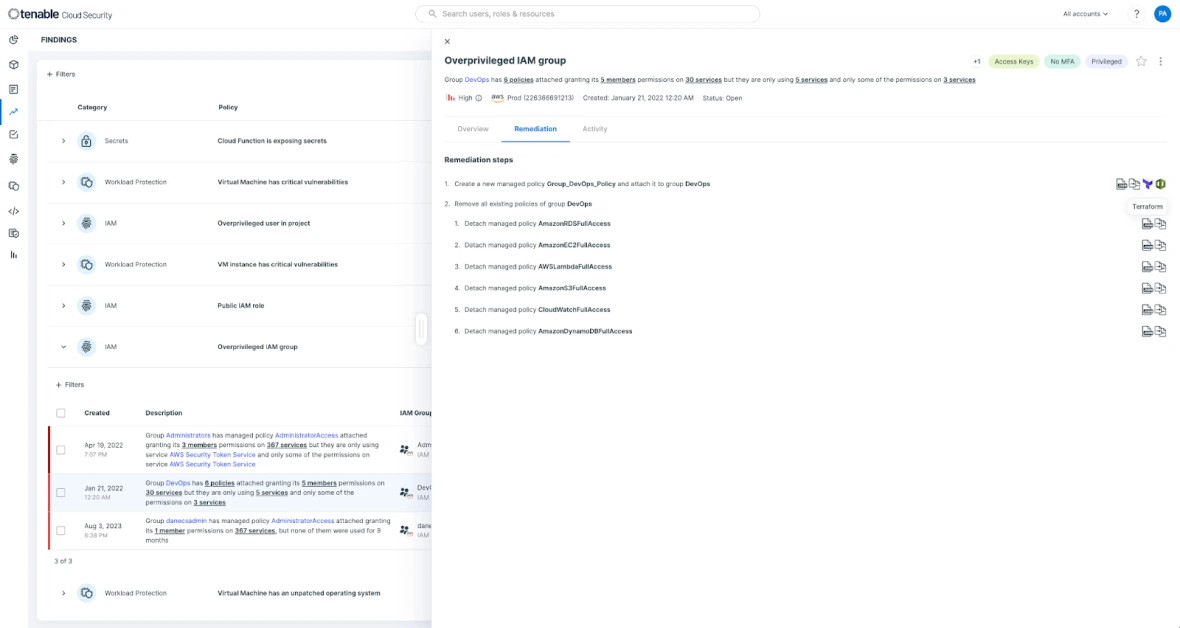
根据行为基准持续评估风险,从而帮助您识别异常和可疑活动。Analyze cloud provider logs and link cloud threats with underlying architecture to show the context associated with each risk quickly.
Try for free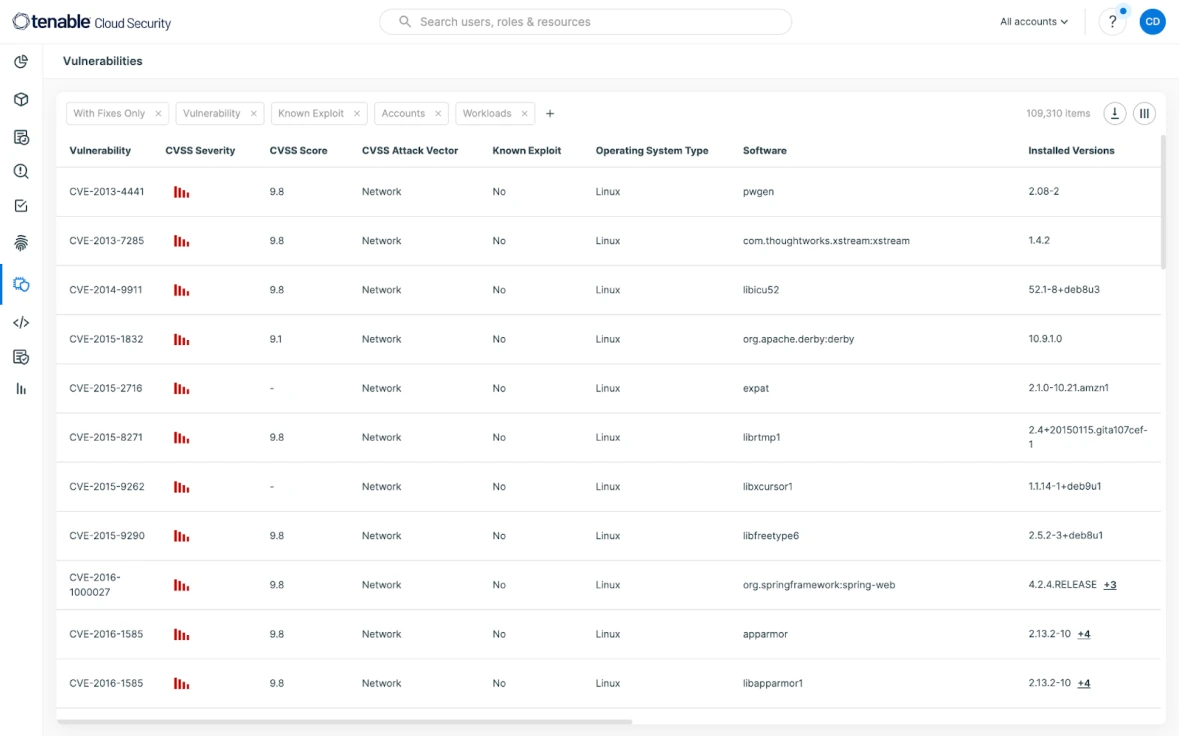
Build zero trust in your cloud security infrastructure. 在不妨碍任何工作的情况下,最大限度地减少服务和人员的过度权限。实现最小权限的第一步是全面、准确地了解所有授权。Continuously discover all entities and policies (including IAM, resource, permissions boundaries, and ACLs) in the environment and analyze the relationships to reveal the gap between desired enterprise policy and actual entitlements.
Try for free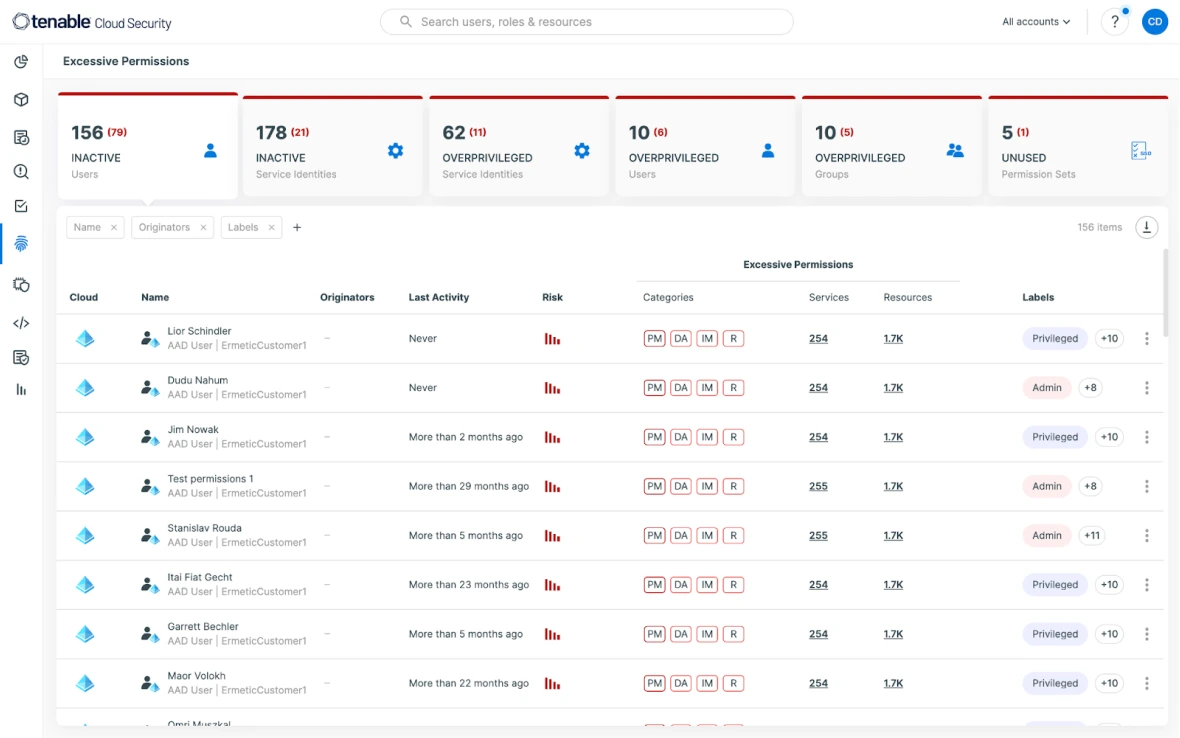









Read the eBook for insight into:
- How to protect workloads and manage vulnerabilities
- Securing identities and entitlements and enforcing least privilege
- Ways to accelerate cloud detection and response
- How to assess and prioritize risk across cloud environments




