by Stephanie Dunn
December 15, 2016
In order to gain a complete visibility into network activity, organizations must be able to collect and monitor event logs on a continual basis. Despite best efforts, many analysts struggle to find a balance in establishing effective audit policies that collect the right amount of information. Ineffective policies can allow attackers to infiltrate the network, exfiltrate confidential data, and persist for long periods of time. Deploying effective audit policies is essential in establishing accurate audit trails and provide valuable forensic evidence. This dashboard covers key concepts within the ITSG-33 guide that will assist organizations in monitoring malicious activity, track vulnerabilities, and strengthen existing policies.
The Communications Security Establishment Canada (CSEC) developed a series of guidelines for security practitioners in managing information technology (IT) security risks for Government of Canada (GC) information systems. The Information Technology Security Guidance Publication 33 (ITSG-33), IT Security Risk Management: A Lifecycle Approach provides a comprehensive set of security controls that can be used to support a wide variety of business requirements. To support interoperability needs, the ITSG-33 guide is consistent with controls published in the U.S. National Institute of Standards and Technology (NIST) Special Publication 800-53. Data presented within this dashboard aligns with ITSG-33 security controls that support continuous monitoring efforts, monitoring network traffic, and auditing information systems. This dashboard aligns with the following controls:
- Continuous Monitoring (CA-7)
- Information Systems Monitoring (SI-4)
- Audit and Accountability (AU-Family)
Implementing a continuous monitoring strategy involves establishing policies and procedures to monitor network traffic, remediate vulnerabilities in a timely manner, and configure audit policies to monitor internal systems. Log data provides a wealth of information that can be used to track issues with user behavior, detecting suspicious activity, and identifying changes to network assets. Security teams can use log data to assist with incident response efforts, and correlate how a system may have been compromised. Routine vulnerability scans should also be performed as a part of a continuous monitoring strategy.
Information presented within this dashboard will assist organizations in monitoring event logs, enhance existing audit policies, and improve overall response efforts. Analysts will obtain an accurate look into the overall attack surface, and have actionable intelligence needed to improve the organization’s security posture. Using information collected from the Tenable Log Correlation Engine (LCE), analysts will be able to monitor patch management efforts, track vulnerable hosts, and detect malicious services in use. Audit checks are performed to identify audit policies or security controls that should be addressed by security teams. Log data collected from sensors across the network will help analysts to determine if event logs are being captured.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.4.1
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.0
Tenable's Tenable.sc Continuous View (CV) will provide continuous visibility enabling organizations to take decisive actions to secure the enterprise. Tenable.sc CV is continuously updated to detect advanced threats and vulnerabilities. Active scanning periodically examines systems to determine vulnerabilities and compliance concerns on network assets. Passive listening provides real-time discovery of vulnerabilities on transient mobile, virtual, and cloud services. Host data and data from other security products is analyzed to monitor the network for malware, intrusions, and other forms of malicious activity. Using Tenable.sc CV, organizations will obtain the most comprehensive view of the network and the intelligence needed to support proactive continuous monitoring efforts.
The following components are included within this dashboard:
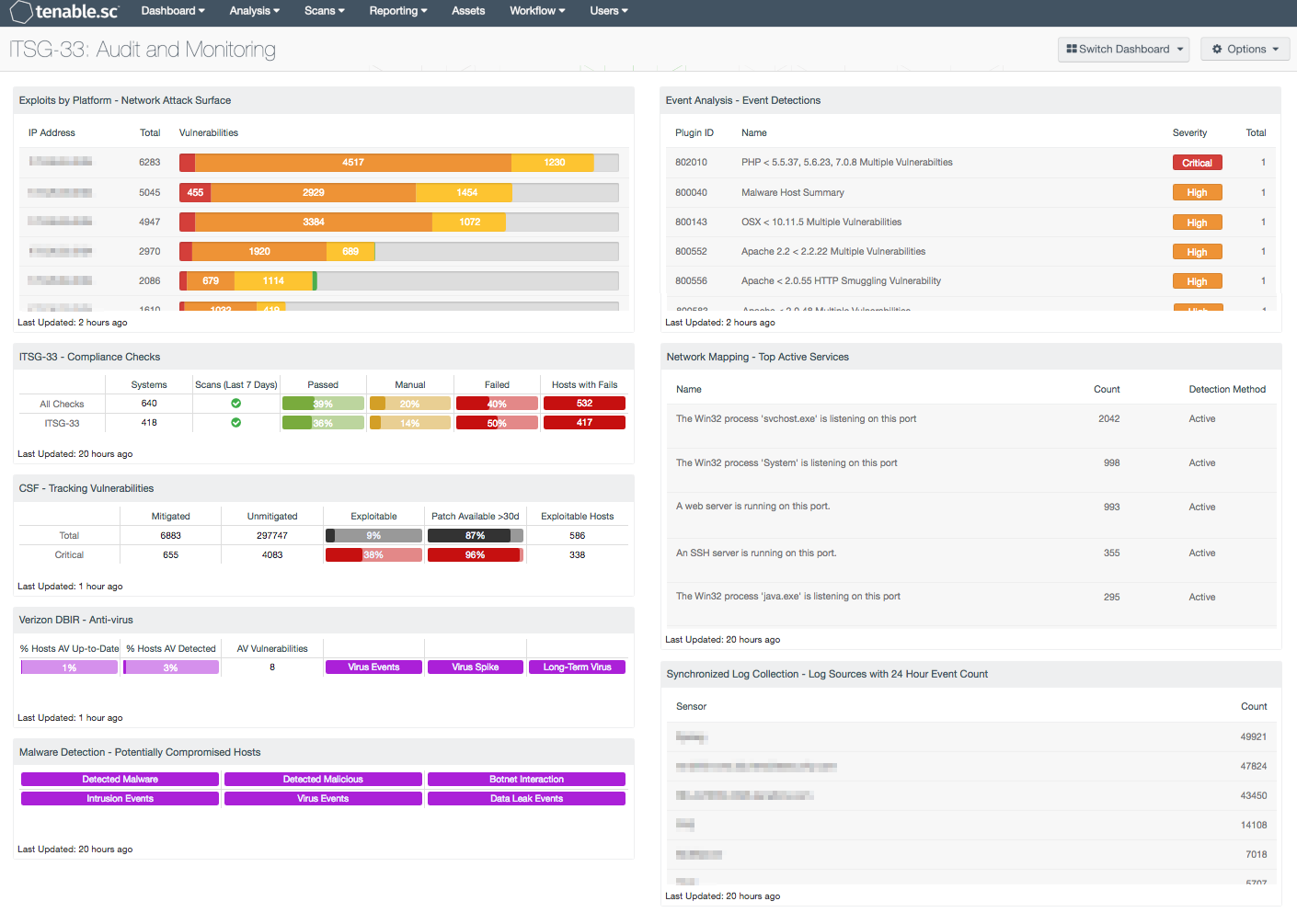
- Exploits By Platform - Network Attack Surface: The Network Attack Surface table lists the most exploitable subnets by vulnerability score. The table is filtered for exploitable vulnerabilities and includes the IP range, total vulnerability count, and a bar chart of vulnerabilities by severity. Security analysts can use this table to identify the most vulnerable subnets within the environment.
- ITSG-33 - Compliance Checks: This component presents the results of compliance audits to verify the security of the network, including those checks that reference the ITSG-33 standard. The top row presents all compliance checks, and the second row presents only those checks that reference the ITSG-33 standard. Each row includes the system count, whether scans were performed in the last seven days, and the percentage of checks that passed, failed, or require manual verification. Passed checks are displayed in green, failed checks are in red, and checks that require manual verification are in orange. The number of hosts with failed compliance checks is also shown.
- CSF - Tracking Vulnerabilities: Tenable.sc records when vulnerabilities are discovered, when patches are issued, and when vulnerabilities are mitigated. This component assists in tracking vulnerability mitigations. In the matrix, the top row is total vulnerabilities at all severity levels, and the row with red breaks out the critical severity vulnerabilities. The Mitigated column displays the number of vulnerabilities that have been moved to the mitigated database. A vulnerability is moved to the mitigated database when the vulnerability is no longer detected by a rescan; the vulnerability is assumed to be remediated. The Unmitigated column displays the number of current vulnerabilities that are not yet remediated and have not been moved to the mitigated database. The Exploitable column displays the percentage of those unmitigated vulnerabilities that are known to be exploitable. The Patch Available column displays the percentage of the unmitigated, exploitable vulnerabilities that have had a patch available for more than 30 days. Ideally, both of these percentages should be 0%, because all exploitable vulnerabilities and all vulnerabilities with patches available should have been mitigated already. The Exploitable Hosts column displays the number of hosts on the network that have unmitigated, exploitable vulnerabilities.
- Verizon DBIR – Anti-virus: This matrix assists the organization in monitoring anti-virus (AV) solutions. The "% Hosts AV Up-to-Date" column displays the percentage of total systems that have AV installed and working properly; the "% Hosts AV Detected" column displays the percentage of total systems on which AV has been detected, whether or not the AV is working properly. The "AV Vulnerabilities" column displays the number of detected vulnerabilities related to AV. The "Virus" indicator is highlighted purple if there were any AV events in the last 72 hours, while the "Virus Spike" indicator is highlighted purple if a large spike in virus activity was detected in the last 72 hours. The "Long-Term Virus" indicator is highlighted purple if in the last 72 hours an IP address has been the source of virus or malware events continuously for more than 20 minutes.
- Malware Detection – Potentially Compromised Hosts: This component presents indicators that highlight potentially compromised hosts. The top row of indicators highlight those hosts that have a high probability of being compromised, including hosts with detected malware infections, hosts with detected malicious activity, and hosts interacting with known bad IP addresses. The second row of indicators highlight hosts with suspicious activity that may indicate a compromise, including those hosts with intrusion events, virus events, and data leakage events. If an event or activity has been detected on a host, the indicator will turn purple. Analysts can drill down and obtain information on the hosts involved, event activity, and potential remediation solutions.
- Event Analysis – Event Detections: This table presents all detections from event plugins associated with the Tenable Log Correlation Engine (LCE). Many of these event plugins report detections of activity or activity summaries, and these can be further investigated as needed. Some of the event plugins report actual vulnerabilities based on the activity observed by LCE. The most severe detections are reported first in the list.
- Network Mapping – Top Active Services: This table enumerates the top services that were active and listening on the network. The table is sorted so that the services with the highest number of detections are at the top. To reduce the network attack surface, services that are not being used should be disabled. Any unauthorized services should be further investigated.
- Synchronized Log Collection – Log Sources with 24 Hours Event Count: This component identifies log sources and helps the organization ensure that all systems that can send logs are sending them to LCE and/or allowing NNM to scan them. Identifying patterns of suspicious behavior using NNM, and sending these logs to the LCE, will show correlated events across multiple workstations and servers. This practice enables investigation and auditing functions to be easier and more effective should an intrusion occur.