Fortify your security posture with Tenable OT Security
Vulnerability Management. Scan your IT, OT, and IoT assets for 79,000+ vulnerabilities. Detect cyber threats, malicious insiders, and more.
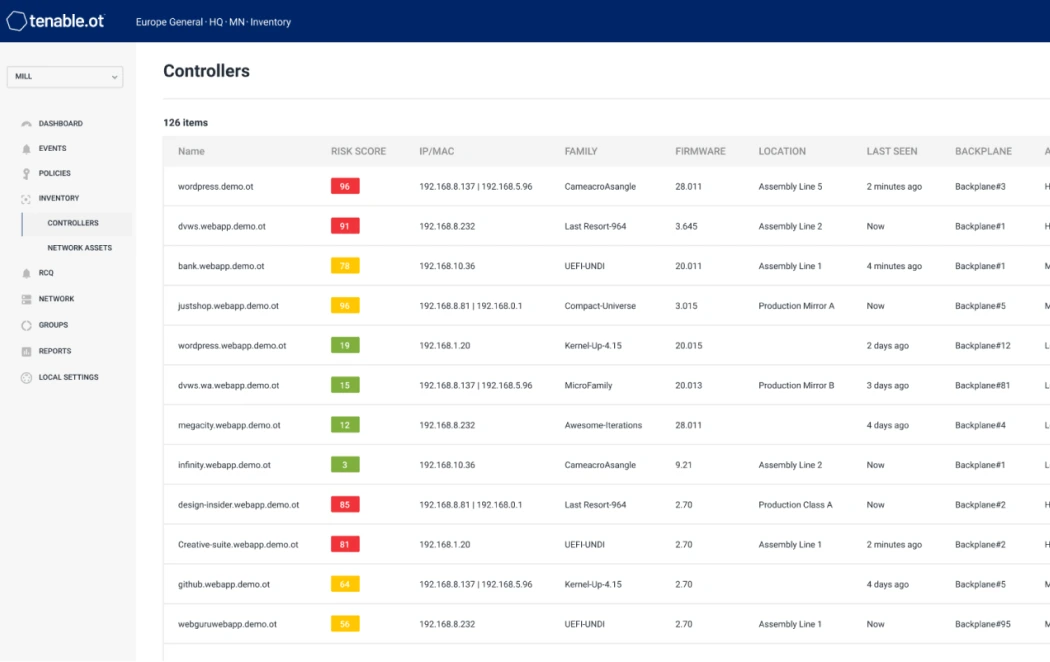
OT Scanning. Maximize your operational environment’s visibility, security, and control for SCADA systems, PLCs, DCS, IED, HMIs, and other assets across IT, OT, and IoT.
Reporting and Risk Intelligence. Access proven security tools and reporting capabilities for IT and OT teams, providing unmatched visibility into converged IT/OT segments and industrial networks in a single pane of glass.
申請示範
取得您所需要的操作技術安全性。
降低不必要的風險。
Vulnerability Management. Scan your IT, OT, and IoT assets for 79,000+ vulnerabilities. Detect cyber threats, malicious insiders, and more.
OT Scanning. Maximize your operational environment’s visibility, security, and control for SCADA systems, PLCs, DCS, IED, HMIs, and other assets across IT, OT, and IoT.
Reporting and Risk Intelligence. Access proven security tools and reporting capabilities for IT and OT teams, providing unmatched visibility into converged IT/OT segments and industrial networks in a single pane of glass.
Tenable 保護了超過 44,000 家客戶和 65% 的財星 500 大企業

1,000 萬元以上
與工廠關閉有關的單日停機時間成本。
不到 5%
的 OT 專業人士表示,自己對公司保護工業物聯網裝置和系統的能力有信心。
Why choose Tenable OT Security?
Access market-leading OT vulnerability management capabilities,
purpose-built to help
secure your operations

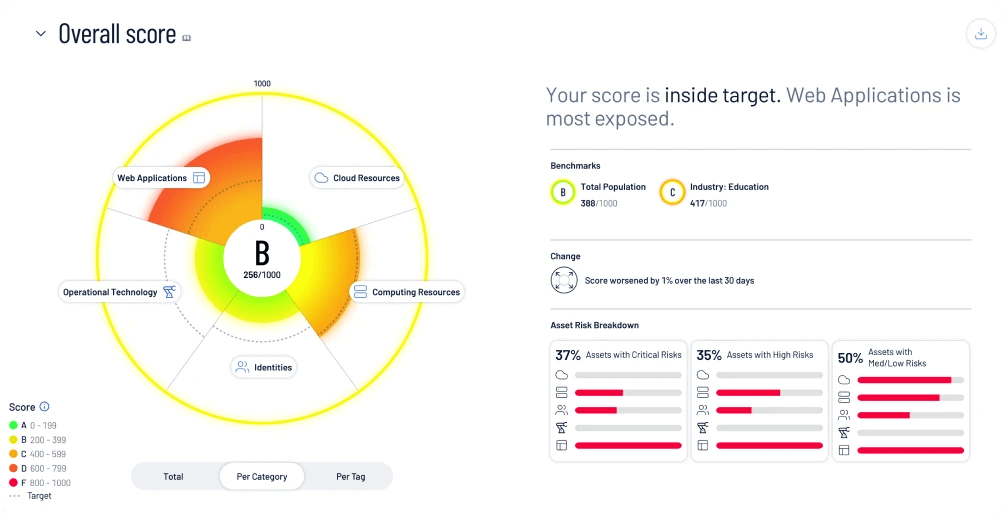
Get complete visibility across your entire attack surface

自動化
Ecosystem integration
Tenable OT Security integrates with leading Access Control Systems, SIEM, SOAR, next generation firewalls and diode based firewalls in order to provide insights to personnel outside of OT specific titles. Tenable OT Security also works in cooperation with the larger Tenable product portfolio including Tenable Security Center, Tenable Vulnerability Management and Tenable Identity Exposure.


Tenable OT Security also works in cooperation with the broader Tenable One portfolio, including Tenable Security Center, Tenable Vulnerability Management, and Tenable Identity Exposure.
主要特色








